
The ONE!
One Schedule to Rule them All!
Welcome to the "One Schedule to Rule them All!". Thank you for your interest by using this. This is an attempt to make things easier for you, the DEF CON attendee, to figure out the when/what/where during the chaos of DEF CON 32.
It started out simple. I had a Kindle and wanted an ebook of the schedule so I didn't have to wear out the paper pamphlet by pulling it out after every talk to figure out where to go next. Back then there was only the main DEF CON tracks, not really any Villages, and production of the ebooks were easy. Over time the Village system developed with a resulting multiplication in complexity, both for attendees and for my production. The offerings no longer include epub and mobi formats and instead now include html, csv, PDF, ical, public Google calendar, and mysql dump format files. Hopefully you'll find something of use.
The intent is still to be a resource to answer the question at the end of an hour of "What's next?"
As a general rule I do not include:
- Off-site events
- Blatent vender pitch events
- Nonspecific timed events. Unfortunately this means the contests aren't on the regular schedule.
- DEF CON events are emphasized, so BSides Las Vegas and BlackHat tend to not show up
Be sure to check out the Links section at the bottom of this. Most all of the events listed here were derived from these links and a Infoboot data feed. There is much more going on at DEF CON than what is listed here.
Check out the Guides/Tips/FAQs links if you're new to Las Vegas.
Notable suggestions are:
- Bring comfortable shoes, you'll be doing a lot more walking than you expect
- Bring a water bottle to keep hydrated
- Beware of going out doors, there's nothing like LV sun and heat
- Everything in Las Vegas is a longer walk than you think
- Relax, don't try to see everything, you'll never be able to!
- Have FUN!
And finally, this is only as good as the ideas and information used to generate it.
I welcome your constructive suggestions and comments. Please send them to qumqats@outel.org
Have a good time at DEF CON 32!
Index of DEF CON 32 Activities
Maps List
Maps Browser
Detailed Village Info
Villages Table
Hour by Hour list of happenings, start at the top, or go to a specific day.
Schedule
- Thursday
- Friday
- Saturday
- Sunday
Sorted list of all the Speakers Names linked to their talk's description.
Speaker List
Sorted list of all the Talk's titles linked to the talk description.
Talk Title List
Talk lists for each Village, start at the alphabetic top, or go to a specific Village.
Village Talk List
ADV - AIV - AIxCC - APV - ASV - BBV - BHV - BICV - BTV - CHV - CLV - CON - CPV - DC - DCG - DCGVR - DDV - DL - ESV - HDA - HRV - ICSV - IOTV - LPV - MISC - PHV - PLV - PSV - PYV - QTV - RCV - RFV - RTV - SEV - SOC - TCV - TEV - VMV - WS - XRV
Descriptions and Info for all the talks.
Talk Descriptions
Contests Table
Contests
Demolabs Table
Demolabs
Workshops Table
Workshops
Paid Trainings Table
Paid Trainings
Parties, Gatherings, and Events Table
Parties Gatherings Events
DEF CON 32 Vendors
Vendors
DEF CON 32 Exhibitors
Exhibitors
DEF CON 32 Communities
Communities
The latest news from defcon.org
DEF CON News
The answer to your questsions about DEF CON overall and for this year.
DEF CON FAQ
DEF CON 32 FAQ
DEF CON .org Links
Combined Schedule Sources
Interesting Links
Guides/Tips/FAQs
Maps List
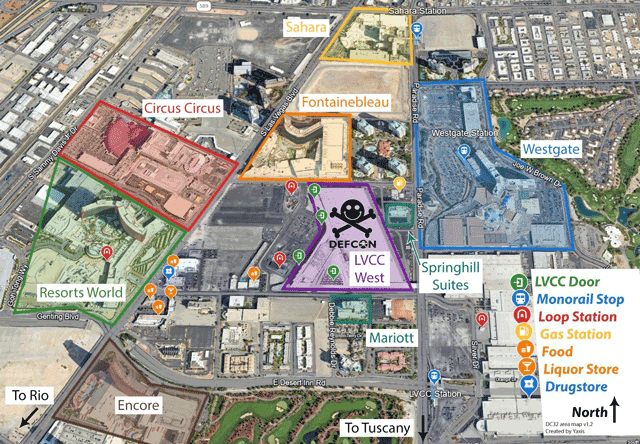
Overview of the area around DEF CON 32
Click on image to view full size
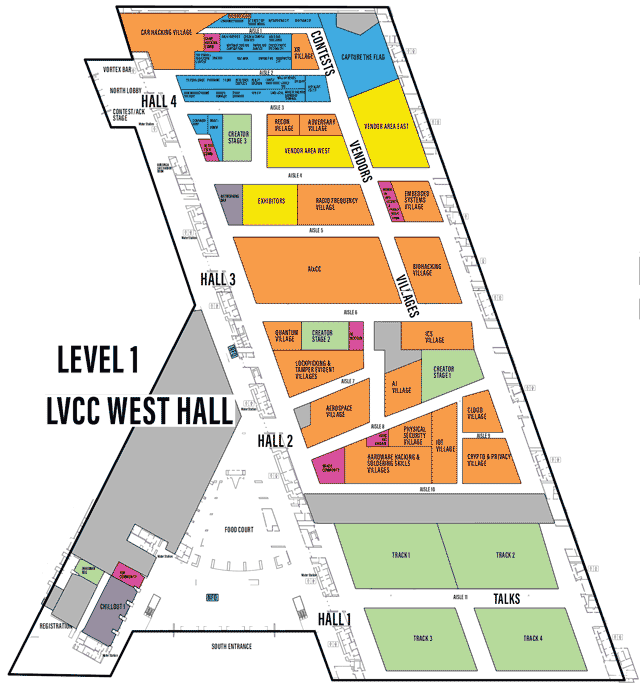
LVCCW Full map of Level 1
Click on image to view full size
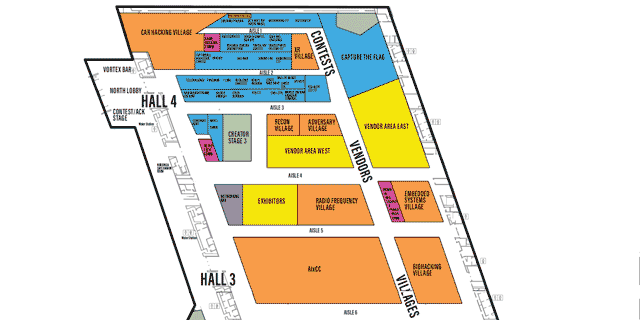
LVCCW map of North portion of Level 1
Click on image to view full size
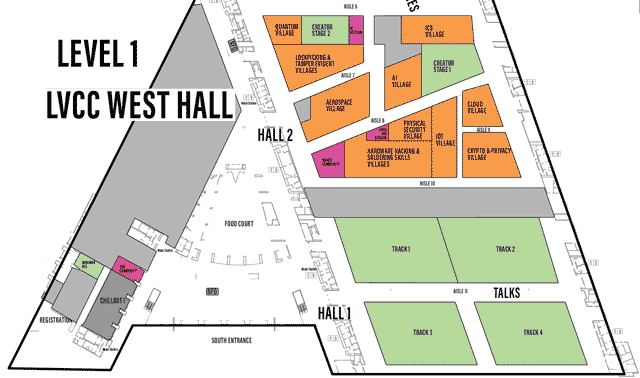
LVCCW map of South portion of Level 1
Click on image to view full size
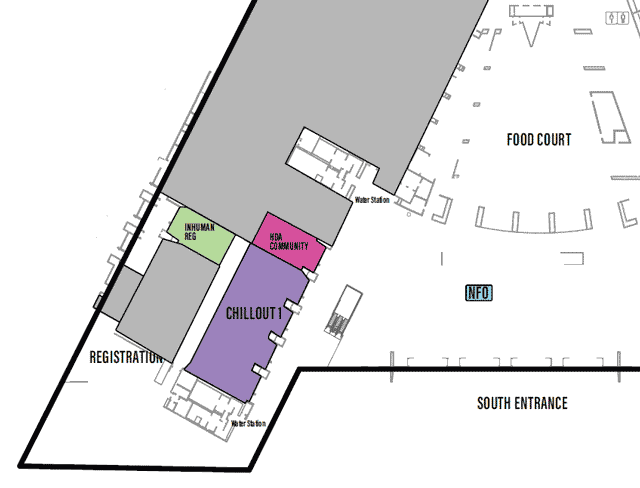
LVCCW map of South Lobby and Registration/HDA of Level 1
Click on image to view full size
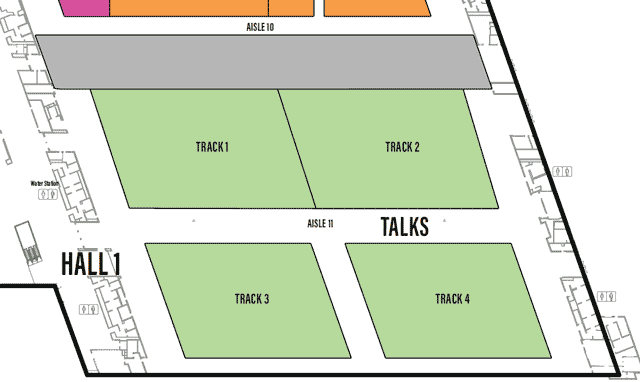
LVCCW map of Hall 1 of Level 1
Click on image to view full size
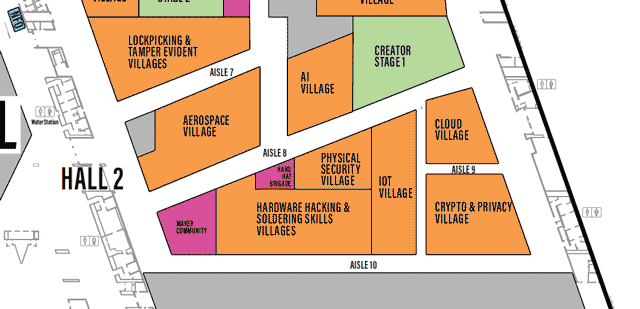
LVCCW map of Hall 2 of Level 1
Click on image to view full size
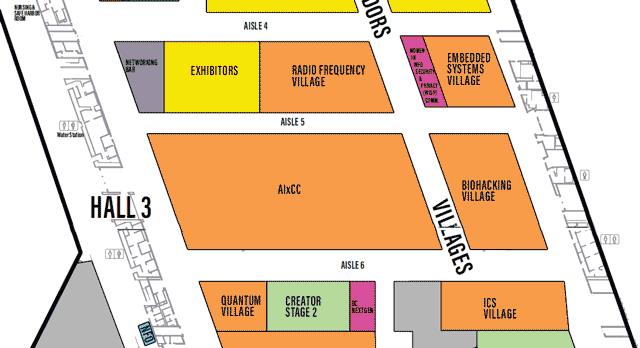
LVCCW map of Hall 3 of Level 1
Click on image to view full size
LVCCW map of Hall 4 of Level 1
Click on image to view full size
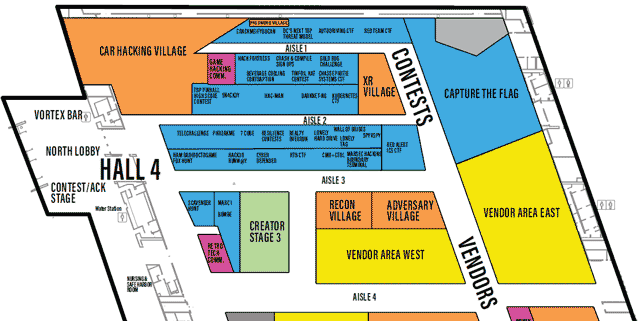
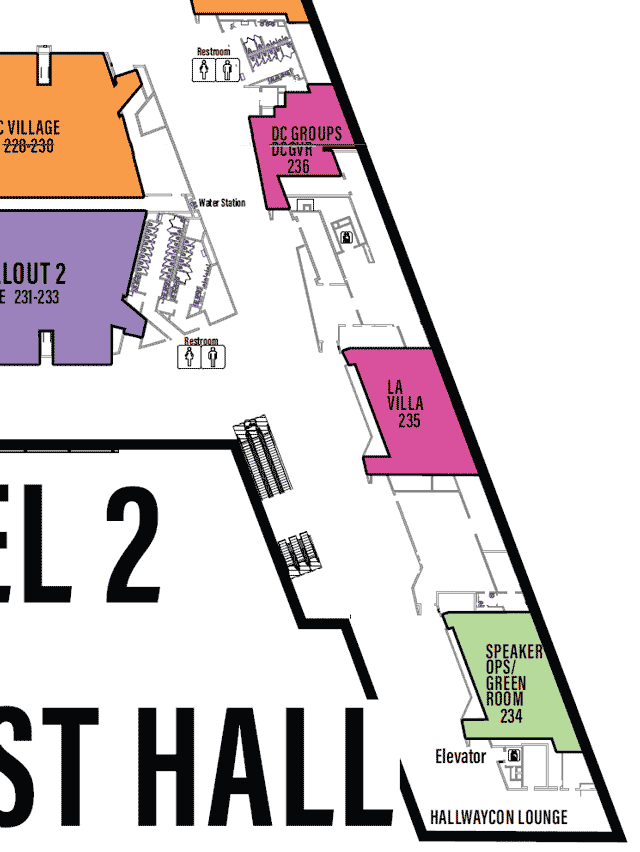
LVCCW Full map of Level 2
Click on image to view full size
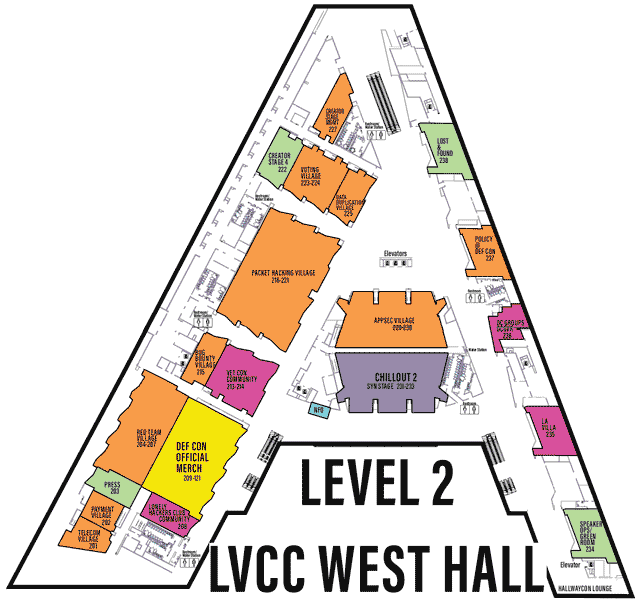
LVCCW map of North portion of Level 2
Click on image to view full size
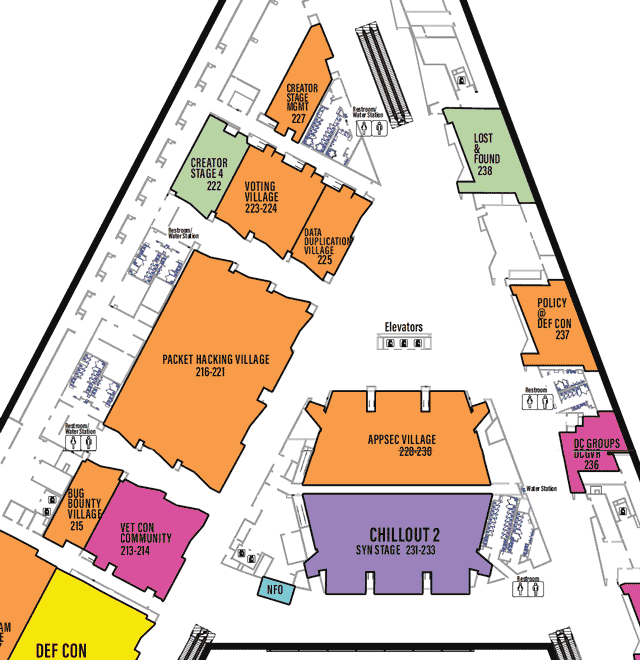
LVCCW map of West portion of Level 2
Click on image to view full size
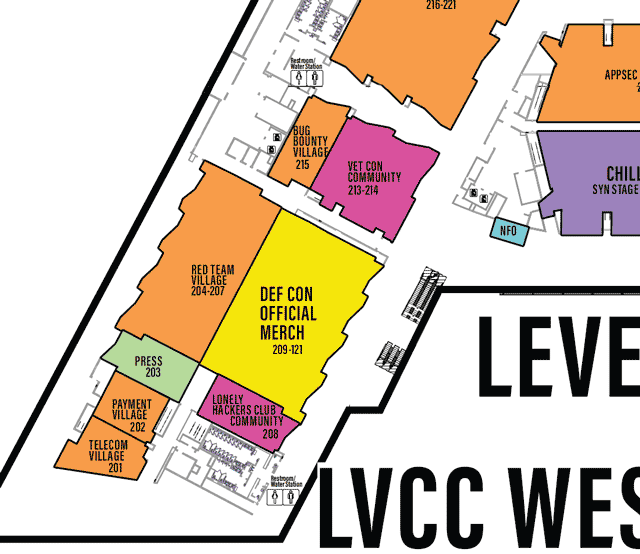
LVCCW map of East portion of Level 2
Click on image to view full size
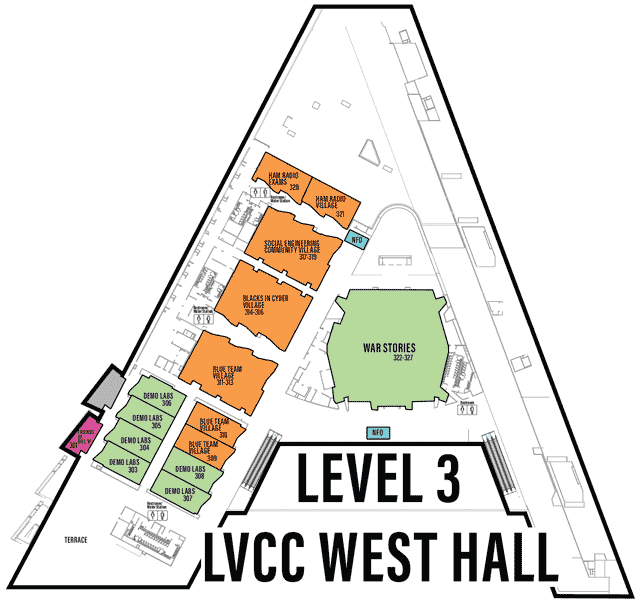
LVCCW Full map of Level 3
Click on image to view full size
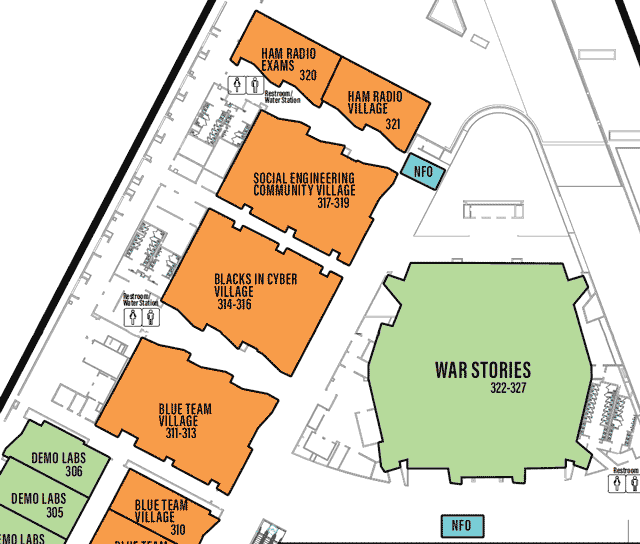
LVCCW map of North portion of Level 3
Click on image to view full size
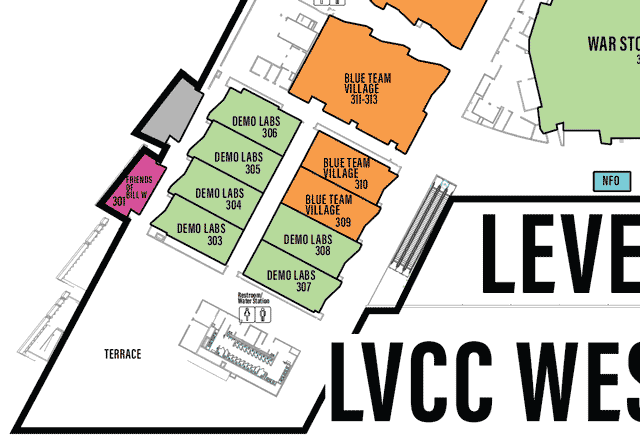
LVCCW map of North portion of Level 3
Click on image to view full size
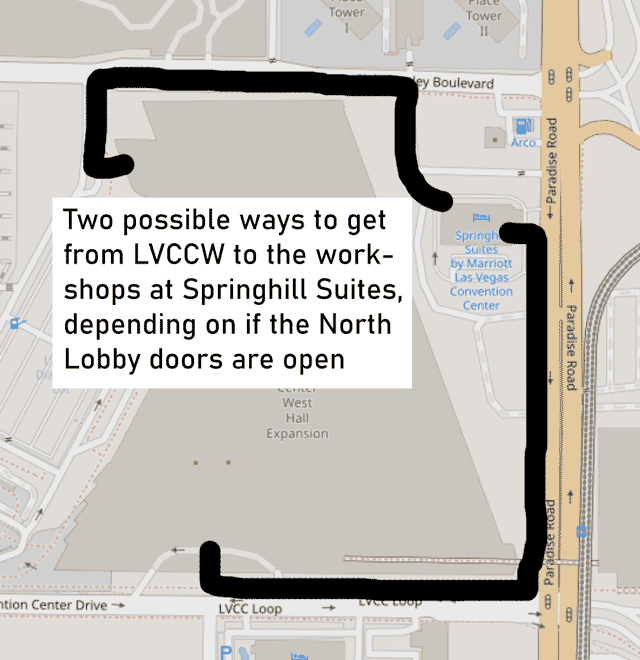
Workshops location - Springhill Suites
Click on image to view full size
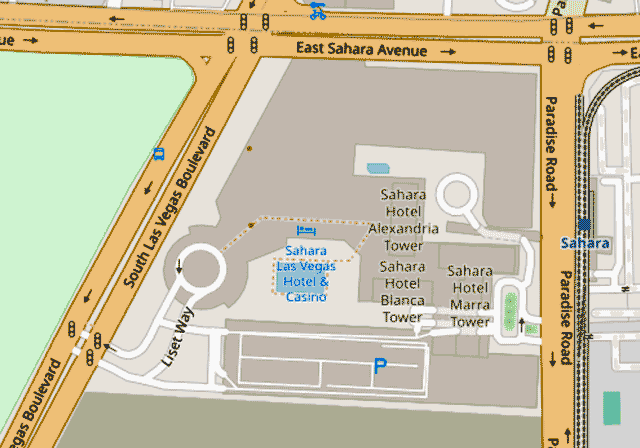
Paid Training location - Sahara
Click on image to view full size
Map Browser
LV Strip Overview - Closeup - Sahara - Springhill
L1_Full - L1_North - L1_South
L1_RegHDA - L1_Hall1 - L1_Hall2 - L1_Hall3 - L1_Hall4
L2_Full - L2_North - L2_West - L2_East
L3_Full - L3_North - L3_South
PDF of LVCCW DEF CON 32 map - full rez, best for zooming in
Las Vegas Convention Center - Virtual Tour
Detailed Village Info
ADV Village: Talk List
Home Page: https://adversaryvillage.org
Sched Page: https://adversaryvillage.org/adversary-events/DEFCON-32/
DC Village Page: #adversary
DC Forums Page: https://forum.defcon.org/node/248651
Location: LVCC West/Floor 1/Hall 4/HW4-03-05 - Map
Social Media Links:
TW @AdversaryVillag
https://defcon.social/@AdversaryVillage
YT https://youtube.com/AdversaryVillage
DC http://adversaryvillage.org/discord
TI @AdversaryVillage
FB @AdversaryVillage
LI @adversaryvillage

Adversary Village is a community initiative which primarily focuses on adversary simulation, purple teaming, and adversary tradecraft. The village covers adversary emulation, threat/APT/ransomware emulation, breach and adversarial attack simulation, supply chain security, adversary tactics, research on nation-state sponsored threat-actors, adversary intelligence, life, adversarial mindset, adversary philosophy and hacker survival skills.
The goal of the Adversary Village is to build an open security community for the researchers and organizations, who are putting together new means, methodologies towards the simulation and emulation of adversary tactics and purple teaming.
Subsequent to feedback from past editions, Adversary Village shall focus on hosting hands-on deep technical workshops, live demonstrations, panel discussions and a ton of other hands-on activities on adversarial attack simulation/emulation, adversary tactics and hacker survival skills.
Adversary Village would have the following hands-on activities for this year at DEF CON;
Adversary simulator and purple teaming hands-on booth:
Adversary Simulator booth is a volunteer assisted activity, which has hands-on adversary emulation plans and exercises specific to a wide variety of threat-actors; these are meant to provide the participants with a better understanding of adversarial attack emulation. The booth will be hosting a simulated environment meant to recreate enterprise infrastructure, operational technology environment, which serves targets for various attack simulations.
The hands-on simulator booth also hosts an activity, which would need the participants to generate their own adversary emulation plans to assess the efficacy of the defense systems based on publicly available cyber threat intelligence.
Choose-your-own adversary adventure game:
Adversary adventure is a story-scenario based, interactive, choose-your-own adventure model interactive game. This is a gamified version of table-top exercises which is presented to the participants as they can choose to play as an attacker, post exploitation OR a Defender who is defending against an attacker group-threat actor OR even play as a CISO who is dealing with an adversarial situation such as a ransomware incident.
Hands-on deep technical workshops:
Adversary Village will feature a limited number of deep technical workshops focused on advanced adversary tradecraft and techniques.
Adversary Wars CTF:
Adversary Village will be hosting a CTF named "Adversary Wars", where the participants will have to pose as adversaries and replicate adversarial actions against each element of a “target” organization. Adversary Wars would have real world simulation of CTF scenarios and challenges, where the participants can perform various attacks and learn new attack vectors, TTPs, techniques, etc. To visualize the CTF environment, the contest area will feature a miniature model of the city made using interlocking-plastic-bricks. The breached components OR organization buildings will be physically marked in the city model as the CTF progresses.
Just like in previous years, winning teams in the CTF competition can expect fantastic prizes. Additionally, there will be complimentary hoodies (yes, the iconic adversary village hoodies), free t-shirts, cool stickers, village coins, badges, and various other swag for the village participants.
Links: Mastodon (defcon.social) -
https://defcon.social/@AdversaryVillage
Website -
https://adversaryvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248652
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248651
Twitter (@AdversaryVillag) -
https://twitter.com/AdversaryVillag
Return to Index
AIV Village: Talk List
Home Page: https://aivillage.org/
Sched Page: https://aivillage.org/events/
DC Village Page: #ai
DC Forums Page: https://forum.defcon.org/node/248648
DC Discord Chan: https://discord.com/channels/708208267699945503/732733090568339536
Location: LVCC West/Floor 1/Hall 2/HW2-07-03 - Map
Social Media Links:
TW @aivillage_dc
TI @aivillage
YT link
DC https://discord.com/invite/GX5fhfT

AI Village is focused on teaching you what you need to know to both defend and break AI. Come learn how ChatGPT, StableDiffusion, malware detectors, ML firewalls, and other AI based products work and how to break them. We have a talks track with world class ML security professionals talking about what they've seen and done in the industry. This year we've expanded the demo area into 8 stations with demos designed to get you up to speed with the underlying technology fast and hands on. Finally, we're running workshops in the morning on dedicated hardware and for the afternoon a generative red team event where you can assess open source models and defenses.
Links: Website -
https://aivillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248649
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248648
Return to Index
AIxCC Village: Talk List
Home Page: https://aicyberchallenge.com/
Sched Page: https://aicyberchallenge.com/
DC Village Page: #aixcc
DC Forums Page: https://forum.defcon.org/node/248672
Location: LVCC West/Floor 1/Hall 3/HW3-05-06 - Map
Social Media Links:
TW @DARPA

The Artificial Intelligence Cyber Challenge (AIxCC) is a two-year competition and educational experience asking the best and brightest in AI and cybersecurity to defend the software on which the world relies. AIxCC will ask competitors to design novel AI systems to secure this critical code and will award a cumulative $29.5 million in prizes to teams with the best systems, including $7 million in prizes to small businesses to empower entrepreneurial innovation during the initial phase of AIxCC.
AIxCC will bring together leading AI companies that will work with DARPA to make their cutting-edge technology and expertise available for challenge competitors. These companies will collaborate with DARPA to enable competitors to develop state-of-the-art cybersecurity systems. AIxCC is collaborating closely with the open-source community to guide teams in creating AI systems capable of addressing vital cybersecurity issues, such as the security of critical infrastructure and software supply chains. Most software, and thus most of the code needing protection, is open-source software, often developed by community-driven volunteers. Further, open-source software comprises most of the code running on critical infrastructure in the United States today, including the electricity and telecommunications sectors.
AIxCC competitions will occur at one of the world’s top cybersecurity conferences, DEF CON. The semifinal competition will be at DEF CON 2024, and the final competition at DEF CON 2025, where the top prize will be $4 million.
Links: Website -
https://aicyberchallenge.com/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248673
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248672
Twitter (@DARPA) -
https://twitter.com/DARPA
Return to Index
APV Village: Talk List
Home Page: https://www.appsecvillage.com/
Sched Page: https://www.appsecvillage.com/events/dc-2024
DC Village Page: #appsec
DC Forums Page: https://forum.defcon.org/node/248676
DC Discord Chan: https://discord.com/channels/708208267699945503/790973922949726228
Location: LVCC West/Floor 2/W228-W230 - Map
Social Media Links:
TW @AppSec_Village
LI @appsecvillage
YT https://www.youtube.com/c/AppSecVillage
DC https://discord.gg/5XY8qYXd7R

Come immerse yourself in everything the world of application security has to offer. Whether you are a red, blue, or purple teamer, come learn from the best of the best to exploit software vulnerabilities and secure software. Software is everywhere, and Application Security vulnerabilities are lurking around every corner, making the software attack surface attractive for abuse. If you are just an AppSec n00b or launch deserialization attacks for fun and profit, you will find something to tickle your interest at the AppSec Village.
Software runs the world. Everything from IoT, medical devices, the power grid, smart cars, and voting apps - all have software behind them. Such a variety of topics will be reflected in our cadre of guest speakers representing all backgrounds and walks of life.
AppSec Village welcomes all travelers to choose from talks and workshops by expert community members, an all-AppSec-focused CTF, contests that challenge your mind and your skillz, and more. Bring your thirst for knowledge and passion for breaking things, and your visit to AppSec Village will be thrilling!
Links: Website -
https://www.appsecvillage.com/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248677
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248676
Twitter (@AppSec_Village) -
https://twitter.com/AppSec_Village
Return to Index
ASV Village: Talk List
Home Page: https://aerospacevillage.org/
Sched Page: https://www.aerospacevillage.org/defcon-32-talk-schedule
DC Village Page: #aerospace
DC Forums Page: https://forum.defcon.org/node/248644
DC Discord Chan: https://discord.com/channels/708208267699945503/732393044363444264
Location: LVCC West/Floor 1/Hall 2/HW2-07-02 - Map
Social Media Links:
TW @secureaerospace
LI @aerospace-village
TW @hack_a_sat
DC https://discord.gg/gV4EWuk
YT https://www.youtube.com/c/AerospaceVillage
https://defcon.social/@aerospacevillage

The aviation and space industries, security researchers, and the public share a common goal: safe, reliable, and trustworthy aviation and space operations. For too long, negative perceptions and fractured trust on all sides have held back collaboration between the aviation, space, and security researcher communities that has advanced safety, reliability, and security of other industries. As the traditional domains of aviation safety and cybersecurity increasingly overlap, more effective collaboration between stakeholders ensures we will be safer, sooner, together.
Through the Aerospace Village, the security research community invites industry leaders, researchers and academia interested in aviation and space security, safety, and resilience to attend, understand, collaborate together to achieve our common goals. Empathy and understanding build common ground, while acts and words likely to increase division between these two communities undermine these efforts. The Aerospace Village welcomes those who seek to improve aviation and space security, safety, and resilience through positive, productive collaboration among all ecosystem stakeholders.
Our Goal
The Aerospace Village is a volunteer team of hackers, pilots, and policy advisors who come from the public and private sectors. We believe the flying public deserves safe, reliable, and trustworthy air travel which is highly dependent on secure aviation and space operations.
Our Mission
- Create, sustain, and grow an inclusive community focused on aerospace cybersecurity;
- Inspire the next generation of aerospace cybersecurity leaders;
- Promote and develop aerospace cybersecurity expertise and knowledge.
The Aerospace Village will do this by:
- Building connections, trust, and understanding among all Village participants.
- Developing aerospace security skills among DEF CON attendees through workshops and hands-on activities.
- Promoting constructive dialog through talks and interaction.
Links: Website -
https://www.aerospacevillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248645
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248644
Twitter (@secureaerospace) -
https://twitter.com/secureaerospace
Return to Index
BBV Village: Talk List
Home Page: https://bugbountydefcon.com/
Sched Page: https://www.bugbountydefcon.com/agenda
DC Village Page: #bbv
DC Forums Page: https://forum.defcon.org/node/248952
Location: LVCC West/Floor 2/W215 - Map
Social Media Links:
TW @BugBountyDEFCON
YT https://www.youtube.com/BountyTalks
TW @arl_rose
TW @infinitelogins
YT https://www.youtube.com/infinitelogins

The global bug bounty community has witnessed exponential growth, with thousands of members actively engaged in the field. This thriving ecosystem now represents a legitimate and sought-after profession for hackers and cybersecurity specialists. It's time to acknowledge and celebrate this evolution by introducing a dedicated Bug Bounty Village at DEFCON, where hunters, learners, and enthusiasts can converge, interact with top-tier hackers, attend insightful talks, and immerse themselves in hands-on activities.
Our Bug Bounty Village promises to be a focal point for DEFCON attendees. It will feature exclusive talks by some of the world's foremost bug bounty hunters, who will unveil their groundbreaking techniques and share real-world vulnerabilities discovered through their exploits. Furthermore, representatives from leading global companies with established bug bounty programs will provide invaluable insights, guidance, and recommendations for both aspiring hunters and organizations keen on launching their bug bounty initiatives.
Inclusive Learning & Community Engagement:
Our village aims to cater to all levels of expertise, from beginners taking their first steps in bug hunting to seasoned professionals looking to enhance their skills. We will conduct a series of workshops that cover a wide spectrum of topics, ranging from fundamental concepts for newcomers to advanced techniques tailored to the most experienced hackers in the field. Participants will have the opportunity to delve into practical exercises and learn to utilize tools like Portswigger Burp Proxy effectively.
Links: Website -
https://bugbountydefcon.com/
Organizer YouTube (bountytalks) -
https://www.youtube.com/c/bountytalks
Organizer YouTube (infinitelogins) -
https://www.youtube.com/c/infinitelogins
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248953
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248952
Twitter (@BugBountyDEFCON) -
https://twitter.com/BugBountyDEFCON
Twitter (@arl_rose) -
https://twitter.com/arl_rose
Twitter (@infinitelogins) -
https://twitter.com/infinitelogins
Return to Index
BHV Village: Talk List
Home Page: https://www.villageb.io/
Sched Page: https://www.villageb.io/creatorstage2024
DC Village Page: #biohacking
DC Forums Page: https://forum.defcon.org/node/248654
DC Discord Chan: https://discord.com/channels/708208267699945503/735273390528528415
Location: LVCC West/Floor 1/Hall 3/HW3-05-07 - Map
Social Media Links:
TW @dc_bhv
LI @biohacking-village
YT http://youtube.com/biohackingvillage
TI @biohackingvillage
DC https://discord.gg/Q8ubDb5
IG @biohacking_village
link

Dive into the Future at the Biohacking Village: Welcome to the Intersection of Biology and Technology
Are you ready to explore the next frontier where technology meets biology? The Biohacking Village at DEF CON invites hackers, cybersecurity experts, biologists, and tech enthusiasts to delve into the exhilarating world of biohacking. This is your unique opportunity to be at the forefront of a revolution that’s redefining the boundaries of biology, technology, and human potential.
Why the Biohacking Village?
- Uncover the Unknown: Embark on a journey to explore how hacking skills can unlock new potentials in biotechnology. Discover the secrets of DNA hacking, medical device exploitation, and more.
- Challenge Your Skills: Put your hacking abilities to the test in an entirely new domain. From breaking into sophisticated bioinformatics databases to uncovering vulnerabilities in the latest medical devices, challenge yourself like never before.
- A Hub of Innovation: Witness groundbreaking demonstrations and hands-on workshops led by pioneers in biotechnology and cybersecurity. The Biohacking Village is your chance to see the future as it unfolds.
- Collaborate and Create: Join a diverse community of hackers, scientists, healthcare professionals, and ethicists. Collaborate on projects that push the boundaries of what's possible in health, security, and technology.
- Ethical Hacking for the Greater Good: Use your skills to make a real-world impact. Contribute to projects focusing on improving public health, securing medical data, and enhancing the safety of biomedical devices.
What Awaits You?
- Innovative Talks & Panels: Engage with thought leaders discussing everything from CRISPR gene editing to the cybersecurity of implantable devices.
- Hands-on Workshops: Learn new skills in biohacking, from DIY biology to the art of securing complex bio-systems.
- Live Demonstrations: Experience cutting-edge technology in action, including live hacking of medical devices and bioinformatics systems.
- Networking Opportunities: Connect with like-minded individuals and industry leaders who share your passion for technology and innovation.
Join the Vanguard of Biocybersecurity
At the Biohacking Village, we’re not just spectators; we’re active participants shaping the future. Whether you're a seasoned hacker or just curious about the intersection of biology and technology, there's something for everyone. Be a part of a community that’s breaking new ground and redefining the possibilities of technology and biology.
Embrace your curiosity, unleash your potential, and join us at the Biohacking Village – where the future of biohacking and cybersecurity converges.
Links: Website -
https://villageb.io/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248655
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248654
Return to Index
BICV Village: Talk List
Home Page: https://www.blacksincyberconf.com/bic-village
Sched Page: https://www.blacksincyberconf.com/bic-village
DC Village Page: #bic
DC Forums Page: https://forum.defcon.org/node/248660
Location: LVCC West/Floor 3/W314-W316 - Map
Social Media Links:
TW @BlackInCyberCo1
https://defcon.social/@blacksincyber
TI @blacksincybersecurity
YT link
LI @blackincyberconference
PT @blacksincybersecurity
FB @blackincyberconf

The Blacks In Cybersecurity (B.I.C.) Village seeks to bring culturally diverse perspectives to the holistic Cybersecurity community; by way of a series of talks and a capture the flag event. In providing these activities, we hope to help highlight Black experiences, innovations in the field, Black culture and educate the community about Black history.
The B.I.C. Village attracts and retains the presence of Hackers from the United States, Africa, Caribbean and Europe (so far) that are a part of the African Diaspora. This often underrepresented and misrepresented community harbors the drive, determination and stick-to-itiveness that is congruent to the Hacker Spirit yet, statistically lacks the proper resources to pursue careers or engage their perspectives on security topics and research.
Through the exposure and information provided by B.I.C. Village, we believe that we can normalize the discussion of deficiency or prejudices in Cybersecurity education/development for minority communities. We also believe this effort can be translated to allow for more diverse hobbyists and professionals to engage and contribute.
Links: Mastodon (defcon.social) -
https://defcon.social/@blacksincyber
Mastodon (infosec.exchange) -
https://infosec.exchange/@blacksincyber
Website -
http://www.blacksincyberconf.com/bic-village
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248661
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248660
Return to Index
BTV Village: Talk List
Home Page: https://blueteamvillage.org/
Sched Page: https://cfc.blueteamvillage.org/dc32/schedule/
DC Village Page: #btv
DC Forums Page: https://forum.defcon.org/node/248657
DC Discord Chan: https://discord.com/channels/708208267699945503/732454317658734613
Social Media Links:
TW @BlueTeamVillage
TI @blueteamvillage
YT https://www.youtube.com/c/blueteamvillage
DC https://discord.gg/blueteamvillage
https://defcon.social/@blueteamvillage

Welcome to the other side of the hacking mirror. Blue Team Village (BTV) is both a place and a community built for and by people who defend computer systems, networks, and people against cyber attacks. It's a place to gather, talk, share, and learn from each other about the latest tools, technologies, and tactics that our community can use to detect attackers and prevent them from achieving their goals.
Project Obsidian – BTV’s Home-Grown Content
The Blue Team Village’s Project Obsidian is an immersive, defensive cybersecurity learning experience that provides attendees with the opportunity to gain knowledge of Incident Response (IR), Digital Forensics (DF), Malware Analysis, Cyber Threat Intelligence (CTI), and Cyber Threat Hunting (CTH). Deep dive into technical topics through workshops and exercises that provide practical hands-on experience across each discipline. Project Obsidian workshops provide cybersecurity training that will enable attendees to develop skills needed to be successful in their current and/or future role.
Two of the most valuable takeaways are how to strategically approach a task and the operational processes that support the objectives behind each task. Knowing ‘how’ to do something is only part of the challenge. Knowing ‘when’ and ‘why’ to perform certain tasks adds necessary context to develop the full story of defensive cybersecurity.
Links: Mastodon (@blueteamvillage@defcon.social) -
https://defcon.social/@blueteamvillage
Website -
https://blueteamvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248658
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248657
Twitter (@BlueTeamVillage) -
https://twitter.com/BlueTeamVillage
Return to Index
CHV Village: Talk List
Home Page: https://www.carhackingvillage.com/
Sched Page: https://www.carhackingvillage.com/defcon-32-talks
DC Village Page: #ch
DC Forums Page: https://forum.defcon.org/node/248679
DC Discord Chan: https://discord.com/channels/708208267699945503/732722838942777474
Location: LVCC West/Floor 1/Hall 4/HW4-01-01 - Map
Social Media Links:
TW @CarHackVillage
YT http://youtube.com/@carhackingvillage
LI @car-hacking-village
DC https://discord.gg/JWCcTAM

Return to Index
CLV Village: Talk List
Home Page: https://cloud-village.org/
Sched Page: https://dc32.cloud-village.org/
DC Village Page: #cloud
DC Forums Page: https://forum.defcon.org/node/248682
DC Discord Chan: https://discord.com/channels/708208267699945503/732733373172285520
Location: LVCC West/Floor 1/Hall 2/HW2-09-01 - Map
Social Media Links:
TW @cloudvillage_dc
YT https://www.youtube.com/cloudvillage_dc
DC https://discord.gg/EygUDJABee

With the industry’s rapid growth in cloud infrastructure, the presence of an open platform to discuss and showcase cloud research becomes a necessity.
Cloud village is an open platform for researchers interested in the area of cloud security. We plan to organise talks, tool demos, CTF and workshops around Cloud Security and advancements.
Our CTF will be a jeopardy style 2.5 days contest where participants will have to solve challenges around Cloud infrastructure, security, recon, etc. These challenges will cover different cloud platforms including AWS, GCP, Azure, Alibaba, Digital Ocean, etc. We will also reward our top 3 teams with awards.
Links: Website -
https://dc32.cloud-village.org
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248683
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248682
Twitter (@cloudvillage_dc) -
https://twitter.com/cloudvillage_dc
Return to Index
CON Village: Talk List
Home Page: https://defcon.outel.org/dcwp/dc32/activities/contests-list/
Sched Page: https://defcon.outel.org/defcon32/dc32-dc32-consolidated_page.html#villist_CON
DC Forums Page: https://forum.defcon.org/node/248121
Social Media Links:
link
Return to Index
CPV Village: Talk List
Home Page: https://cryptovillage.org/
Sched Page: https://cryptovillage.org/
DC Village Page: #cpv
DC Forums Page: https://forum.defcon.org/node/248685
DC Discord Chan: https://discord.com/channels/708208267699945503/732734002011832320
Location: LVCC West/Floor 1/Hall 2/HW2-09-02 - Map
Social Media Links:
TW @cryptovillage
SL https://cryptovillage.slack.com/
YT link
TI @cryptovillage
https://defcon.social/@cryptovillage

Launched in 2014, Crypto & Privacy Village (CPV) is a community-run village centred on privacy and cryptography that aims to educate and inform the general public, students, educators, hackers, security and privacy professionals, and policymakers. We provide a unique hybrid space that features talks; chill space for relaxing with friends, doing CTFs, and cross industry networking; the Gold Bug Challenge and desk for hints and support; privacy-related art installations; and an information desk for questions about privacy and cryptography. Come talk with us about facial recognition technology, privacy enhancing clothing, or crypto backdoor laws!
Links: Mastodon (@cryptovillage@defcon.social) -
https://defcon.social/@cryptovillage
Website -
https://cryptovillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248686
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248685
Return to Index
DC Village: Talk List
Home Page: https://defcon.org/html/defcon-32/dc-32-speakers.html
Sched Page: https://defcon.outel.org/defcon32/dc32-dc32-consolidated_page.html#villist_DC
Social Media Links:
TW @defcon
FB @defcon
YT https://www.youtube.com/user/DEFCONConference
http://www.reddit.com/r/defcon
IG @wearedefcon
DC https://discord.gg/defcon
Return to Index
DCG Village: Talk List
Return to Index
DCGVR Village: Talk List
Home Page: https://www.dcgvr.org/
Sched Page: https://www.dcgvr.org/
DC Forums Page:
Social Media Links:
TW @DCGVR
TI @defcon_groups
DC https://discord.gg/bsX4QXf3rD
YT link
Return to Index
DDV Village: Talk List
Home Page: https://dcddv.org/
Sched Page: https://dcddv.org/dc32-schedule
DC Village Page: #ddv
DC Forums Page: https://forum.defcon.org/node/248949
DC Discord Chan: https://discord.com/channels/708208267699945503/732732641694056478
Location: LVCC West/Floor 2/W225 - Map
Social Media Links:
TW @DDV_DC

The Data Duplication Village has all the updated bits and bytes available from infocon.org packed up into nice, neat packages. If you're looking for a copy of all the things, we've got what you need to fill up all your storage including a few nice hash tables and all of the DefCon talks. Add to that just about every other security con talk known to hacker-kind! Our village provides a "free-to-you" service of direct access to terabytes of useful data to help build those hacking skills and talk with other storage enthusiasts.
Check the schedule and/or dcddv.org for the most up-to-date information.
## How It Works
The DDV provides a core set of drive duplicators and data content options. We accept 8TB and larger drives on a first come, first served basis and duplicate 'till we can no longer see straight. Bring in your blank SATA3 drives - check them in early - to get the data you want. Come back in about 24 hours to pick up your data-packed drive. Space allowing, we'll accept drives all the way through until Saturday morning - but remember, it's FIFO - get those drives in early!
## What You Get
We're working on more content right up until the last minute so keep checking on dcddv.org for the latest. This year, we're adding new data to duplicate! Humans will be able to choose from the following data sources for duplication:
- A) Infocon.org Archive - 6TB archive of all the past hacking convention videos that DT could find, built on last years collection and always adding more for your data consuming appetite.
- B) Rainbow tables 1 of 3 - 6TB from freerainbowtables.com, the Lanman, MSQLSHA1, and NTLM hash tables plus freerainbowtables.com tools
- C) Rainbow tables 2 of 3 - 6TB from freerainbowtables.com, the A5/1 GSM, and MD5 tables plus freerainbowtables.com tools
- D) Vx Underground Archive - 8TB archive of the latest papers, samples, and code from Vx Underground
- E) Rainbow tables 3 of 3 - 8TB of New NTLM-9 hash tables and a copy of the Infocon.org mirrors
Links: Website -
https://dcddv.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248950
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248949
Return to Index
DL Village: Talk List
Home Page: https://forum.defcon.org/node/248122
Sched Page: https://defcon.outel.org/defcon32/dc32-dc32-consolidated_page.html#villist_DL
Return to Index
ESV Village: Talk List
Home Page: https://embeddedvillage.org/
DC Village Page: #esv
DC Forums Page: https://forum.defcon.org/node/248663
Location: LVCC West/Floor 1/Hall 3/HW3-05-05 - Map
Social Media Links:
TW @EmbeddedVillage

Embedded systems exist at the intersection of hardware and software, built to accomplish a specific task. Often these disciplines are dealt with individually, but understanding the custom relationships between hardware and software is key to performing security research on these devices.
Embedded Systems Village advances the security of embedded systems by hosting hands-on hacking workshops, showcasing new security research demos, and organizing exciting hacking contests to educate attendees and manufacturers on the approach hackers use to attack these devices. Attendees will leave the village with an understanding of how to reduce complex, exotic devices to their underlying embedded components and to extract the information required to use the tools and techniques taught at other villages where embedded systems are on display.
Links: Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248664
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248663
Return to Index
HDA Village: Talk List
Social Media Links:
TW @HDA_DEFCON
Return to Index
HHV Village: Talk List
Home Page: https://dchhv.org/
Sched Page: https://dchhv.org/schedule/schedule.html
DC Village Page: #hhv
DC Forums Page: https://forum.defcon.org/node/248669
DC Discord Chan: https://discord.com/channels/708208267699945503/732728536149786665
Location: LVCC West/Floor 1/Hall 2/HW2-10-01 - Map
Social Media Links:
TW @DC_HHV
https://defcon.social/@DC_HHV

Every day our lives become more connected to consumer hardware. Every day the approved uses of that hardware are reduced, while the real capabilities expand. Come discover hardware hacking tricks and tips regain some of that capacity, and make your own use for things! We have interactive demos to help you learn new skills. We have challenges to compete against fellow attendees. We have some tools to help with your fever dream modifications. Come share what you know and learn something new.
Links: Website -
https://ddhhv.org/
Mastodon (@DC_HHV@defcon.social) -
https://defcon.social/@DC_HHV
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248670
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248669
Return to Index
HRV Village: Talk List
Home Page: https://hamvillage.org/
Sched Page: https://hamvillage.org/dc32/index.html
DC Village Page: #ham
DC Forums Page: https://forum.defcon.org/node/248666
DC Discord Chan: https://discord.com/channels/708208267699945503/732733631667372103
Location: LVCC West/Floor 3/W321 - Map
Social Media Links:
TW @HamRadioVillage
TI @HamRadioVillage
DC https://discord.gg/hrv
https://defcon.social/@HamRadioVillage

Ham radio is the original group of electronic hackers, starting long before computers, circuit chips, or even transistors. Continuing this pioneer spirit, Ham Radio Village is here to support advancement of the hobby with a cybersecurity slant. Everything we do today involves wireless communications of some sort, and a basic knowledge of how radio works is crucial. In the HRV, you can learn hand-on with topics such as how to legally use a radio to send commands to a satellite, communicating around the globe when no other methods exist, and how to send and receive real-time location data without relying on any cellular networks. You can put your skills to the test by trying to find the hidden transmitters in the Ham Radio Fox Hunt contest, as well as transmitting memes over the airwaves to defcon attendees. We provide license testing services for those looking to become licensed or upgrade their license class, as well as guidance on how to hack on the medium to achieve the best results and have the most fun!
Links: Mastodon (defcon.social) -
https://defcon.social/@HamRadioVillage
Website -
https://hamvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248667
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248666
Return to Index
ICSV Village: Talk List
Home Page: https://www.icsvillage.com/
Sched Page: https://www.icsvillage.com/defconevents/def-con-32
DC Village Page: #ics
DC Forums Page: https://forum.defcon.org/node/248688
DC Discord Chan: https://discord.com/channels/708208267699945503/735938018514567178
Location: LVCC West/Floor 1/Hall 3/HW3-06-05 - Map
Social Media Links:
TW @ICS_Village
LI @icsvillage
YT link
TI @ics_village

**Mission**. ICS Village is a non-profit organization with the purpose of providing education and awareness of Industrial Control System security.
- Connecting public, industry, media, policymakers, and others directly with ICS systems and experts.
- Providing educational tools and materials to increase understanding among media, policymakers, and general population.
- Providing access to ICS for security researchers to learn and test.
- Hands on instruction for industry to defend ICS systems.
**Exhibits**. Interactive simulated ICS environments that provide safe yet realistic examples to preserve safe, secure, and reliable operations. We bring real components such as Programmable Logic Controllers (PLC), Human Machine Interfaces (HMI), Remote Telemetry Units (RTU), and actuators, to simulate a realistic environment throughout different industrial sectors. Visitors can connect their laptops to assess these ICS devices with common security scanners, network sniffers to sniff the industrial traffic, and more! We will also have space dedicated to Maritime technology as well as Escape Rooms ran by Idaho National Labs and CISA. In addition to talks, hands-on demos/hacking, and escape rooms we are collaborating with BioHacking Village to demonstrate how Industrial Control Systems are used in Health Care.
Links: Website -
https://www.icsvillage.com/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248689
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248688
Return to Index
IOTV Village: Talk List
Home Page: https://www.iotvillage.org/
Sched Page: https://www.iotvillage.org/defcon.html#Talks
DC Village Page: #iot
DC Forums Page: https://forum.defcon.org/node/248691
DC Discord Chan: https://discord.com/channels/708208267699945503/732734565604655114
Location: LVCC West/Floor 1/Hall 2/HW2-08-04 - Map
Social Media Links:
TW @iotvillage
TW @ISEsecurity
TW @Villageidiotlab
https://defcon.social/@IoTVillage/
TI @iotvillage
YT https://www.youtube.com/c/IoTVillage/videos
DC https://discord.gg/EFKbNFrFaN

Return to Index
LPV Village: Talk List
Home Page: https://www.toool.us/
Sched Page: https://x.com/toool/status/1821662290296660451
DC Village Page: #lpv
DC Forums Page: https://forum.defcon.org/node/248927
DC Discord Chan: https://discord.com/channels/708208267699945503/732734164780056708
Location: LVCC West/Floor 1/Hall 2/HW2-07-03-A - Map
Social Media Links:
TW @toool
TI @toool_us
YT https://youtube.com/c/TOOOL-US
https://techhub.social/@TOOOL

Want to tinker with locks and tools the likes of which you've only seen in movies featuring secret agents, daring heists, or covert entry teams?
Then come on by the Lockpick Village, run by The Open Organization Of Lockpickers, where you will have the opportunity to learn hands-on how the fundamental hardware of physical security operates and how it can be compromised.
The Lockpick Village is a physical security demonstration and participation area. Visitors can learn about the vulnerabilities of various locking devices, techniques used to exploit these vulnerabilities, and practice on locks of various levels of difficultly to try it themselves.
Experts will be on hand to demonstrate and plenty of trial locks, pick tools, and other devices will be available for you to handle. By exploring the faults and flaws in many popular lock designs, you can not only learn about the fun hobby of sport-picking, but also gain a much stronger knowledge about the best methods and practices for protecting your own property.
Links: Website -
https://www.toool.us/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248928
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248927
Twitter (@toool) -
https://twitter.com/toool
Return to Index
MISC Village: Talk List
Sched Page: https://defcon.outel.org/defcon32/dc32-dc32-consolidated_page.html#villist_MISC
Return to Index
PHV Village: Talk List
Home Page: https://www.wallofsheep.com/
Sched Page: https://www.wallofsheep.com/pages/dc32
DC Village Page: #phv
DC Forums Page: https://forum.defcon.org/node/248889
DC Discord Chan: https://discord.com/channels/708208267699945503/708242376883306526
Location: LVCC West/Floor 2/W216-W221 - Map
Social Media Links:
TW @wallofsheep
FB @wallofsheep
YT https://youtube.com/wallofsheep
TI @wallofsheep
PS https://www.periscope.tv/wallofsheep
https://defcon.social/@wallofsheep
IG @wallofsheep

The Packet Hacking Village at DEF CON provides a community learning experience for people of all skill levels, from absolute beginners to seasoned professionals. While DEF CON is made up of dozens of small community-of-interest villages, we are one of the largest and most well known. We host practical training, network forensics and analysis games, and the renowned Capture The Packet event, which has been a Black Badge contest over 10 times and draws world-class hackers from around the world. Our mission has always been simple: to teach people good internet safety practices, and to provide an atmosphere that encourages everyone to explore and learn.
We provide a welcoming environment for hackers of all skill levels and backgrounds to network, learn new things, and be active participants in DEF CON. Our famous “Wall of Sheep” provides a fun and interactive take on internet security and privacy, while our contests Packet Inspector, Packet Detective, and Capture The Packet serve as a zero-to-hero pathway for individuals to learn network security, packet analysis, and delve into advanced security topics. Every year we strive to bring something new and innovative to DEF CON, whether it’s never-seen-before talks or creative games to teach and test skills.
Depending on what talks, contests, and events participants select, they can expect to learn any/all of the following:
Basic Internet security and privacy, network cable construction, honeypot setup and operation, regex, Linux training, packet interception and decoding, network analysis, sniffing, and forensics, reverse engineering, file forensics, system forensics, cryptography analysis, and more to be determined by the talks and workshops that we accept.
The Packet Hacking Village and Wall of Sheep have been a part of DEF CON since DEF CON 9, and we are proud to provide education and training to the hacker community at no cost.
Links: Facebook -
https://www.facebook.com/wallofsheep
Instagram -
https://www.instagram.com/wallofsheep/
YouTube -
https://www.youtube.com/channel/UCnL9S5Wv_dNvO381slSA06w
Mastodon (defcon.social) -
https://defcon.social/@wallofsheep
Pinterest -
https://www.pinterest.com/wallofsheep/
Tumblr -
https://wallofsheep.tumblr.com/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248890
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248889
Twitter (@wallofsheep) -
https://twitter.com/wallofsheep
Return to Index
PLV Village: Talk List
Home Page: https://defcon.org/policy/
DC Village Page: #policy
DC Forums Page: https://forum.defcon.org/node/248898
Location: LVCC West/Floor 2/W237 - Map
Social Media Links:
TW @DEFCONPolicy
link
https://defcon.social/@defconpolicy

The DEF CON community understands that creating a safer digital society requires collaboration between security and policy experts. Policy @ DEF CON provides a space for representatives of all areas of security to come together to educate and engage each other.
Tech policy is being written as we speak and we believe that including diverse expert voices will improve outcomes and help to bridge gaps between technical and policy practitioners. Senior government officials, nonprofit and private sector experts, security researchers, hackers, academics and technologists from around the world all come together at Policy @ DEF CON.
Links: Mastodon (defcon.social) -
https://defcon.social/@defconpolicy
Website -
https://defcon.org/policy/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248899
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248898
Twitter (@defconpolicy) -
https://twitter.com/defconpolicy
Return to Index
PSV Village: Talk List
Home Page: https://www.physsec.org/
DC Village Page: #psv
DC Forums Page: https://forum.defcon.org/node/248895
DC Discord Chan: https://discord.com/channels/708208267699945503/732732893830447175
Location: LVCC West/Floor 1/Hall 2/HW2-08-03 - Map
Social Media Links:
TW @physsec
TI @bypassvillage
LI @physsec
https://defcon.social/@physsec

The Physical Security Village explores the world of door hardware bypasses and techniques generally outside of the realm of cyber-security and lockpicking. Come learn some of these lock bypasses, how to fix them, and have the opportunity to try them out for yourself.
We’ll be covering the basics, like the under-the-door-tool and latch slipping attacks, as well as an in depth look at more complicated bypasses. Learn about elevator hacking, defeating alarm systems and surveillance cameras, and cut-away and display models of common hardware to show how it works on the inside.
We are one of the easiest villages to get started in - read the instruction sheets we have or scan a QR code to learn the techniques, or ask any of our volunteers in the green shirts if you have questions! Looking for a challenge? Show us you can use lock bypass to escape from a pair of standard handcuffs in under 30 seconds and receive a prize!
Links: Mastodon (defcon.social) -
https://defcon.social/@physsec
Website -
https://physsec.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248896
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248895
Return to Index
PWV Village: Talk List
Home Page: https://passwordvillage.org/
DC Forums Page:
DC Discord Chan: https://discord.com/channels/708208267699945503/732733760742621214
Social Media Links:
TW @PasswordVillage
TI @passwordvillage
YT link
Return to Index
PYV Village: Talk List
Home Page: https://www.paymentvillage.org/
Sched Page: https://www.paymentvillage.org/workshops
DC Village Page: #payment
DC Forums Page: https://forum.defcon.org/node/248892
DC Discord Chan: https://discord.com/channels/708208267699945503/732733473558626314
Location: LVCC West/Floor 2/W202 - Map
Social Media Links:
TW @paymentvillage
TI @paymentvillage
YT link
https://t.me/paymentvillage

Come to the Payment Village to learn about payment technologies, their history, and how hackers bypass security and fraud mechanisms to cash out! Payment technologies play a crucial role in our daily lives, yet many of us lack an understanding of how they work. We invite you to explore the history of payments and to learn how modern-day payments work. The village is jam-packed with hands-on experiences and exciting challenges!
Unsure where to start? Sign up for one of our workshops to get going. Do you have adept problem-solving skills? Pick up a Payment Village credit card and take part in our card hacking challenge! Looking for a unique challenge and want to get physical? Try our scavenger hunt. Bigger and better than last year! Try your hand at our cash-grab machines with real money. Catch as much money as you can to decipher the clues and solve the challenges.
Links: Website -
https://www.paymentvillage.org/
YouTube -
https://www.youtube.com/c/PaymentVillage
Telegram -
https://t.me/paymentvillage
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248893
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248892
Twitter (@paymentvillage) -
https://twitter.com/paymentvillage
Return to Index
QTV Village: Talk List
Home Page: https://quantumvillage.org/
DC Village Page: #quantum
DC Forums Page: https://forum.defcon.org/node/248901
Location: LVCC West/Floor 1/Hall 3/HW3-06-01 - Map
Social Media Links:
TW @quantum_village
DC https://discord.gg/6WUjH5cBXu
LI @quantumvillage
YT https://youtube.com/@quantum_village/

Attention Quantum Hackers - Quantum Village is Back for DEF CON 32! Come and explore and discover new technologies to hack - this year, we are focusing on quantum tech and society; from how to hack quantum networks to how ‘thinking quantum’ could change the world. We have a plethora of new activities, open to all levels, for hackers to come and learn quantum technologies - workshops, some talks, interactive demonstrations, and real quantum hardware! We also have the return of our infamous Quantum-CTF - pitch your wits against the Quantum Quizmasters and earn points for glory! Come and learn more about this exciting emerging field of technology and science, and become a QUANTUM HACKER!
We are very excited to bring back Quantum Village after our standing-room only success these last two years! This year we want to focus on looking at the parallels between how classical computing developed and became distributed and interconnected through LANs and WANs and later social networks, and how quantum computing is looking to do the same with the ‘quantum internet’, and what it means to have a ‘social quantum network’. To this end we are working with some quantum infrastructure companies to have a real quantum network present at the event and ready for people to hack, e.g. via messing with the fibre lines we plan on distributing throughout the village.
We also want to use this analogy to get participants to ask questions about how quantum technologies can, should, and may fit into society at large, building on our ‘Quantum Life’ sessions in previous years that have lead to some really engaging discussions and thought provoking debates - all of which we would continue to build upon.
We also want to provide a bigger, more expansive Quantum CTF competition within the village that we would like to build our own hardware (e.g. badges) to present both as part of the challenge.
Links: Website -
https://quantumvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248902
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248901
Twitter (@quantum_village) -
https://twitter.com/quantum_village
Return to Index
RCV Village: Talk List
Home Page: https://www.reconvillage.org/
Sched Page: https://www.reconvillage.org/talks
DC Village Page: #recon
DC Forums Page: https://forum.defcon.org/node/248907
DC Discord Chan: https://discord.com/channels/708208267699945503/732733566051418193
Location: LVCC West/Floor 1/Hall 4/HW4-03-04 - Map
Social Media Links:
TW @ReconVillage
FB @reconvillage
YT https://www.youtube.com/reconvillage/

Recon Village is an Open Space with Talks, Live Demos, Workshops, Discussions, CTFs, etc., with a common focus on Reconnaissance. The core objective of this village is to spread awareness about the importance of reconnaissance and open-source intelligence (OSINT) and demonstrate how even a small piece of information about a target can cause catastrophic damage to individuals and organizations. As recon is a vital phase for infosec as well as investigations, folks should have this skill set in their arsenal. People should check out Recon Village, as they get to learn novel point/recon techniques, play hands-on CTF, participate in Live Recon, and, most of all, have fun. At RV, we keep things simple, and the focus is on generating quality content using talks, workshops, CTF, live hacking, hackathons, etc. This year, we are launching a new hands-on event, i.e. Live Recon Contest, where we will challenge participants to perform recon on organization (pre-approved) - live and compete against each other to find as many as recon flags. This will include gauging skills like domain discovery, subdomain enumerations, GitHub Dorking, Metadata Extraction, data harvesting, social media profiling, threat intel mining, correlations and aggregations, and a lot more.
Also, to reduce the barrier to entry, we are going to host 101 Hands-on OSINT & Recon Workshops where people can learn and practice some new skills.
Similar to the previous years, there will be Awesome rewards for the winners, along with free t-shirts, stickers, village coins, and other schwag which attendees can grab and show off. We will be making changes to our badge as well. P.S. We will not be selling it, though.
Links: Website -
https://reconvillage.org/
YouTube -
https://www.youtube.com/reconvillage
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248908
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248907
Twitter (@reconvillage) -
https://twitter.com/reconvillage
Return to Index
RFV Village: Talk List
Home Page: https://rfhackers.com/
DC Village Page: #rfv
DC Forums Page: https://forum.defcon.org/node/248904
DC Discord Chan: https://discord.com/channels/708208267699945503/732732595493666826
Location: LVCC West/Floor 1/Hall 3/HW3-05-03 - Map
Social Media Links:
TW @rfhackers
TW @rf_ctf
link
DC https://discordapp.com/invite/JjPQhKy

After 17 years of evolution, from the WiFi Village, to the Wireless Village, RF Hackers Sanctuary presents: The Radio Frequency Village at DEFCON 32. The Radio Frequency Village is an environment where people come to learn about the security of radio frequency (RF) transmissions, which includes wireless technology, applications of software defined radio (SDR), Bluetooth (BT), Zigbee, WiFi, Z-wave, Radio Frequency Identification (RFID), Infrared (IR) and other protocols within the usable RF spectrum. As a security community we have grown beyond WiFi, and even beyond Bluetooth and Zigbee. The RF Village includes talks on all manner of radio frequency command and control as well as communication systems. While everyone knows about the WiFi and Bluetooth attack surfaces, most of us rely on many additional technologies every day. RF Hackers Sanctuary is supported by a group of experts in the area of information security as it relates to RF technologies. RF Hackers Sanctuary’s common purpose is to provide an environment in which participants may explore these technologies with a focus on improving their skills through offense and defense. These learning environments are provided in the form of guest speakers, panels, and Radio Frequency Capture the Flag games, to promote learning on cutting edge topics as it relates to radio communications. We promise to still provide free WiFi.
Co-located with the RF Village is the RF Capture the Flag. Come for the talks, stay for the practice and the competition.
Who runs this thing?
RF Hackers Sanctuary is a group of all volunteers with expertise in radio security and various other related fields. We are the original creators of the WiFi Capture the Flag, Wireless Capture the Flag, and RF Capture the Flag. We are the original founders of the WiFi Village, Wireless Village, and RF Village. Often imitated, never duplicated.
Links: Website -
https://rfhackers.com/
Discord -
https://discordapp.com/invite/JjPQhKy
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248905
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248904
Twitter (@rfhackers) -
https://twitter.com/rfhackers
Twitter (@rf_ctf) -
https://twitter.com/rf_ctf
Return to Index
RTV Village: Talk List
Home Page: https://redteamvillage.io/
Sched Page: https://redteamvillage.io/schedule.html
DC Village Page: #redteam
DC Forums Page: https://forum.defcon.org/node/248910
Location: LVCC West/Floor 2/W204-W207 - Map
Social Media Links:
TW @RedTeamVillage_
YT https://www.youtube.com/redteamvillage
TI @redteamvillage
DC https://discord.gg/redteamvillage

The Red Team Village is focused on training the art of critical thinking, collaboration, and strategy in offensive security. The RTV brings together information security professionals to share new tactics and techniques in offensive security. Attendees may spend all three days engaged in introductory workshops or challenge themselves in an immersive Capture the Flag competition to put their newly obtained skills to the test.
Links: Website -
https://redteamvillage.io/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248911
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248910
Twitter (@RedTeamVillage_) -
https://twitter.com/RedTeamVillage_
Return to Index
SEV Village: Talk List
Home Page: https://www.se.community/
Sched Page: https://www.se.community/schedule/
DC Village Page: #sev
DC Forums Page: https://forum.defcon.org/node/248913
DC Discord Chan: https://discord.com/channels/708208267699945503/732733952867172382
Location: LVCC West/Floor 3/W317-W319 - Map
Social Media Links:
TW @sec_defcon
YT link
TI @se_community
LI @social-engineering-community
FB @Social-Engineering-Community-108883855139272

- Hours
- Friday: 08:30 – 18:00
Saturday: 10:00 – 18:00
Sunday: 10:00 – 14:00
- Location
- The Social Engineering Community Village will be in the LVCC West Hall rooms W317-319
Welcome to the Social Engineering Community! The SEC village focuses purely on the human aspect of security, Social Engineering, to enable people of all ages and backgrounds interested in the subject matter to have a venue to learn, discuss, and practice this craft.
This year, over three days at DEF CON, you can expect the following events to take place in the village:
- Vishing Competition (#SECVC): This edge-of-your-seat competition is where prior selected teams (who have already put WEEKS of work into the competition) place live phone calls inside a soundproof booth in front of SEC audience members to elicit as many objectives as possible. The highest score wins! This competition takes place only on Friday.
- Youth Challenge: Anyone 18 and under is invited to compete and learn about more than just Social Engineering; our challenges include areas in cryptography, network security, defusing intergalactic implosion bombs, and more. Can you stop the universe from imploding into what we’re assuming is probably another universe but much smaller? We hope so! Otherwise, even the dolphins will have to find a new home.
- Cold Calls: This event lets DEF CON attendees sign up in the village (first come, first serve style) to place live phone calls inside the soundproof booth. We provide the target and phone number, then give a few objectives (easy, medium, and hard), and start a countdown timer to see if they have the skills to get information from a stranger with no preparation. There is nothing to prepare for, just bring yourself!
- New: This year, we may have a couple more surprises up our sleeves – stay tuned and check out our website as it gets closer to DEF CON with our daily schedule!
Links: Website -
https://www.se.community/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248914
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248913
Return to Index
SOC Village: Talk List
DC Forums Page: https://forum.defcon.org/node/244769
Return to Index
TCV Village: Talk List
Home Page: https://telecomvillage.com/
Sched Page: https://telecomvillage.com/index.html#program-details
DC Village Page: #telecom
DC Forums Page: https://forum.defcon.org/node/248918
Location: LVCC West/Floor 2/W201 - Map
Social Media Links:
TW @TelecomVillage

The Telecom Village is a platform for anyone with an interest in both the offensive and defensive facets of telecom security. The village is where a variety of events, including talks, CTFs, and discussions centred on telecom security, take place. The Telecom Village’s primary focus would be on Telecom Security. We plan to host multiple hands-on events as part of the village to give participants an overview security specific challenges in a Telcom Network. This includes: CTFs in telecom signaling security and another one in Private 5G and select set of mini workshops and panels, spread across two days.
This Year we are planning to cover the following points Live4G/5G(SA) with Commercial BTS, internals and of a SIM Card, Simulating 4G/5G in a portal portable computing device, fundamentals of VoLTE/VoNR and its Attack vectors, MBSS for Telecom Security etc.
Telecom Security is an extremely focused and relatively closed domain within the Industry. We hope to bring this to a larger audience, ensure that they have a source which could act as a structure to facilitate learning and development in the sector. We will see larger adoption of Private 5G network across the globe and industries, which will come with it’s own set of unique challenges. We hope this village will play a key role is development and identification of key talents/projects which will help in tackling security challenges that plagues the telecom sector.
Links: Website -
https://telecomvillage.com/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248919
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248918
Twitter (@TelecomVillage) -
https://twitter.com/TelecomVillage
Return to Index
TEV Village: Talk List
DC Village Page: #tev
DC Forums Page: https://forum.defcon.org/node/248916
Location: LVCC West/Floor 1/Hall 2/HW2-07-03 - Map
"Tamper-evident" refers to a physical security technology that provides evidence of tampering (access, damage, repair, or replacement) to determine authenticity or integrity of a container or object(s). In practical terms, this can be a piece of tape that closes an envelope, a plastic detainer that secures a hasp, or an ink used to identify a legitimate document. Tamper-evident technologies are often confused with "tamper resistant" or "tamper proof" technologies which attempt to prevent tampering in the first place. Referred to individually as "seals," many tamper technologies are easy to destroy, but a destroyed (or missing) seal would provide evidence of tampering! The goal of the TEV is to teach attendees how these technologies work and how many can be tampered with without leaving evidence.
The Tamper-Evident Village includes the following contests and events:
- The Box; an electronic tamper challenge. An extremely realistic explosive with traps, alarms, and a timer ticking down. One mistake and BOOM, you're dead. Make every second count! Sign ups on-site when the TEV begins.
- Tamper-Evident King of the Hill; a full-featured tamper challenge. Tamper single items at your leisure and attempt to beat the current best. There can be only ONE! No sign ups required, play on-site when the TEV begins.
- Badge Counterfeiting Contest; submit your best forgery of a DEF CON human badge. Other target badges are also available for those looking for more counterfeit fun!
- For your viewing pleasure, collections of high-security tamper-evident seals from around the world.
- Presentations & demonstrations on various aspects of tamper-evident seals and methods to defeat them.
- Hands-on fun with adhesive seals, mechanical seals, envelopes, and evidence bags.
Links: Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248917
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248916
Return to Index
VMV Village: Talk List
Home Page: https://votingvillage.org/
DC Village Page: #voting
DC Forums Page: https://forum.defcon.org/node/248921
DC Discord Chan: https://discord.com/channels/708208267699945503/732733881148506164
Location: LVCC West/Floor 2/W223-W224 - Map
Social Media Links:
TW @votingvillagedc
YT link
TI @votingvillagedc
LI @election-integrity-foundation
IG @votingvillage?igsh=MWJreTh6dGl3eDEzNg==

The Voting Village is an interactive educational environment that provides the public with the unique opportunity to have hands-on experience with our current election infrastructure. Attendees will be able to interact with multiple different types of voting systems, all of which are currently in use across the country today. Hackers will have the opportunity to test how secure these voting systems truly are, and will report to the Voting Village Lead's any vulnerabilities they find. The Voting Village explores all aspects of election security and works to promote a more secure democracy.
Attendees of Voting Village will also have access to Harri Hursti, the world's premier hacker and leading election and cyber security expert who has successfully hacked voting machines on multiple occasions. Aside from Harri, attendees will have access to other experts as well as the option of joining us for our speaker track (TALKS) that will take place every day except for the last Sunday of DEF CON. Our speaker track represents the most relevant government agencies and the top media outlets. Additionally, there will be multiple showings of Harri's HBO documentary, Kill Chain: The Cyber War on America's Elections. We will also have two Capture The Flags (CONTESTS) taking place throughout DEF CON.
Due to it being a presidential election year, the focus on elections is going to be extremely heightened. Having an open research environment like the Voting Village helps offset the misinformation and disinformation that is rampant leading up to a presidential election. The Voting Village not only addresses election infrastructure related issues but also focuses on information integrity as a critical element of our election system. Our talks given by the most reputable subject matter experts cover all of these election related topics.
Links: Website -
https://votingvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248922
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248921
Twitter (@VotingVillageDC) -
https://twitter.com/VotingVillageDC
Return to Index
WS Village: Talk List
Home Page: https://defcon.org/html/defcon-32/dc-32-workshops.html
Sched Page: https://defcon.outel.org/defcon32/dc32-dc32-consolidated_page.html#villist_WS
Return to Index
XRV Village: Talk List
Home Page: https://xrvillage.org/
DC Village Page: #xrv
DC Forums Page: https://forum.defcon.org/node/248924
Location: LVCC West/Floor 1/Hall 4/HW4-01-06 - Map
Social Media Links:
TW @XRVillage
LI @xr-village
https://defcon.social/@xrvillage

Talks, playground for using XR tech, open bug hunt, bug bounty workshop, tech & art performances, VR gaming, and cross conference AR “Pokemon Go!” style collection experience. Federal agencies CISA and national laboratories Idaho & Pacific Northwest will be hosting interactive demos and an escape room in our space. They will be in collaboration with the ICS Village.
Workshop / Open Bug Hunt Pwn-a-Palooza (Collab with Hardware Hacking Village, Red Team Village)
The event is an open bug hunt with components of hardware hacking, XR rooted devices for workshop tie-in (VR headsets, glasses) and we are working with other villages and seeking support from industry pros to better direct the expectation of the hunt. We would like to offer prizing.
Playground
Open area for exploring emerging and existing XR tech; gaming, haptics, deconstructed devices to play with.
AR hunt / collection game
Collect village “stickers” throughout the con a la Pokemon Go! Style AR overlay that interacts with all the other villages at DEF CON. Think red mowhawks from Red Team Village, a viking from Adversary Village, a goat from OWASP, etc.
Links: Mastodon (defcon.social) -
https://defcon.social/xrvillage
Website -
https://www.xrvillage.org/
Discuss (DEF CON Forums) -
https://forum.defcon.org/node/248925
Sub-forum (DEF CON Forums) -
https://forum.defcon.org/node/248924
Return to Index
Speaker List
A-ISAC and Embry-Riddle Aeronautical University - Prescott
A-ISAC and Embry-Riddle Aeronautical University - Prescott
A-ISAC and Embry-Riddle Aeronautical University - Prescott
Aakin Patel
Aapo Oksman
Aaron "dyn" Grattafiori
Aaron Crow
Aaron Levy
Aaron Rosenmund
Aaron Shim
Abhijith “Abx” B R
Abhijith “Abx” B R
Abhinav Panda
Abhishek S
Abhishek S
Abraxas3d
Acid-T
Adam "_whatshisface" Pennington
Adam Batori
Adam Dobell
Adam Robbie
Adam Shostack
AdaZebra
Adel Karimi
Adnan Khan
Adrian Coleșa
Adrian Garcia
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adversary Village Crew
Adwiteeya Agrawal
Aeva Black
Aeva Black
Agostino Panico
Akib Sayyed
Akib Sayyed
Akib Sayyed
Alan Villaseñor
Alaric Becker
Alberto Rodriguez
Aleise McGowan
Alejandro Caceres
Alek Amrani
Alessandro Magnosi
alevsk
Alex Delifer
Alex Foley
Alex Gonzalez
Alex Kelly
Alex Kelly
Alex Kelly
Alexander Rubin
Alexandre CABROL PERALES
Alexandrine Torrents
Alexandrine Torrents
Alexandru Lazar
Alfie Champion
Allan "dwangoAC" Cecil
Allen Baranov
Alon Leviev
Alvaro Velasquez
Amal Joy
Amit Elazari
AMSAT
AMSAT
AMSAT
Amul Chaulagain
Ana Aslanishvili
Anand Tiwari
Anand Tiwari
Anant Shrivastava
AND!XOR
Andra
Andra
Andra
Andrew "DigitalAndrew" Bellini
Andrew Carney
Andrew Carney
Andrew Carney
Andrew Case
Andrew Johnson
Andrew M
Andrew Morris
Andrew Tierney
Andrzej Olchawa
Andrzej Olchawa
Angelina Tsuboi
Angelo Violetti
Angus Strom
Anjuli Shere
Ankita Gupta
Ankita Gupta
Ankur
Ankush Jain
Ankush Jain
Anna Bower
Anne Neuberger
Anthony “Coin” Rose
Anthony Hendricks
Anthony Kava
Antoine Carossio
Apurv Singh Gautam
Aquarious Workman
Aravind Prakash
Archwisp
AreTillery
Arjun Gopalakrishna
Armando Aguilar
Arnaud Soullié
Arnold Osipov
Arun Nair
Asher Davila
Asher Davila
Ashley Hiram M.
atlas
Aurora Johnson
Austin Carson
Austin Sellers
Ava Petersen
Avi Lumelsky
Avi McGrady
Aviad Hahami
Ayan Islam
Ayush RoyChowdhury
Babak Javadi
Barrett "pwneip" Darnell
Ben "NahamSec" Sadeghipour
Ben "NahamSec" Sadeghipour
Ben "NahamSec" Sadeghipour
Ben Dechrai
Ben Goerz
Ben Varcoe
ben@armosec.io
Benjamyn Whiteman
Bernhard Sedlmayer
BIC Village Staff
Bill Demirkapi
Bill Marczak
Bill Woodcock
Bill Woodcock
Bill Woodcock
Billy Graydon
Billy Graydon
bkobe
Blaine Jeffries
Blake Hudson
Bleon Proko
Bob Gourley
Bob Wall
Bobby R
Boeing
Boeing
Boeing
Borja Pintos Castro
Brad Proctor
Bradán Lane
Bradley Nash
Braelynn
Braelynn
Bramwell Brizendine
Brandon Colley
Brandon Colley
Brandon Dudley
Brett DeWitt
Brian Howard
Brian Weber
Bruna Shinohara de Mendonça
Bruna Shinohara de Mendonça
Bruno Krauss
Bryan Hance
Bryson Bort
Bryson Bort
C$
c0ldbru
Cale Smith
Call the Cops
CalPoly
CalPoly
CalPoly
CalPoly
CalPoly
CalPoly
Camilo Piñón Blanco
CaptHz
Carlos Fragoso
Carlota Bindner
Carson Zimmerman
Caspian Kilkelly
Cassie Crossley
Cassie Crossley
Cat Self
Catherine J. Ullman
Catherine J. Ullman
Catherine Terranova
Catherine Terranova
Catherine Terranova
CATO Networks
Cecilie Wian
Ceri Coburn
Cesar Ortega Ortega
Cesare Pizzi
Ch33r10
Chad Shortman
Changhyun Park
Chanin Kim
Charles "cfreal" Fol
Charles Waterhouse
Charles Waterhouse
Chirag Savla
Chloé Messdaghi
Chloé Messdaghi
Chloé Messdaghi
Chris Aniszczyk
Chris Cleary
Chris Davis
Chris Gates
Chris Poore
Chris Thompson
Chris Thompson
Chris Wysopal
Christian Dameff
Christiane Borges Santos
Christina Liaghati
Christine Lai
Christine Lai
Christophe Tafani-Dereeper
Claudi d’Antoine
Cliff Neve
Col Travis Hartman
Colbert Zhu
Colby Morgan
Constantine Nicolaidis
Constantine Nicolaidis
Cory Doctorow
Cory Doctorow
Cory Watson
Costume Contest
Costume Contest
Craig Chamberlain
Craig Lester
Cromulence
Cromulence
Cromulence
Cromulence
Cromulence
Cromulence
CT Cubed
CT Cubed
CT Cubed
CTRL / rsm
CtrlAltFu
Cyb0rg42
Cybelle Oliveira
Cybelle Oliveira
Cyrus Nikolaidis
Czesia Glik
Czesia Glik
Czesia Glik
Daemon Chadeau
Dafinga
Daiwei Zhu
Damien Cauquil
Dan "dan_kb6nu" Romanchik
Dan "dan_kb6nu" Romanchik
Dan Berte
Dan Goga
Dan Goga
Dan Gunter
Dan McInerney
Dani
Daniel "Blaklis" Le Gall
Daniel Ayzenshteyn
Daniel Beard
Daniel Bohannon
Daniel Cuthbert
Daniel Cuthbert
Daniel Isler
Daniel Messer
Daniel Miessler
Daniel Rohrer
Danilo Erazo
Danny Quist
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dark Wolf
Dave Scanlan
David "CountZ3r0" Roman
David "Icer" Maynor
David "Icer" Maynor
David Lo
David McDonald
David Meléndez
David Shandalov
David Sopas
David Weston
David Zito
deaddoll
Denis Smajlović
Dennis Giese
Dennis Giese
Dennis Giese
Deral Heiland
Derek DelGaudio
Deth Veggie
Devon Colmer
Dhiyaneshwaran Balasubramaniam
Dhruv Shah
Diego Jurado
Dillon Lee
Dimitri Di Cristofaro
Dirk-jan Mollema
DJ Habbs
DJ Roma
DJ Scythe
DJ St3rling
DJ Vulp
DotOrNot
Doug Kent
Dr. Andrew Fasano
Dr. David A. Wheeler
Dr. Fatou Sankare
Dr. Jennifer Roberts
Dr. Juel Tillman
Dr. Kathleen Fisher
Dr. Kosuke Onishi
Dr. Louis DeWeaver III
Dr. Matt Turek
Dr. Matthew Canham
Dr. Muhsinah Morris
Dr. Renee Wegrzyn
Dr. Stefanie Tompkins
Dr. Susan Coller Monarez
Dr. William (Bill) Butler
Dr. William Corvey
Drew "aNullValue" Stemen
Drew Green
Drew Green
Drew Green
Drew Springall
Drinor Selmanaj
Dual Core
Duane Michael
Duncan Woodbury
Dylan "The Magician" Baklor
Dylan Fox
Eddie Zaneski
Eduard Agavriloae
Eduardo Chavarro Ovalle
Ege Feyzioglu
eigentourist
Elad Pticha
Elad Pticha
Eli McRae
Elizabeth Biddlecome
Elizabeth Eigner
Elonka Dunin
Elonka Dunin
Emanuel Valente
Emile Fugulin
Emma Stewart
Emmanuel Goldstein
Emmanuel Law
Endeavors
Enoch Long
Enrique Nissim
Erez M Abrams
Eric Clay
Eric Clay
Eric Forte
Eric Lippart
Eric Woodruff
Erick Galinkin
Erick Galinkin
Erik Hunstad
Erika Cheung
Erwin Karincic
Escobar
ET
Eugene Rodionov
Evan Anderson
evildaemond (Adam Foster)
Exotrail
Exotrail
Exotrail
Ezra Woods
Ezz Tahoun
Ezz Tahoun
Ezz Tahoun
Ezz Tahoun
Ezz Tahoun
Ezz Tahoun
Faizan Ahmad
Federico Lucifredi
Felipe Pr0teus
Fernando De La Peña Llaca
Fernando Tomlinson
Filipi Pires
Filipi Pires
Filipi Pires
Fleur van Leusden
Florian Haag
Florian Haag
Francisco Canteli
Francisco Perdomo
Fred Wilmot
Gabriela (Gabs) Garcia
Gal Elbaz
Gareth Heyes
Gareth Heyes
Garrett Foster
Garrett Foster
Gaspard Baye
Gaspard Baye
Gastón Aznarez
Gastón Aznarez
Gaurav Joshi
Gautam Peri
General Paul M. Nakasone
Geoff Horvath
Giacomo Longo
Giglio
Giorgio "gbyolo" Bernardinetti
Golden Richard
Gonçalo Marques Raposo de Magalhães
Graham Helton
Greg Conti
Gregory Carpenter
Grey Fox
Grey Fox
Grey Fox
Grifter
Grind613
Grindhaus Selektor
Guillermo Buendia
Gunnar Andrews
Gustavo Moreira
Gustavo Roberto
Guy Amit
Gwyddia
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hack-A-Sat
Hahna Kane Latonick
Hallie Stern
Ham Radio Village Staff
Ham Radio Village Staff
Ham Radio Village Staff
Hamster
Hamster
Hanryeol Park
Hao Zheng
Hare Krishna Rai
Harlan Geer
Harley Geiger
Harley Wilson
Harley Wilson
Harley Wilson
Harri Hursti
Harri Hursti
Harri Hursti
Harriet Farlow
Harriet Farlow
Harriet Farlow
Harrison Richardson
Harry Coker Jr.
Harry Krejsa
Harsha Koushik
Harsha Koushik
Hayyan Ali
HD Moore
Heather Adkins
Heather Adkins
Helvio Carvalho Junior
Herming Chiueh
Himanshu Das
HK
hoodiePony
Hubert Lin
Hyo Jin Lee
Ian Carroll
Ian Foster
Ian G. Harris
Ian Hickey
Iceman
Icetre Normal
Iggy
Ignacio Daniel Navarro
Ignacio Daniel Navarro
Ike Marizu
Ilkin Javadov
ILOVEPIE
Ilyes Beghdadi
int eighty (of Dual Core)
IntelliGenesis and IG Labs
IntelliGenesis and IG Labs
IntelliGenesis and IG Labs
Inti De Ceukelaire
iosifache
Irvin Lemus
Isabel Manjarrez
Isabel Manjarrez
Isabel Straw
Isabella Barnett
Ismail Melih Tas
Itay Cohen
Ivan Evtimov
Jack Cyprus
Jack Heysel
Jack Rhysider
Jacob H Braun
Jacob H Braun
Jacob Oakley
Jacob Shams
Jad Meouchy
Jake “Hubble” Krasnov
Jake “Hubble” Krasnov
Jake Braun
Jake Braun
Jake Jepson
Jake Williams
James "albinowax" Kettle
James "albinowax" Kettle
James Hawk
James Howe
James Utley
Jamie Hardy
Jamie Williams
Jan Trzaskowski
Jannis Hamborg
Jared Dixon
Jared Dygert
Jared Dygert
Jason Butryn
Jason Clinton
Jason Craig
Jason Haddix
Jason Haddix
Jason Romero
Jasper Insinger
Jasper Insinger
Javan Rasokat
Jay Chen
Jay Chen
Jay Healey
Jay White
Jayson E. Street
Jayson E. Street
Jayson E. Street
Jeff "The Dark Tangent" Moss
Jeff "The Dark Tangent" Moss
Jeff "The Dark Tangent" Moss
Jeff "The Dark Tangent" Moss
Jeff "The Dark Tangent" Moss
Jeff Diecks
Jeff Foley
Jeff Foley
Jeff Guerra
Jeff Man
Jeffery Martin
Jeffrey Hofmann
Jeffrey Knockel
Jen Easterly
jen-ozmen
Jenko Hwong
Jennifer Guerra
Jeremy Banker
Jeremy
Jeremy
Jerome Wynne
Jerome Wynne
Jesika Juarez
Jessica Hoffman
Jessica Sexton
Jeswin Mathai
jgamblin
JiaQing Huang
Jim "Gurney" Ross
Jim Rush
Joan Arrow
Joanna Bitton
Joe "Kingpin" Grand
Joe "securelyfitz" FitzPatrick
Joe Slowik
Joe Slowik
Joe Vest
Joel "Niemand_Sec" Noguera
Johannes Willbold
John "2PAC" Smithberger
John Rodriguez
John Rodriguez
John Rodriguez
John Rodriguez
John Stawinski
John Threat
Johnathan Kuskos
Jon DiMaggio
Jon Marler
Jonathan "JBO" Bar Or
Jonathan Fischer
Jonathan Leitschuh
Jonathan Leitschuh
Jonathan Reiter
Jonathan Waterman
Jonghyuk Song
Jordan Kasper
Jorge Acevedo Canabal
Jose Plascencia
Joseph Cox
Joseph Cox
Joseph
Josh Huff
Josh Isaac
Josh Izaac
Josh Kamdjou
Josh Pyorre
Josh Stroschein
Josh Stroschein
Josh Summitt
Joshua Herman
Joshua HIll
Julia Dewitz-Würzelberger
Julien Terriac
Just Tulpa
Justin "Rhynorater" Gardner
Justin "Rhynorater" Gardner
Justin Mott
Justin Wynn
Justin
Jyoti Raval
Kaitlyn Handelman
Kaleeque Pierce
Kaloyan Velikov
Kamikazi
Kampf
Karan Dwivedi
Karen Ng
Karen Ng
Karen Ng
Karen Ng
Karl Fosaaen
Karthik Tadinada
Kasimir Schulz
Kasimir Schulz
Kasimir Schulz
Kasimir Schulz
Katherina Canales
Kathy Zhu
Katie Trimble-Noble
Kellee Wicker (Moderator)
Kemba Walden
Ken Gannon
Ken Kato
Ken Kato
Ken Munro
Ken Munro
Ken Munro
Ken Pyle
Ken Pyle
Ken Pyle
Kendall Spencer
Kendall Spencer
Kenneth Ellington
Kent Britain
Kent Wilson
Kent Wilson
Kerry-Ann Barrett
Kevin "Kent" Clark
Kevin "Kent" Clark
Kevin Manna
Kevin Mitchell
Kevin Parker
Kirk Trychel
Kirk Trychel
Kirsten Renner
Kivanc Aydin
Klaus Schmeh
Klaus Schmeh
Kody K
Kody K
Kody K
Kody K
Kody K
Kody K
Kody K
Kody K
Kody K
Kody K
Konstantinos Karagiannis
Konstantinos Papapanagiotou
Krzysztof Okupski
Kuan-Ting "HexRabbit" Chen
Kunal Bhattacharya
kvprashant
Kyle McMillan
Kyle Murbach
Lacey Harbour
Langston Clement
Langston Clement
Larry Pesce
Lauren Proehl
Lauren Putvin
Lee McWhorter
Leigh-Anne Galloway
Leigh-Anne Galloway
Leigh-Anne Galloway
Leigh-Anne Galloway
Leigh-Anne Galloway
Lenin Alevski
Lenin Alevski
Lenin Alevski
Lenin Alevski
Lennert Wouters
Leo Tsaousis
Leon Derczynski
Leon Derczynski
Leonardo Pigñer
Leonardo Serrano
Leonidas Vasileiadis
Levone Campbell
Lexie Thach
Lillian Ash Baker
Liv Matan
Lockheed Martin
Lockheed Martin
Lockheed Martin
Logan MacLaren
Lorenzo Grazian
Lorenzo Pedroncelli
Lozaning
Luca "CYBERANTANI" Bongiorni
Luca "CYBERANTANI" Bongiorni
Luca "CYBERANTANI" Bongiorni
Lucas Cioffi
Lucas Philippe
Lucas Philippe
Lucas Potter
Lucas Rooyakkers
Luciano Remes
Luigi Cruz
Lukas McCullough
Luke Koch
Luke McLaren
Lynn Hamida
m1ddl3w4r3
Magik Plan
Manfred
Manvell Lessane
Mar Williams
Marcelo Ribeiro
Marco Figueroa
Marcus Hutchins
Mariia Mykhailova
Marilyn Marks
Mário Leitão-Teixeira
Mário Leitão-Teixeira
Mário Leitão-Teixeira
Mário Leitão-Teixeira
Mark Foudy
Mark Griffin
Mark Mager
Mark Perry
Mark Perry
Mars Cheng
Martin Doyhenard
Martin Doyhenard
Martin Petran
Martin Pratt
Martin Rakhmanov
Martin Strohmeier
Martin Strohmeier
Martin Strohmeier
Mary Kaiser
Matei Josephs
Matheus Eduardo Garbelini
Matt Blaze
Matt Blaze
Matt Burch
Matt Burch
Matt Burrough
Matt Domko
Matt Gaffney
Matt Hazelett
Matt James
Matt Knight
Matt Knight
Matt Mayes
Matt Mayes
Matt Pawloski
Matt Thomassen
Matthew "mandatory" Bryant
Matthew Dixson
Matthew Handy
Matthew Nickerson
Matthew Richard
Matthias Göhring
Matthias Göhring
mattrix
Mauro Eldritch
Mauro Eldritch
Mauro Eldritch
Max "Libra" Kersten
Max "Libra" Kersten
Maya Pavlova
MC Frontalot
mcdwayne
mcdwayne
mcdwayne
Meaghan Neill
Megan Squire
Melanie Allen
Melvin Langvik
Meow-Ludo Disco Gamma Meow-Meow
Micah Silverman
Michael "codingo" Skelton
Michael "mtu" Torres
Michael "v3ga" Aguilar
Michael "v3ga" Aguilar
Michael Brown
Michael Butler
Michael Dascal
Michael Donley
Michael Garcia
Michael Gorelik
Michael Katchinskiy
Michael Moore
Michael Moore
Michael Orlitzky
Michaela Barnett
Michal Grygarek
Michelle Eggers
Mika Devonshire
Mike Holcomb
Mike Holcomb
Mike Larkin
Mike Manrod
Mike Raggo
Mike Ruth
Mike Walker
Mike Weigand
Mikey Awbrey
Mikhail Shcherbakov
Mishaal Khan
Mishaal Khan
Miss Jackalope
Mixæl Swan Laufer
Mixæl Swan Laufer
Mohammed Ilyas Ahmed
Mohit Tiwari
Mona Wang
Moritz Abrell
Moritz Laurin Thomas
Moritz Laurin Thomas
Moses Frost
Moses Frost
Muhammad Mudassar Yamin
Mulong Luo
muteki
Myeonghun Pak
Myeongjin Shin
N8
Nadeem Bagwan
Nader Zaveri
Naomi Brockwell
Nasreen Djouini
Natalie Simpson
Nate Young
Nate Young
Nathan Case
Nathan Sidles
Nestor Sánchez
Neumann "scsideath" Lim
NG Yeow Boon
Nia Luckey
Nick Aleks
Nick Aleks
Nick Ascoli
Nick Ascoli
Nick Draffen
Nick Frichette
Nick Frichette
Nick Halt
Nick Landers
Nick McClendon
Nick Warner
Nicole Beckwith
Nicole DeCario
Nicole DeCario
Nicole Tisdale
Nicole Tisdale
Nikhil "niks" Shrivastava
Nikhil "niks" Shrivastava
Nikhil Mittal
Nikita Kronenberg
Nikki Pope
Nikkia Henderson
Nikkia Henderson
Niklas Lindroos
Nina Alli
Nina Bindel
Ninjula
Niru Ragupathy
Nitin Natarajan
Nivedita (Nivu) Jejurikar
Niyo Little Thunder Pearson
Noah Lazzaro
Numan Ozdemir
O'Craven Celtic Pirate Band
Océane Thieriot
Octavio Gianatiempo
Octavio Gianatiempo
Ofek Itach
Ofir Yakobi
Ohm-I & The NPC Collective
Omar Santos
Omar Santos
Omar Santos
Omar Santos
Omenscan
Or Sahar
Or Yair
Oreen Livni
Oreen Livni
Ori David
Ori Ron
Ori Ron
Ori Ron
overcast
Özgün Kültekin
PankleDank
PatAttack
Patrick “Lord Digital” Kroupa
Patrick Eisenschmidt
Patrick Kiley
Patrick Walsh
Paul Brownridge
Paul Gerste
Paul Roberts
Paul Vixie
Paul Wortman
Paulino Calderon
Paulo A. Silva
Pavel Khunt
Peiter “Mudge” Zatko
Peiyu Wang
Pen Test Partners
Pen Test Partners
Pen Test Partners
Per Thorsheim
Perri Adams
Perri Adams
Perry Carpenter
Pete Ortega
Pete Stegemeyer
Phil Rhodes
Philip Acosta
Philip Stark
Philip Stark
Philip Stark
Prashant Venkatesh
Prince Chaddha
Priyanka Joshi
punkcoder
Quentin Fraty
R.J. McCarley
r1otctrl
R4v3n Bl4ck
Rachael Tubbs
Rachel Cummings
Rachel Cummings
Rachel Murphy
Rachel Murphy
Ralph May
Ralph May
Ram Ganesh
Ram
Randi Tinney
Randy Belbin
Randy Pargman
Randy Pestana
Raunak Parmar
Ravid Mazon
Ravid Mazon
Ravin Kumar
Ray Baeza
Ray Baeza
RC Jones
Rebecca Ford
Rebecca J. Rohan
Rebecca Lively
RedHunt Labs (Kunal)
Relay
Remy DeCausemaker
Renée DiResta
Rewanth Tammana
Rey "Privesc" Bango
RF Hackers
RF Hackers
RF Hackers
Ricardo L0gan
Rich DeMillo
Rick Altherr
Ricky "HeadlessZeke" Lawshae
Rik Chatterjee
Rob Joyce
Rob King
Robert Ditmer
Robert Landavazo
Robert Pafford
Robert Pimentel
Robert Van Etta
Roberto Rodriguez
Roberto Soares
Robin Bisping
Rodney David Beede
Roger Dingledine
Rohit Pitke
Romain Cayre
Ron Ben-Yizhak
Ron Fabela
Ronald Broberg
Ronald Gonzalez
Roni "Lupin" Carta
Roni "Lupin" Carta
Rotem Bar
Roy Weiss
RTV Staff
RTV Staff
RTV Staff
Rudy Mendoza
Ruoyu "Fish" Wang
Rupali
Russ McRee
Ryan Barnett
Ryan Chapman
Ryan Chapman
Ryan Holeman
Ryan Johnson
Ryan M. "0dayCTF" Montgomery
Ryan O'Donnell
Ryan O'Donnell
Ryan Rutan
Ryan Tracey
S1nn3r
Sabajete Elezaj
Salvador Mendonza
Sam "Frenchie" Stewart
Sam (erbbysam) Erb
Sam Bowne
Sam Cosentino
Sam Curry
Sam Mayers
samy kamkar
Sandra Stibbards
Sanne Maasakkers
Sara Attarzadeh
Sarah Hipel
Sarah Mader
Sarah Novotny
Sarthak Taneja
Sarthak Taneja
Savannah "lazzslayer" Lazzara
Savannah "lazzslayer" Lazzara
Scotch & Bubbles
Scott Helme
Scott Weston
Sean
Sean McGregor
Sean McGregor
Sean McKeever
Sean Metcalf
Sean Oesch
Sebastiaan Pierrot
Sebastian Cesario
Sebastian Tapia De la torre
Sebastien Tricaud
Senior Representative from UK NCSC
Serrgei Frankoff
Seth Art
Seth
Seunghee Han
Shahar Man
Shane McFly
Shawn Abelson
Shea Nangle
Shea Nangle
Shebin Mathew
SheHacksPurple
Shelly Giesbrecht
Shina Liu
Shir Sadon
Shishir Gupta
Shiva Shashank Kusuma
Shmuel Cohen
Shourya Pratap Singh
Shubham
Silvia Puglisi
Sim Cher Boon
Simone Stephen
SIV
Skittish and Bus
Soledad Antelada Toledano
Solomon Sonya
Soohwan Oh
Sorin Boloș
Spencer McIntyre
Spyros Gasteratos
Squiddy
Stephan Viljoen
Stephen Sims
Steve Dossey
Steve McGregory
Steven Sheffield
Sting
Stitcharoo
Stryker
Stryker
Stuart Wagner
Subho Majumdar
Sudhanshu
Sudipta Chattopadhyay
Suha Sabi Hussain
Suneel Sundar
Susan Greenhalgh
Susan Greenhalgh
Suzanne Borders
Sven Cattell
Sven Cattell
Sven Cattell
Sydney Johns
Sydney Johns
Sydney Marrone
Syed Aamiruddin
Syntax (DJ) + Luna (VJ)
Tailor Tolliver
Tal Folkman
Tal Folkman
Tal Folkman
Talk Sinn
Tarah Wheeler
Tarun Koyalwar
Ted Harrington
Tejas Patel
Tennisha Martin
Tennisha Martin
Terry Luan
th3CyF0x
The Glad Scientist
the gumshoo
The_Gibson
TheTechromancer
Thiago Bordini
Thiago Bordini
Thomas "Cr0wTom" Sermpinis
Thomas "Cr0wTom" Sermpinis
Thomas "stacksmashing" Roth
Thomas Boejstrup Johansen
Thomas Roccia
Thomas Roccia
Thomas X Meng
Tiernan "nvx" Messmer
Tim Chase
Tim Clevenger
Tim Clevenger
Tim Fowler
Tim Roberts
Timm Lauser
Tina Schneibs
Tina Velez
Todd Fletcher
Tom "Decius" Cross
Tom Boner
Tom Porter
Tom VanNorman
Tom VanNorman
Tomais Williamson
Tomer Peled
TommydCat
Tony Sager
Travis Weathers
Trey Bilbrey
Trey Bilbrey
TRIODE
Tristan Kalos
Troy Defty
Troy Defty
Trupti Shiralkar
TSA
TSA
TSA
TX
Tyler Casey
Ueric Melo
UK Repersentative 2
Utku Yildirim
Vadim Makarov
Vangelis Stykas
Vangelis Stykas
Varjitt Jeeva
Victor Fernandez Minguillon
Victor Pasknel
Victor Santos
Vikas Khanna
Viktor Gazdag
Vincent Lenders
Vincent Lenders
Vincent Sloan
Vinnie "kernelpaniek" Vanhoecke
Vinod Shrimali
Vishal Thakur
Vivek Ramachandran
Vivek Ramachandran
Vivek Ramachandran
Vivek Ramachandran
Vladyslav Zubkov
Vladyslav Zubkov
Wade Cappa
Walter J. Scheirer
Walter Scheirer
Wan Ding Yao
Wang Zhilong
WangJunJie Zhang
Wesley McGrew
Wesley McGrew
Wesley McGrew
WiGLE Staff
Will Baggett
Will Pearce
Will Pearce
William Loomis
William Phillips
William Taylor
Willis Vandevanter
Winson Tam
Woody
Wooseok Kim
Wouter Veenstra
Wyatt Ford
X
Xavier "rubix1138" Ashe
Xavier D. Johnson
Xavier Palmer
Xavier Zhang
Xiling Gong
Xinzhi Luo
xray
Xuan Xing
Yael Grauer
Yakir Kadkoda
Yan "Zardus" Shoshitaishvili
Yariv Tal
YiSheng He
Yisroel Mirsky
Yoann Dequeker
Yossi Pik
Yossi Pik
Yossi Pik
YTCracker
YTCracker
Yue Liu
Yurii Zadoianchuk
Zachary Stein
Zaire Moore
Zander Mackie
ZEE
Zibran Sayyed
Zoziel
ᗩᒪETᕼE
Talk List
"BYOCTF" - Bring Your Own [Challenges||Capture] The Flag - BICV
(|(MaLDAPtive:¯\_(LDAP)_/¯=ObFUsc8t10n) (De-Obfuscation &:=De*te)(!c=tion)) - DC
0.0.0.0 Day: Exploiting Localhost APIs From The Browser - APV
3D Printing My Way to Sanity: The Self-Funding Hobby That Changed Everything - MISC
3DU: Homo (e)x Machina - BHV
4G Frenzy - TCV
5G Fortress - TCV
5Ghoul Framework - 5G NR Attacks & 5G OTA Fuzzing - DL
A Bug Hunter's Guide to Account Takeover - BBV
A dive into world of Aircraft PKI - ASV
A Hacker's guide to PQC - QTV
A hole in one: pwning a cruise ship from a golf simulator and other tales of maritime IT-OT misconvergence - ICSV
A Reverse Engineer's Guide to AI Interpretability - AIxCC
A Shadow Librarian in Broad Daylight: Fighting back against ever encroaching capitalism - DC
A Short Introduction to 802.11ah Long Range WiFi HaLow with TaiXin TXW8301 devices - RFV
A Treasure Trove of Failures: What History’s Greatest Heist Can Teach Us About Defense In Depth - DC
A Whirlwind Tour of the FBI's Secret Encrypted Chat App - CPV
A Zero to Hero Crash Course to Server-Side Request Forgery (SSRF) - BBV
A-ISAC Aviation Cybersecurity Challenge - ASV
A-ISAC Aviation Cybersecurity Challenge - ASV
A-ISAC Aviation Cybersecurity Challenge - ASV
Abusando de Bitlocker para secuestrar información corporativa | Desde la intrusión hasta el descifrado (i) - MISC
Abusing DevOps to Pivot Between Cloud and On-Prem - RTV
Abusing legacy railroad signaling systems - DC
Abusing Windows Hello Without a Severed Hand - DC
Access Control Done Right the First Time - PSV
Access Control done right the first time - PSV
ACE up the Sleeve: From getting JTAG on the iPhone 15 to hacking into Apple's new USB-C Controller - DC
Activity: API Security 101: Testing and Trivia by Akto.io - APV
Activity: API Security 101: Testing and Trivia by Akto.io - APV
Activity: Capture the Container by Chainguard - APV
Activity: Capture the Container by Chainguard - APV
Activity: Hacking Developers’ Trust – Faking GitHub Contribution by Checkmarx - APV
Activity: Hacking Developers’ Trust – Faking GitHub Contribution by Checkmarx - APV
Activity: Spot the Reachable by Backslash - APV
Activity: Spot the Reachable by Backslash - APV
Activity: Spot the Reachable by Backslash - APV
Activity: Spot the Secrets: Finding Secrets Throughout Your Environments by GitGuardian - APV
Activity: Spot the Secrets: Finding Secrets Throughout Your Environments by GitGuardian - APV
Activity: Spot the Secrets: Finding Secrets Throughout Your Environments by GitGuardian - APV
Activity: Test Your AppSec Knowledge by Deepfactor - APV
Activity: Threat modelling fun session with OWASP Cornucopia - APV
Activity: Threat modelling fun session with OWASP Cornucopia - APV
Activity: Vulnerability Hunt - The Snippets Edition - APV
Activity: Vulnerability Hunt - The Snippets Edition - APV
Advanced Packet Radio Operation - HRV
Adventures in Android Triage Collection - BTV
Adversarial AI: Disrupting Artificial Intelligence with Style - ADV
Adversary Simulation: Using Blue Eyes to See Red - RTV
Adversary simulator and purple teaming hands-on booth - ADV
Adversary simulator and purple teaming hands-on booth - ADV
Adversary simulator and purple teaming hands-on booth - ADV
Adversary Village keynote kick-off panel - ADV
Adversary-Adventure Table-top Game - ADV
Adversary-Adventure Table-top Game - ADV
Adversary-Adventure Table-top Game - ADV
Advocating for an Inclusive Cyber-Civil Rights Policy Agenda for Vulnerable Communities - PLV
AI Village Day 1 Keynote – Poison, injection, evasion, oh my! Grounding AI security threats in data driven reality - AIV
AI-Driven Cyber Resilience: Surviving the 5G Threat Landscape - TCV
AI’ll be watching you. Greybox Attacks against an Embedded AI - AIV
Ain’t that a Breach: Zero Trust Is the Only Solution! - BICV
AIxCC Closing Ceremonies - DC
All Your Keyboards Are Belong to US! - DC
AMA on Proxmark3 with Iceman - RFV
AMD Sinkclose: Universal Ring -2 Privilege Escalation - DC
Amenaza persistente: UXHIL y la propagación de URSA - MISC
An adversarial approach to Airline Revenue Management Proving Ground - ASV
An Operator's Guide: Hunting SCCM in the Real World - RTV
Analyzing the Security of Satellite-Based Air Traffic Control - ASV
Android App Usage and Cell Tower Location: Private. Sensitive. Available to Anyone? - DC
Anyone can hack IoT - a beginner’s guide to hacking your first IoT device - IOTV
Application Threat Modeling with Trike - APV
AR + Art = interactive installations to bring your stories to life - XRV
Area DC32: An Interactive Tabletop Takes Flight (A BTV Panel) - BTV
ARINC 664 CTF - ASV
ARINC 664 CTF - ASV
ARINC 664 CTF - ASV
Arsenal: AI Goat - APV
Arsenal: CyberChef like Automation within BurpSuite - Let's get cooking with the CSTC - APV
Arsenal: GraphQL Armor - Open Source GraphQL Security - APV
Arsenal: HunterBounter - Swiss Army Knife for Bug Bounty - APV
Arsenal: Introducing RAVEN - Discovering and Analyzing CI/CD Vulnerabilities in Scale - APV
Arsenal: Kubescape - OSS security from left to right and everything in the middle - APV
Arsenal: SanicDNS - APV
Arsenal: SCAGoat - APV
Ask Me Anything - Daniel Cutberth, Moderated by Sudhanshu - RCV
Atomic Honeypot: A MySQL Honeypot That Drops Shells - DC
Attack and Defence in OT - Simulating attacks against hydroelectric power plants leveraging ICS Firing Ranges - ICSV
Attack Vectors of Quantum Computers - QTV
Attacking and defending card present transactions - PYV
Attacking and Defending Software Supply Chains: How we got Admin in your Clouds! - CLV
Attacks on GenAI data and using vector encryption to stop them - CPV
Automated Control Validation with Tommyknocker - DL
automobiles, alcohol, blood, sweat, and creative reversing of an obfuscated Car-Modding tool - DC
Aviation cybersecurity lightning talk: Three topics in thirty minutes - ASV
AWS CloudQuarry: Digging for secrets in public AMIs - DC
Badge Cloning: A Penetration Tester's Guide to Capturing and Writing Badges - RTV
Basic Mobile Phone Privacy - CPV
Basic Mobile Phone Privacy - CPV
Basic Packet Radio Operation - HRV
Bastardo Grande: Hunting the Largest Black Market Bike Fence In The World - RCV
Be Latino in Cybersecurity on markets outside LATAM - MISC
Be the Ghost in the Shell Barrier Mazes FTW - XRV
Behind Enemy Lines: Engaging and Disrupting Ransomware Web Panels - DC
Behind Enemy Lines: Going undercover to breach the LockBit Ransomware Operation - DC
Behind the Badge: How we used and abused hardware to create the AV badge for DC32 - ASV
Bespoke C2s are coming of age. - RTV
Beyond Sunset: Exposing the Occultations Lurking in Large-Scale Off-Grid Solar Systems - IOTV
BIC United Kingdom Chapter Informational Virtual Opening Session - BICV
BIC Village Keynote: Cyber Threat Landscape And Law Enforcement - BICV
BIC Village Opening Q&A with Marcus Hutchins - BICV
Blacks in Cyber Lituation 2.0 - SOC
Blue Goes Purple: Purple Teams for Fun and Profit (A BTV & RTV Panel) - RTV
Blue Team Careers: Do what you love, get paid for it! (A BTV Interactive Panel) - BTV
Bluetooth Blues: Unmasking CVE 2023-52709 - The TI BLE5-Stack Attack - CHV
Bluetooth Landscape Exploration & Enumeration Platform (BLEEP) - DL
BOAZ, Yet Another layered Evasion Tool: Unveiling the Secrets Behind Antivirus Testing - RTV
Bogus Badges: The Art and Innovation of Badge Counterfeiting - PSV
BOLABuster: Harnessing LLMs for Automating BOLA Detection - AIV
BOLABuster: Harnessing LLMs for Automating BOLA Detection - APV
Book Signing: Visual Threat Intelligence: An Illustrated Guide for Threat Researchers - MISC
Breaching AWS Accounts Through Shadow Resources - DC
Breaking and Defending Cloud Infrastructure: Red Team Evasion Tactics and Access Control Solutions - DCGVR
Breaking Boundaries: Popping Shells in the Airgap with $10 and a Dash of Arduino Magic - BHV
Breaking Secure Web Gateways (SWG) for Fun and Profit - DC
Breaking software protected crypto implementations - PYV
Breaking the Beam: Exploiting VSAT Satellite Modems from the Earth's Surface - DC
Breaking Through Election Myths - VMV
Bricked & Abandoned: How To Keep The IoT From Becoming An Internet of Trash - DC
Bridging Space and Medicine - BHV
Bridging the Experience Gap in Machine Learning Security - AIV
Bridging the Gap: How the American Legion Provides Veterans with a Sense of Belonging and Support - MISC
Brief History of GRC - DCGVR
Bringing Down North Korea - DC
BTV Conversations: Exploring the Cyberpsychology of Cyber Defender Acceptance Behaviors and Personality Traits - BTV
BTV Conversations: Touch Grass to Combat Burnout - BTV
Building a Cyber Threat Intelligence Program from scratch for free! - BTV
Building a foundation with the 5 critical controls - ICSV
Building a secure and resilient nationwide EV charging network: the role of hackers in the clean energy revolution - CHV
Building Surgical Implants: A Comprehensive Guide to APT-style Techniques - RTV
Building the Ultimate Budget-Friendly Low Earth Orbit Satellite Ground Station - ASV
Building Your Red-Teaming Co-Pilot: Navigating the New Cyber Era with Pretrained Gen-AI - RTV
Building Zero Trust in ICS - ICSV
BYOS – Bring Your Own Satellite - ASV
Bypass 101 - PSV
Bypass 101 - PSV
Bypass 101 - PSV
Bypass 102 - PSV
Bypassing Corporate controls on Mac Devices - RTV
Bypassing WHOIS Rate Limiting and Alerting on Fresh Enterprise Domains - RCV
BypassIT - Using AutoIT & Similar Tools for Covert Payload Delivery - DL
Caido Internals Deep-Dive - BBV
Career Development - The Human Element - ICSV
Case Study: Hacking Smart Lock For Fun and Profit - MISC
Catch them all! Detection Engineering and Purple Teaming in the Cloud - CLV
Challenges and Reactions: Cybersecurity and Communications Resilience in Taiwan - PLV
Changing Global Threat Landscape with Rob Joyce and Dark Tangent - DC
Chatbots for Cybersecurity - MISC
Choose your own adventure: Has your fleet been hacked? - ASV
Clapping cheeks, aka home brew antennas - HRV
Clash, Burn, and Exploit: Manipulate Filters to Pwn kernelCTF - DC
Closing the Software Vulnerability Gap - AIxCC
Cloud Native Security Platform for Defenders - BTV
Cloud Offensive Breach and Risk Assessment (COBRA) - DL
Cloud Offensive Breach and Risk Assessment (COBRA) - CLV
Cloud Offensive Breaches: The Graph-Based Exploitation of Misconfigurations - RTV
Cloud Tripwires: fighting stealth with stealth - CLV
CODASM - Hiding Payloads in Plain .text - DL
Cognative Weather Report - VMV
Color Blasted Badge Making: How Hard Could It Be ? - MISC
Combining Uncensored and Censored LLMs for Ransomware Generation - RTV
Compromising an Electronic Logging Device and Creating a Truck2Truck Worm - DC
ConfusedPilot: Data Corruption and Leakage by Misusing Copilot for Microsoft 365 - AIV
Connecting the Dots: Mastering Alert Correlation for Proactive Defense in the Cloud - CLV
Contextualizing Open Source Software’s Importance to CISA's Mission - AIxCC
CopyCat: An Artist Guide to Adversary Forgery - ADV
Correlating & contextualizing OT events/alerts/logs using weakly supervised AI - ICSV
Correlating slow & stealthy APT traces hiding in the sheer noise - ADV
Countdown to Industrial Extinction - ICSV
Covert Quantum Communication - QTV
Creating Azure Policy Compliant Backdoor - CLV
CTI is Dead, Long Live CTI: Reassessing Blue Team's Squishiest Value Proposition (BTV Panel) - BTV
CubeSat Simulator - ASV
CubeSat Simulator - ASV
CubeSat Simulator - ASV
CULT OF THE DEAD COW & Friends Present: Prime Cuts from Hacker History - 40 Years of 31337 - DC
Current EW techniques - RFV
Custom, cheap, easy, and safe badges - without starting from scratch - DC
Cyber Informed Engineering for Critical Infrastructure - ICSV
Cyber Security Transformation Chef (CSTC) - DL
Cyberjutsu Path to a Digital Martial Art - ADV
Cybersecurity for Emerging Tech (panelists would include researchers or industry executives in emerging tech categories, like space, OT, hardware like drones, etc) - MISC
Cybersecurity for Veterans: Bridging the Gap from Military to Civilian Careers - MISC
Cybersecurity Overview over LATAM- Skills, Challenges, Knowledge, Perspectives - MISC
Cybersecurity Schoolhouse Rock - PLV
D0N0H4RM: Cyber STEM Storytime - BHV
DarkGate: Cazando a la amenaza y exponiendo su infraestructura - MISC
Darkstar Badge Challenge - ASV
Darkstar Badge Challenge - ASV
Darkstar Badge Challenge - ASV
Data Brokers and the Threat to Your Privacy - CPV
Data On Demand: The challenges of building a privacy focused AI Device - CPV
DC NextGen / Youth Challenge Area at Red Team Village - RTV
DC NextGen / Youth Challenge Area at Red Team Village - RTV
DC NextGen / Youth Challenge Area at Red Team Village - RTV
DC101 Panel - DC
De Escudo a Espada: Cómo un Antivirus Facilitó el compromiso de una compañía - MISC
Deception & Counter Deception – Defending Yourself in a World Full of Lies - DC
Decoding Galah, an LLM Powered Web Honeypot - PHV
DEF CON Academy: Cultivating M4D SK1LLZ In the DEF CON Community - DC
DEF CON Closing Ceremonies & Awards - DC
DEF CON Franklin Project - DC
DEF CON Groups Panel #1 - DCGVR
DEF CON Unplugged: Cocktails & Cyber with Jeff & Jen - DC
Defeating EDR Evading Malware with Memory Forensics - DC
Defeating magic by magic:Using ALPC security features to compromise RPC services - DC
Defend the Airport CTF - ASV
Defend the Airport CTF - ASV
Defend the Airport CTF - ASV
Democracy From Around the World - VMV
Detección de Vulnerabilidades mediante Instrumentación y su Explotación - MISC
Detect a Threat - ASV
Detect a Threat - ASV
Detect a Threat - ASV
Detouring Danger: Hunting Privileged File Operation Vulnerabilities in OT/ICS software - ICSV
Developing Better Payloads with Automated Testing - RTV
Developing Evilginx Phishlets - RTV
Differential privacy beyond algorithms: Challenges for successful deployment - CPV
Digital Emblems: When markings are required under international law, but you don’t have a rattle-can handy - DC
Discovering and exploiting local attacks against the 1Password MacOS desktop application - DC
Disenshittify or die! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification. - DC
distribRuted - Distributed Attack Framework - DL
Docker Exploitation Framework - DL
Does the World Need Another Threat Model, the Road to EMB3D - ICSV
DoH Deception: Evading ML-Based Tunnel Detection with Black-Box Attack Techniques - RTV
Don't Give Up The Ship! Maritime SOC/NOC Afloat - ICSV
Don't go too far… your job is not done! - MISC
Don't Ship Your Bridges! Tools to Explore Wireless Attack Surfaces in Every Ship's Marine Navigation Systems - ICSV
Doors, Cameras, & Mantraps: Oh my! - LPV
DoorSim - making my conference travel easier - RFV
Dragon SlayingGuide: Bug Hunting In VMware Device Virtualization - DC
DriverJack: Turning NTFS and Emulated Read-only Filesystems in an Infection and Persistence Vector - DC
Drone Capture the Flag (CTF) - ASV
Drone Capture the Flag (CTF) - ASV
Drone Capture the Flag (CTF) - ASV
Drone Flying Experience - ASV
Drone Flying Experience - ASV
Drone Flying Experience - ASV
Drone Hacking Activity - ASV
Drone Hacking Activity - ASV
Drone Hacking Activity - ASV
Drone Hacking Choose Your Own Adventure - ASV
Drone Hacking Choose Your Own Adventure - ASV
Drone Hacking Choose Your Own Adventure - ASV
Drop-Pi - DL
Dysfunctional Unity: The Road to Nowhere - BHV
Efficient Bug Bounty Automation Techniques - BBV
Election 2024 Freedom of Choice: A Psybernomic Conundrum - VMV
Emulating Magstripe with Arduino - PYV
Emulating Magstripe with Arduino - PYV
Encrypted newspaper ads in the 19th century - The world's first worldwide secure communication system - DC
Engineers & Exploits: The Quest for Security - APV
Epyon - Attacking DevOps environments - CLV
Eradicating Hepatitis C With BioTerrorism - DC
Eradicating Hepatitis C With BioTerrorism - BHV
Establishing the first Open Source Program Office at a United States Federal Agency - AIxCC
Evading Modern Defenses When Phishing with Pixels - ADV
Evaluations and Guardrails against Prompt Injection attacks on LLM powered-applications - AIV
Evolution of RF Signal Visualization - From Spectrum Analyzers to Augmented Reality - XRV
Expanding Pathways into the National Cyber Workforce - BICV
Exploit K8S via Misconfiguration .YAML in CSP environments - CLV
ExploitIfNotExists: Privilege Escalation & Persistence with Azure Policy - CLV
Exploiting Bluetooth - from your car to the bank account$$ - CHV
Exploiting Bluetooth - from your car to the bank account$$ - DC
Exploiting common vulnerabilities in AWS environments - CLV
Exploiting insecure OTA updates to create the worlds first Toothbrush Botnet and selfreplicating ESP32 worm - RFV
Exploiting the Unexploitable: Insights from the Kibana Bug Bounty - DC
Exploiting Voice Cloning in Adversarial Simulation - ADV
Exploration of Cellular Based IoT Technology - IOTV
Exploring Bias in AI-Assisted News - BICV
Exploring the Cosmos: Hackable Innovations at the Allen Telescope Array - RFV
Exposing Coordinated Attacks Hiding in the Sheer Noise of False Positives and Lone Incidents: A Data Science Correlation and Contextualization Journey of Logs, Events, and Alerts - PHV
Extend reality with tabletop RPG OWASP Cornucopia. Play sessions throughout workshop times. - XRV
FACTION - DL
Famous and Not-So-Famous Unsolved Codes - CPV
Farming Ndays with GreyNoise - DL
FIDO2 in the Quantum Realm - QTV
Finding 0days in Vilo Home Routers - IOTV
Finding Holes in Conditional Access Policies - CLV
Fine Grained Authorisation with Relationship-Based Access Control - APV
Fireside Chat with DNSA Anne Neuberger - DC
Fireside Chat with Jay Healey and National Cyber Director Harry Coker, Jr. - DC
First Time TSX Hacking Challenge - VMV
Fitness of Physical Red Teamers - PSV
Fix the Flag Wargame - APV
Fix the Flag Wargame - APV
Fix the Flag Wargame - APV
Flipping Locks (The Remix) - Remote Badge Cloning with the Flipper Zero and More - PSV
Flipping Locks (The Remix) - Remote Badge Cloning with the Flipper Zero and More - PSV
Fly Catcher - How I Developed a Low-Cost Raspberry Pi Based Device for ADS-B Spoof - ASV
Flying Blind: Navigating the Turbulent Skies of Aviation Cybersecurity Regulation - PLV
Fool us Once, fool us twice... Hacking Norwegian Banks - CPV
Forgetting the Fundamentals? Data Communications: Physical and Logical Explanation - ICSV
Formidable Adversaries: Responding to Breaches, Ransomware, and State-Sponsored Threat Actors - ADV
From CTI to Creating Campaigns - BTV
From Easy Wins to Epic Challenges: Bounty Hunter Edition - BBV
From Network to Network: Hands-On Pivoting Techniques in Internal Environments - RTV
From Redlining to Weblining: Examining Broadband Deserts and Racial Injustice - BICV
From research to release: Transferring AIxCC results to open source software - AIxCC
From Runners to IdP Admin - RTV
From Theory to Reality: Demonstrating the Simplicity of SPARTA Techniques - ASV
Front line first aid: Triaging your DFIR emergency responders - DCGVR
Fumbling into FedCyber - BICV
FuzzLLM: A Fuzzing Framework for Discovering Jailbreak Vulnerabilities in Large Language Models - BICV
garak : A Framework for Large Language Model Red Teaming - AIV
Garak - DL
GC2 - The First Serverless Command & Control - DL
GCPwn: A Pentester's GCP Tool - CLV
Generative AI vs Crusty NCO - MISC
Generative Red Team 2 Kickoff - AIV
Generative Red Team 2 Readout & Acknowledgements - AIV
GeoINT Mastery: A pixel is worth a thousand words - RCV
GHOST in the Model: Generating AI-Assisted Threat Models for Efficient Offensive Security Testing - RTV
Global Perspectives in Cybersecurity: Challenging Norms and Expanding Horizons - PLV
Gone in 60 Seconds… How Azure AD/Entra ID Tenants are Compromised - CLV
Gotta Cache ‘em all: bending the rules of web cache exploitation - DC
GPON Unplugged - TCV
GPS spoofing: it's about time, not just position - ASV
Grand Theft Actions: Abusing Self-Hosted GitHub Runners at Scale - DC
Gridlock: The Dual-Edged Sword of EV and Solar APIs in Grid Security - APV
Ground Control to Major Threat - Hacking the Space Link Extension Protocol - ASV
GUR RIBYHGVBA BS PELCGBTENCUL - CPV
Haciendo visible lo invisible: Observabilidad y transparencia en routers Draytek - MISC
Hack-A-Sat Digital Twin - ASV
Hack-A-Sat Digital Twin - ASV
Hack-A-Sat Digital Twin - ASV
Hack-A-Sat Quals Challenges - ASV
Hack-A-Sat Quals Challenges - ASV
Hack-A-Sat Quals Challenges - ASV
Hacker vs AI: perspectives from an ex-spy - PLV
Hacking Corporate Banking for Fun and Profit - APV
Hacking Millions of Modems (and Investigating Who Hacked My Modem) - DC
Hacking Policy and Policy Hacking - A Red-Teamer Hacker Guide to the Universe of Cyber Policy - RTV
Hacking Processes: Introducing the Redteaming Process Framework: RTPF - RTV
Hacking Quantum Key Distribution (QKD) - QTV
Hacking the Quansheng UV-K5 - HRV
Hacking the Skies – Satellite Red Teaming - RTV
Hacking the Vote: How Hackers Caused the Downfall of the Dutch Voting Machines - VMV
Ham in a Day Class - HRV
Ham Radio for Hackers - HRV
Ham Radio Fox Hunt - CON
Ham Radio Fox Hunt - CON
Ham Radio Fox Hunt - CON
Ham Radio in an HOA: Radio in the Face of Your Oppressor - HRV
HandPwning: "Your Hand is your Passport. Verify me. Now let me in!" - ICSV
HandPwning: “Your Hand is your Passport. Verify me. Now let me in!” - PSV
HandPwning: “Your Hand is your Passport. Verify me. Now let me in!” - PSV
Hands-on Attack and Breach Simulation exercises - ADV
Hands-on Attack and Breach Simulation exercises - ADV
Hands-on Attack and Breach Simulation exercises - ADV
Hands-On Container Image Security: Mastering Sigstore for Unbreachable Integrity - CLV
Hands-on Kubernetes security with KubeHound (purple teaming) - ADV
HDA Presents : Naomi Brockwell - HDA
HIDe & SEEK - DL
High Intensity Deconstruction: Chronicles of a Cryptographic Heist - DC
High ROI Manual Bug Hunting Techniques - BBV
HookChain: A new perspective for Bypassing EDR Solutions - DC
Hopper - Distributed Fuzzer - DL
Hospitals, Airports, and Telcos — Modern Approach to Attributing Hacktivism Attacks - RCV
Hot SOC Topics for 2024: Feel the Spice! - BTV
How can hackers support efforts to secure AI systems? - PLV
How Competitions Can Fuel Innovation - AIxCC
How do we make LLVM quantum? - QTV
How I discovered and hacked Learning Codes of the key job of a car assembled in my country - CHV
How I Learned to Stop Worrying and Love the Ban - DCGVR
How is GenIA Impacting Cybersecurity: The good, The Bad, and The ugly (Trilingual Panel) - MISC
How to Corrupt Youth to Cyber Focused Space Science - ASV
How to Find a 0day in iOS Apps - BICV
How to Steal Voting Software and Get Away With It - VMV
How we built our REDACTED THING this year, 5n4ck3y, && AMA Panel on Making Badges - MISC
Human Dignity in AI and Tech Policy - PLV
Hunters and Gatherers: A Deep Dive into the World of Bug Bounties - BBV
I am still the Captain now! - ICSV
I've got 99 problems but a prompt injection ain't pineapple - BBV
I've got 99 problems but a prompt injection ain't watermelon - APV
iCLASS - Throwing away the keys - RFV
Iconv, set the charset to RCE: exploiting the glibc to hack the PHP engine - DC
ICS 101 - ICSV
Identity Theft is not a Joke, Azure! - CLV
IDOR in Financial Operations - RTV
If Existing Cyber Vulnerabilities Magically Disappeared Overnight, What Would Be Next? - DC
Importance of ICS knowledge from a engineer's perspective - ICSV
Incident Response 101: Part 1 (IR Overview, Lifecycles, Frameworks, and Playbooks) - BTV
Incident Response 101: Part 2 (Analyst Mindset and Quality Assurance) - BTV
Incubated Machine Learning Exploits: Backdooring ML Pipelines Using Input-Handling Bugs - DC
Indivisible - VMV
Industry Panel: The Modern Evolution of LLMs - AIxCC
Injecting and Detecting Backdoors in Code Completion Models - APV
Insert coin: Hacking arcades for fun - RTV
Inside Dash Cam: Custom Protocols and Discovered 0-days - IOTV
Inside the FBI’s Secret Encrypted Phone Company ‘Anom’ - DC
Intermediate Physical Security - PSV
Interview - CATO Networks, Hosted by Dhruv Shah - RCV
Interview - Daniel Miessler, Hosted by Ankur - RCV
Interview - Mika Devonshire, Hosted by Himanshu Das - RCV
Interview - RedHunt Labs (Kunal), Hosted by Anant Shrivastava - RCV
Interview - Scott Helme, Hosted by Shubham - RCV
Interview - the gumshoo, Hosted by Ram - RCV
Intro to QKD: Quantum Key Exchange: Beyond the Hype - QTV
Intro to Quantum with Q# - QTV
Introduction to Creating Osquery Extensions: Enhancing Endpoint Security Visibility - BTV
Introduction to Drone Security - ASV
Introduction to IPv6 - PHV
Introduction to Kubernetes common attack techniques - RTV
Introduction to MITRE Caldera Through Adversary Emulation - ADV
Introduction to Payment Village CTF - PYV
Introduction to Payment Village CTF - PYV
Introduction to the Payment Village badge - PYV
Invisible Invaders: Strategies to Combat Living Off the Land Techniques in ICS - ICSV
IoT Cat Lamp - IOTV
IoT Cat Lamp - IOTV
Island Hoping: Move from LOLBins to Living off Langs - RTV
Jack Rhysider Masquerade Party - SOC
Jayson Street - Keynote - DCGVR
Jayson Street - Keynote - DCGVR
Jeitinho Cibernético: A Convergência da Segurança no Brasil e América Latina - MISC
Joe and Bruno's Guide to Hacking Time: Regenerating Passwords from RoboForm's Password Generator - DC
Keynote - AI-Powered Cybersecurity: The Importance of Red Teamers - AIV
Kicking in the Door to the Cloud: Exploiting Cloud Provider Vulnerabilities for Initial Access - CLV
Kicking in the Door to the Cloud: Exploiting Cloud Provider Vulnerabilities for Initial Access - DC
Kubernetes Attack Simulation: The Definitive Guide - ADV
Kubernetes Security: Hands-On Attack and Defense - APV
Laundering Money - DC
Learn BadUSB Hacking With the USB Nugget - IOTV
Learn Beginner Soldering With the Meow Mixer Badge - IOTV
Learning the New Amass Collection Engine - RTV
Level UP OSINT - RTV
Leveraging AI for Smarter Bug Bounties - BBV
Leveraging Internal Systems for Enhanced Bug Bounty Success - BBV
Leveraging private APNs for mobile network traffic analysis - DC
LFG! Forming a Bug Bounty Hunting Party - BBV
Life, Liberty and the pursuit of Convenience: the slow death of independence - BICV
Listen to the whispers: web timing attacks that actually work - DC
Living off the Land inside your WiFi : Exploring and Exploiting Access Points and Routers - IOTV
Living off the Land inside your WiFi : Exploring and Exploiting Access Points and Routers - IOTV
Living off the Land inside your WiFi : Exploring and Exploiting Access Points and Routers - IOTV
Locksport Competitions: Compete in the Olympics of Locks - LPV
LoRa for Hackers : Long Range Hacking for Beginners With CircuitPython - IOTV
Lost in Translation - WAF Bypasses By Abusing Data Manipulation Processes - BBV
Low Power & Long Range Communications - QRP - HRV
Mac-n-Cheese: How to Cook Up Delicious Electron Techniques for Red Teamers - RTV
macOS Red Team on Corporate Scenarios - RTV
Maestro - DL
Make all the things - Construa seus próprios "brinquedos" Threats - MISC
Making the DEF CON 32 Badge - DC
Maltego Community Workshop - RCV
Manufacturing- Lessons Learned, Lessons Taught - ICSV
Mapping the Landscape: Top 10 Cybersecurity Trends in Critical Infrastructure for 2024 - ICSV
Maricopa County -Preparing for the 2024 Elections Cycle - VMV
Master Splinter’s initial physical access dojo: Storytelling of a complex adversarial attack - ADV
Maturing Your Application Security Program - APV
MCPA x BIC x CAPT Virtual National Service Panel 2024 - BICV
Measuring the international balance of trade in Internet bandwidth: introducing Netflow to Ministries of Finance - PLV
Measuring the Tor Network - DC
Meet the PortSwigger Research team (Q/A) - BBV
Meshtastic Adventures: Triumphs, Tribulations, and Total Mesh-ups. - RFV
Meshtastic Meetup - IOTV
Meshtastic Meetup - IOTV
Mexicans Together - Un vistazo a recientes investigaciones de nuestros dos equipos globales - MISC
MFT: Malicious Fungible Tokens - ADV
Microhard? More like MicroEASY...to exploit... - IOTV
Mind-Controlling Other Applications: An intro to intra-process hacking - APV
Mining for Abandoned Gold in DNS - RTV
Misinformation, Disinformation, and Malformation in 2024 - VMV
MITRE Caldera for OT - DL
MITRE Caldera - DL
Mobile Mesh RF Network Exploitation: Getting the Tea from goTenna - DC
Modern Red Teaming: macOS, K8s, and Cloud - RTV
Modifying Impacket for Better OpSec - RTV
Modifying Impacket for Better OpSec - ADV
Moriarty - DL
MoWireless MoProblems: Modular Wireless Survey Systems and the Data Analytics That Love Them - PHV
MPT - Pentest in Action - DL
Music Set / Entertainment (Cyberpunk Bar Friday, ACK Stage) - SOC
Music Set / Entertainment (Cyberpunk Bar Saturday, ACK Stage) - SOC
Music Set / Entertainment (Cyberpunk Bar Thursday, ACK Stage) - SOC
Music Set / Entertainment (Pirate's Night For Me! Saturday, SYN Stage) - SOC
Music Set / Entertainment (Retro Sci-Fi Friday, SYN Stage) - SOC
Music Set / Entertainment (Thursday, SYN Stage) - SOC
Mutual authentication is optional - DC
My Conversations with a GenAI-Powered Virtual Kidnapper - AIV
My Smart Red Team Copilot - BICV
Nano-Enigma: Uncovering the Secrets Within eFuse Memories - DC
National Labs Use of XR - XRV
Navigating Bureaucracy: Strategies for a Post-Military Career Encore - MISC
Navigating Microaggressions and Fostering Inclusive Communication with Peers and Leadership for Black Professionals - BICV
Navigating the Cyber Security Labyrinth: Choose Your Own Security Adventure? - APV
Nebula - 3 Years of Kicking *aaS and Taking Usernames - DL
New Skill Unlocked: C2 Infrastructure Automation - RTV
No CTF? No Problem! Leveraging Alternate Reality Games to Develop OSINT and Cryptography Skills - MISC
No Symbols When Reversing? No Problem: Bring Your Own - DC
No Time for Complacency: The Stakes of AI in Cybersecurity - AIxCC
NSM-22 and the National Risk Management Plan: CISA Wants to Hear from You on How to Protect Our Nation’s Critical Infrastructure - PLV
NTLM - The Last Ride - DC
Obsidian: Forensics 101 Part 1 - BTV
Obsidian: Forensics 101 Part 2 - BTV
Offensive Security Testing: Safeguarding the Final Frontier - ASV
OH-MY-DC: Abusing OIDC all the way to your cloud - DC
On Your Ocean's 11 Team, I'm the AI Guy (technically Girl) - DC
On Your Ocean’s 11 Team, I’m the AI Guy (technically Girl) - AIV
One Click, Six Services: Abusing The Dangerous Multi-service Orchestration Pattern - CLV
One for all and all for WHAD: wireless shenanigans made easy ! - DC
One Port to Serve Them All - Google GCP Cloud Shell Abuse - CLV
Online Payments - Attack and Defense - PYV
Open Hardware Design for BusKill Cord - DL
Open sesame - or how vulnerable is your stuff in electronic lockers - DC
Open Source Drone Hacking Simulator - ASV
Open Source Hacker Vs. Government Lawyer: Clashing Views on Fixing Tech in the DoD
- PLV
Opening Remarks - AIV
Optical Espionage: Using Lasers to Hear Keystrokes Through Glass Windows - DC
OSINT at Clemson: Unmasking John Mark Dougan's Disinformation Empire - RCV
OSINT for Hackers - RTV
OT Incident response and Threat Hunting - ICSV
Outlook Unleashing RCE Chaos: CVE-2024-30103 & CVE-2024-38021 - DC
OWASP Amass Expanding Data Horizons: Amassing More Than Subdomains - RCV
Panel of Bug Bounty Community Leaders - BBV
Photoshop Fantasies - AIV
Physical Fundamentals of Quantum Computing - QTV
Physical OSINT - PSV
Physical Red Teaming for Offensive Cyber Teams - RTV
Physical Security - Bypassing Access Control Systems - RTV
Physical Security Assessment Basics for Internal Employees - PSV
Pick Your Poison: Navigating a secure clean energy transition - PLV
Pipeline Pandemonium: How to Hijack the Cloud and Make it Rain - RTV
Play by Play of the Curling v. Raffensperger Lawsuit - VMV
Playing with Quantum: wayfinding with quantum game theory - QTV
Porn & Privacy - CPV
Power To The Purple - ADV
Practical Exploitation of DoS in Bug Bounty - BBV
Prendendo Fraudadores utilizando Técnicas de Red Team - MISC
Preparing for the Future: A Discussion of our Rapidly Evolving Threat Landscape - IOTV
Product security considerations for OT security appliances - ICSV
Programming a CTS-V Gauge Cluster into an ATS-V, out of pure spite - CHV
Protecting the Backbone of Our Modern World - MISC
Prototype Pollution in Depth, From Beginner to 0-Day Hunter - BBV
Psychic Paper: Making eink access badges accessible for anyone - IOTV
PTP Flight Challenge - ASV
PTP Flight Challenge - ASV
PTP Flight Challenge - ASV
Pushing the limits of mass DNS scanning - RCV
Pwning through the Metaverse - Quest Headset Vulnerability Research - XRV
QML - Quantum Machine Learning: What is it, where did it come from, and how do I start? - QTV
Quantum on the flip side - A global south perspective on Quantum Technologies - QTV
QuickShell: Sharing is caring about an RCE attack chain on Quick Share - DC
Ransomware B-Sides: Los ransoms que nunca triunfaron - MISC
Recon MindMap: Organize, Visualize, and Prioritize Your Recon Data Efficiently - RCV
Recursion is a Harsh Mistress: How (Not) To Build a Recursive Internet Scanner - RCV
Red Goes Purple: Executing the Attack Path - RTV
Red Team Infrastructure Setup and Automation - RTV
Red Team Terraform Workshop - RTV
Red Teaming is broken; this panel will fix it. - ADV
Redefining V2G - How to use your vehicle as a game controller - DC
Reflections on a Decade in Bug Bounties: Experiences and Major Takeaways - BBV
Relative Path File Injection: The Next Evolution in RPO - APV
Remote Sensor Node Updates for FISSURE - The RF Framework - RFV
Removing OPSEC from Cyber Predators and Threat Actors - MISC
Removing the Ring of Gyges: Lessons from Securing AI Systems Against File Format Abuse - AIV
Revealing Choke Points: Practical Tactics for Boosting Cloud Security - CLV
Reverse engineering and hacking Ecovacs robots - ESV
Reverse Engineering MicroPython Frozen Modules: Data Structures, Reconstruction, and Reading Bytecode - DC
RF Attacks on Aviation's Last Line of Defense Against Mid-Air Collisions (TCAS II) - ASV
RF CTF Kick Off Day 1 - RFV
RF CTF Kick Off Day 2 - RFV
RFID 101 - PSV
Risk Limiting Audit DEMO by Philip Stark - VMV
Risk Limiting Audits From the Source - VMV
Rules All Hackers Must Follow in War - PLV
Runtime Reachability: Prioritizing Vulnerabilities with eBPF & Continuous Profiling - CLV
RustOps - RTV
Safecracking for Everyone - LPV
Safecracking Practical Demonstration - LPV
SBOMs the Hard Way: Hacking Bob the Minion - IOTV
SCAGoat - Exploiting Damn Vulnerable SCA Application - DL
SDLC Nightmares - Defeating Secure Code Review GPT Hallucinations - APV
Secrets and Shadows: Leveraging Big Data for Vulnerability Discovery at Scale - DC
Secure the Skies: A Modern Android Security Research Framework for Drone Ground Control Stations and Applications - ASV
Securing CCTV Cameras Against Blind Spots - DC
Securing Frontends at Scale: Paving our Way to the Post-XSS World - APV
Securing Health Care: AIxCC, DIGIHEALS, and UPGRADE - AIxCC
Securing the Cloud with Cloud Threat Intelligence and Open Source Security - BTV
Securing the Future with CoSAI: Identified Technical Workstreams and Call for Contributions - RTV
Securing the Harvest: Cyber Defense for Agricultural Control Systems - ICSV
Seeing the Unseen: An Evaluation of Active Scanning in ICS Environments - ICSV
Selfie with a CubeSat - ASV
Selfie with a CubeSat - ASV
Selfie with a CubeSat - ASV
Serberus - DL
Shifting left in Reversing apk by converting smali to java - DCGVR
SHIM me what you got - Manipulating Shim and Office for Code Injection - DC
Signature-Based Detection Using Network Timing - PHV
SIMply Secure - TCV
Simulated Drone Hacking - RTV
Singapore - Safeguarding the Nation: The Vital Role of Cybersecurity in AI-Driven Homeland Security - PLV
SIV Internet Voting Hacking Challenge - VMV
Skynet - DL
Small Satellite Modeling and Defender Software - ASV
Smart Shopping Cart Wheels - How they Work - PSV
Smishing Smackdown: Unraveling the Threads of USPS Smishing and Fighting Back - DC
SMOKE: Signature Management using Operational Knowledge and Environments - AIxCC
Sneaky Extensions: The MV3 Escape Artists - ADV
So you wanna know how to make badges - MISC
Social Engineering Improv Acting Techniques - PSV
Social Engineering Like you’re Picard - DC
Software Defined Radio 101: Capturing Your First RFCTF Flag - RFV
Sold Out - 64-bit Intel Assembly Language Programming for Hackers - WS
Sold Out - Capture the Flag 101 - WS
Sold Out - Crash Course in Physical Access Control Systems - WS
Sold Out - Dissecting and Defeating Ransomware's Evasion Tactics - WS
Sold Out - Dissecting Malware for Defense - Crafting Custom Yara Rules - WS
Sold Out - Dodging the EDR Bullet: A Workshop on Malware Stealth Tactics - WS
Sold Out - Email Detection Engineering and Threat Hunting - WS
Sold Out - Finding the Needle: An Introduction to Detection Engineering - WS
Sold Out - Flipping the Coin: Red and Blue Teaming in Windows Environments (++) - WS
Sold Out - From an attacker's lair to your home: A practical journey through the world of Malware - WS
Sold Out - Ghidra Analysis & Automation Masterclass - WS
Sold Out - Hack the connected plant! - WS
Sold Out - Hacking Apps on Salesforce - WS
Sold Out - Hacking The Metal: A Spark of Intelligence - WS
Sold Out - Hide your kids, turn off your Wi-Fi, they Rogue APing up in here; 201 - WS
Sold Out - Industrial Control Systems: how to secure them in practice! - WS
Sold Out - Learning to Hack Bluetooth Low Energy with BLE CTF - WS
Sold Out - Long Live Empire: A C2 Workshop for Modern Red Teaming - WS
Sold Out - Machine Learning for N00bs - WS
Sold Out - Master Class: Hands-On Machine Learning to Enhance Malware Analysis, Classification, and Detection - WS
Sold Out - Med Team vs Red Team: Intro into Medical Device Hacking - WS
Sold Out - Offensive SCCM: Abusing Microsoft's C2 Framework - WS
Sold Out - Playing with RFID - WS
Sold Out - Sharp Security from All Angles: Mastering Security in .NET Core 8 and Angular 17 Applications - WS
Sold Out - Small Choices, Global Repercussions: A Tabletop Exercise about Decision-Making in Healthcare Cybersecurity - WS
Sold Out - Supercharge SAST: Semgrep Strategies for Secure Software - WS
Sold Out - Tracing The Pain Away - Practical Binary Tracing Techniques For Defeating Modern Malware Protections - WS
Sold Out - Traumatic Library Loading : If you want to use it, you have to implement it... - WS
Sold Out - Whitebox Web Exploit Development - WS
Solder your own cat shaped WiFi Haking tool - IOTV
Solving the "Lover, Stalker, Killer" Murder with strings, grep, and Perl - DC
Something something Meshtastic Pip-Boy Personal Mesh with 150 km reach - DCGVR
Space Grand Challenge Luna - ASV
Space Grand Challenge Luna - ASV
Space Grand Challenge Luna - ASV
Space Pirate Simulator - ASV
Space Systems Security CTF – Platform Security - ASV
Space Systems Security CTF – Platform Security - ASV
Space Systems Security CTF – Platform Security - ASV
spacestudio and spacetower challenges - ASV
spacestudio and spacetower challenges - ASV
spacestudio and spacetower challenges - ASV
Speed Bumps and Speed Hacks: Adventures in Car Manufacturers Security - APV
Spies and Bytes: Victory in the Digital Age - DC
Splitting the email atom: exploiting parsers to bypass access controls - DC
Spotting Deepfakes in a World with Generative AI - AIxCC
SQL Injection Isn't Dead: Smuggling Queries at the Protocol Level - DC
SQLi to Root Access: Exploiting a ISP infrastructure - MISC
Sshamble: Unexpected Exposures in the Secure Shell - DC
SSTV: How To Send Cat Memes Via Ham Radio - HRV
Stanford Digital Observatory - VMV
Staying alive off the grid - using APRS and Lambdas to monitor temperature remotely - HRV
Stealer Logs: Automation, Analysis, & Espionage in the World's Most Interesting Dataset - BTV
Store bought is fine, sometimes! - BTV
Stranger in a Changed Land - DC
Structural Insights: PDF Analysis for Detecting and Defending Against Threats - MISC
Student Engagement Doesn't Have to Suck - XRV
Sudos and Sudon’ts - Peering inside Sudo for Windows - DC
Supercharge your vuln finding workflow with automated labs: How Ludus made it rain creds from SCCM - RTV
Surprise Talk - CPV
SWGRecon: Automate SWG Rules, Policy, and Bypass Enumeration - RCV
Taking off the blindfold: Detecting persistent threats on Draytek edge devices - DC
Taming the Beast: Inside the Llama 3 Red Team Process - DC
Tapping the OSINT potential of Telegram - RCV
Techniques for Creating Process Injection Attacks with Advanced Return-Oriented Programming - DC
Telecom Time Machine - TCV
Tempest c2: Use and Design - RTV
Tempest - DL
Tengu Marauder - DL
Terraform Unleashed: Crafting Custom Provider Exploits for Ultimate Control - CLV
Testbed Virtual Factory - DL
The Art of Critical Thinking through an Adversarial Mindset? (RTV Keynote) - RTV
The art of Pivoting in OSINT Investigations - RCV
The Bug Hunters Methodology Live - DEF CON Edition - BBV
The Cat-and-Mouse Game of Adversarial Artificial Intelligence - AIxCC
The Curious Case of Alice and Bob: What You Can (And Cannot!) Do as Digital Investigators - PHV
The Curious Case of Stealer Logs: Access & Espionage in the World's Most Interesting Dataset - RTV
The Dark Side of Bug Bounty - APV
The hack, the crash and two smoking barrels. (And all the times I (almost) killed an engineer.) - DC
The Hybrid Horizon: Unleashing the Power of Azure Hybrid Integrations - RTV
The Immortal Retrofuturism of Mainframe Computers and How to Keep Them Safe - APV
The Implications of Cyberbiosecurity in Advanced Agricultural Systems - BICV
The Interplay between Safety and Security in Aviation Systems - ASV
The Metasploit Framework v6.4 - DL
The Missing Link - How we collect and leverage SBOMs - APV
The not-so-silent type: Breaking network crypto in almost every popular Chinese keyboard app - DC
The Open Source Fortress: Finding Vulnerabilities in Your Codebase Using Open Source Tools - APV
The Oracle Awakens: Demystifying Privilege Escalation in the cloud - CLV
The Past, Present, and Future of Bioweapons - BHV
The People's Republic of Fieldbus: What to know about EPA - ICSV
The perma-lag: why industrial cybersecurity will never be state-of-the-art - ICSV
The Quantum Ethics and Skills Debates - QTV
The Rise and Fall of Binary Exploitation - DC
The Rise of the Planet of the Agents: LLM-based AI Agents and Cloud Security APIs - CLV
The Risk and Reward of Distributed Industrial Control - ICSV
The Sand Castle - The State of the MacOS Sandbox - DCGVR
The Secret Life of a Rogue Device - Lost IT Assets on the Public Marketplace - DC
The SIEMless Hack: Rewriting Reality with Log Injection - RTV
The Threat of Deepfakes and Synthetic Media to Election Integrity - VMV
The Transparency Algorithm: AI's Answer to Legal Racial and Social Inequality - BICV
The Value of Trust in the Open-source Software Ecosystem - PLV
The Village Peoples' Panel - What Really Goes On in a Village? - RTV
The Way To Android Root: Exploiting Your GPU On Smartphone - DC
The wild and wonderful world of early Microprocessors (with a focus on the 6502) - DC
The World Wide Paraweb - DL
The XZ Backdoor Story: The Undercover Operation That Set the Internet on Fire - DC
TheAllCommander 2.0 - DL
Thinking Outside the Kube - Finding and Exploiting Command Injections in Kubernetes - RTV
Threat Emulation 101 - RTV
Threat Hunting + Intelligence, capabilities, skills and capabilities inside the LATAM community - MISC
Threat hunting like a pentester - RTV
Threat Modeling in the Age of AI - APV
Threats in Space: The Dangerous Rise of GNSS Attacks - MISC
Thrunting or DEATH! (A BTV Panel) - BTV
Ticking SQLi - APV
Top War Stories from a TryHard Bug Bounty Hunter - BBV
Tough Adversary? Don’t Blame Sun Tzu - ADV
Tracking Industrial Advanced Threat Actors Who Aren't Really Advanced Just Skiddies Who Deface PLCs and Have Bad Manners: Methods and Results - ICSV
Tracking Real-Time Locations with Rogue WiFi Packets - RFV
Transforming AppSec: Protecting 'Everything as Code' & Emerging Tech - APV
Trapped Ion Quantum Computing Systems - Behind The Scenes: from the physics to control electronics - QTV
Travel Better: Expedient Digital Defense - CPV
Trip Through Reality XR for Performances Masterclass with the Glad Scientist - XRV
Troll Trapping Through TAS Tools - Exposing Speedrunning Cheaters - DC
Tunnel Vision: Exploring VPN Post-Exploitation Techniques - RTV
UDSonCAN Attacks: Discovering Safety-Critical Risks by Fuzzing - CHV
Under the Hood: Incident Response at High Speed (A BTV Panel) - BTV
Understanding Cognitive Warefare in a Geopolitcal Context - VMV
Understanding the Role of Secretary of States in Elections - VMV
Underway to Identifying Commonalities of Cybersecurity Incidents in the Maritime Transportation System - ICSV
Unexpected Leaks in AWS Transit Gateways - CLV
Unlocking Hidden Superpowers: Neurodiversity in Infosec - DCGVR
Unlocking the Gates - Understanding Authentication Bypass Vulnerabilities - APV
Unlocking the Gates: Hacking a secure Industrial Remote Access Solution - DC
Unmasking Shadows: Strategies on Hunting Ransomware Groups - BICV
UnOAuthorized: Discovering the path to privilege elevation to Global Administrator - CLV
Unsaflok: Hacking millions of hotel locks - DC
Unveiling Vulnerabilities: A Comprehensive Guide to Bug Bounty Recon - BBV
US and International Public Cyber Policy 101 - PLV
Use opensource AI to map alerts & logs into techniques, clusters, and killchains - BTV
User Behaviour Analytics in Payments - PYV
Using AI Computer Vision in Your OSINT Data Analysis - PHV
Using ChatGPT to Write Defensive & Offensive Tools for ICS/OT - ICSV
Using EPSS for Better Vulnerability Management - APV
Using Retrieval Augmented Generation (RAG), Langchain, and LLMs for Cybersecurity Operations - RTV
V2GEvil: Ghost in the wires - CHV
Veilid Dev and Community Meetup - DC
Village closing - ADV
Virtual SIEM/SOAR Workshop - BICV
Visualizing AIxCC: Bringing Your Code to Life - AIxCC
Volatile Vault - Data Exfiltration in 2024 - DL
Voting Village Opening Remarks - VMV
Vovk - Advanced YARA Rule Generator v2.0 - DL
War Games: Red Team for OT (Based on Real World Case Studies) - ICSV
Warflying in a Cessna - ASV
Warwheeling: The Wireless Sk8r - RFV
Watch The Skies: Build Your Own ADS-B receiver - ASV
Watchers being watched: Exploiting the Surveillance System and its supply chain - DC
Weaponized Convenience: Inside the Rise of Remote Tool Abuse - BICV
Web2 Meets Web3: Hacking Decentralized Applications - APV
Welcome to DEF CON - DC
What Do Long Voter Registration Lines Mean? - VMV
What Does it Mean to be an American? - VMV
What is the Voting Village? - VMV
What To Expect When You’re Exploiting: Attacking and Discovering Zero-Days in Baby Monitors and Wi-Fi Cameras - IOTV
What!? Is my life that fragile? - DCGVR
What’s next for the commercial CNE marketplace? A chance for you to influence the policy that will impact the future - PLV
When Chatbots Go Rogue – Lessons Learned from Building and Defending LLM Applications - APV
Where's Waldo? Can you find the Raspberry Pi in the Cyber Defense Exercise? - ICSV
Where’s the Money: Defeating ATM Disk Encryption - IOTV
Where’s the Money: Defeating ATM Disk Encryption - DC
Who cashed my check?! Catching (Very Obvious) Fraudsters - DCGVR
Who's Afraid of Synthetic Aperture Radar? - RFV
Why are you still, using my server for your internet access. - DC
Why You Should Be Hunting on Web3 Bug Bounties - BBV
Wi-Fi Hacker Hunting - IOTV
Wi-Fi Hacking Self Defense: Four Advanced Techniques and How to Stop Them - IOTV
Windows Downdate: Downgrade Attacks Using Windows Updates - DC
Winning big: AppSec Considerations From the Casino Industry - APV
Winning the Game of Active Directory - PHV
Wireless & Networking workshop - ESV
Wireless & Networking workshop - ESV
Wireless & Networking workshop - ESV
World Wide War Drive Outbrief - RFV
Worried about AI taking your job? Then this talk is for you. - BICV
Wu-Tang is for the Children: How States Laws Intended to Protect Children Raise Other Privacy and Legal Risks - CPV
XenoboxX - Hardware Sandbox Toolkit - DL
Xiaomi The Money - Our Toronto Pwn2Own Exploit and Behind The Scenes Story - DC
XR for All: Accessibility and Privacy for Disabled Users - XRV
Yet another way of exfiltrating data from air-gapped systems OR Oh no, everything is a radio - RFV
You got a lighter? I need to do some Electroporation. - BHV
Your AI Assistant has a Big Mouth: A New Side-Channel Attack - DC
Your CI/CD Pipeline Is Vulnerable, But It's Not Your Fault - APV
Your Smartcard is Dumb: A Brief History of Hacking Access Control Systems - PSV
Zip It Up, Sneak It In - Introduction of apkInspector - DL
DEF CON News
NEWS
DEF CON Response to Badge Controversy
Posted 8.10.24

DEF CON thrives on community collaboration and has operated for over 30 years successfully working with hundreds of vendors including the dozens that have helped with our badges over the years. For this year’s Raspberry Pi badges, DEF CON hired Entropic Engineering to do the hardware development and firmware. After going overbudget by more than 60%, several bad-faith charges, and with a product still in preproduction, DEF CON issued a stop work order. Any claims that DEF CON did not pay Entropic Engineering for its hardware or firmware development are false. Unfortunately, we heard that these issues with Entropic Engineering were not unique to DEF CON. We decided at that point to finish the badge on our own. We paid to send engineers to Vietnam to work onsite to finalize and test the badges in order to ensure they would be done on time for the conference. We never removed Entropic Engineering’s logo from our badge, it is still on the PCB. However, Entropic was not involved in the design and production of the case, and we removed their logo we had added as a courtesy.
We were happy to still include one of their contractors on the badge panel session. Unfortunately, shortly before the talk was set to take place DEF CON became aware that unauthorized code had been included in the firmware we had paid Entropic Engineering to produce, claiming credit for the whole badge and promoting their coin wallet to solicit money from DEF CON attendees above and beyond what we had negotiated. When asked about the unauthorized code, the engineer said it had been done as a “joke” two months ago and forgot to remove it, and we decided as an organization not to have him on stage while we kept the slides in the talk giving him credit for his work. We communicated the change in advance of the talk, and this individual decided to show up for the panel anyway. He refused to leave, demanding that our security team remove him. Wanting to ensure that the other people involved in creating the badge were able to deliver their presentation, we complied with his wishes and escorted him off the stage, where he was free to continue attending the conference.
Any issues of non-payment are between him and Entropic Engineering, DEF CON fulfilled its financial obligations.
DEF CON Badge Update!
Posted 8.9.24

Thanks to everyone who has reached out to us about the DEF CON 32 badge. We are aware of the save issue and a fix is incoming. Later today we'll have a patch and some instructions for you at
defcon.org/badge/32
. We'll keep you posted in these spaces.
DEF CON Hotline!
Posted 8.4.24

You can reach DEF CON staff during normal hours of operation to anonymously report any behavior violating our code of conduct or to find an empathic ear! You can contact us via:
Voice Call, SMS/Text, or Signal:
+1 (725) 222-0934
or Discord:
@defconhotline
We hope you have a safe and fun #DefCon32!
Online Registration Closes Soon!
Posted 7.18.24

Just a friendly DEF CON reminder for all our last minute folks -
online registration for DEF CON 32
ends August 1. Cash at the door still works, though. Linecon abides.
Pirate Party at DEF CON 32!
Posted 7.2.24

New DEF CON 32 parrrty just dropped! Join us Saturday August 10 for ‘Yo Ho Ho, a Pirate’s NIght for Me! There’ll be a best-dressed pirate contest with a 460 dollar prize and entertainment from O’Craven (Insta: OCRAVEN),NorCal’s most swashbuckling Celtic Pirate Rock Band.
For details and updates keep an eye on
the DEF CON Music Page
. We’ll see you there!
Workshops Live! Registration opens soon!
Posted 7.1.24

The wait is over-
DEF CON 32’s Workshop roster
is LIVE! We’re quite proud of the lineup! Registration opens at precisely noon Pacific on July 7.
Workshops historically fill up quite quickly so we recommend having a few choices and doing some stretches for maximum click-finger agility.
Good luck to everyone. Just over a month till DC32! Let’s GO.
DEF CON Music Presents: Retro Sci-fi Friday Night!
Posted 6.14.24

The good folks at @defcon_music have blessed us with some big party info for #defcon32.
"This year’s theme for our
Friday Night party is “Retro Sci-Fi“
Be sure to bring your ray guns, Thought immobilizers, Robot sidekicks and of course your best spacesuit!
Sci-Fi costume contest at Midnight!
Winner gets $460 cash!
(Costumes encouraged but not required.)
For more keep an eye on
defconmusic.org
.
Parties! Meetups! Events! Contests!
Posted 6.12.24

We are enterning the home stretch, citizens of DEF CON! Just under two months until the curtains open - have you prepared yourselves?
The full roster of
parties, meetups and events
is live on defcon.org to assist in all your various pre-function planning.
Prior Planning Prevents Poor Partying, so get yourself familiarized. While you’re there, please make sure to check out the
fantastic contest lineup
DC32 has ready for you!
It’s within sight - just over the horizon. Feel free to get psyched.
See you soon!
Save yourself! Book at The RIO!
Posted 5.22.24

DEF CON 32 #protip: On the desert planet of Las Vegas, door to door AC is worth its weight in water.
When choosing a hotel, don’t overlook our deeply discounted room block in the Rio. All our reserved Rio rooms are fully remodeled suites, and there’s a FREE shuttle right to DEF CON’s main entrance. No wasting your precious moisture on the burning sidewalks.
Also, we have it on good authority the the shuttle moves without rhythm so as not to attract the worm.
Check out the Rio room link now!
Congrats to CTF Qualifying teams!
Posted 5.7.24
Thanks to the fine folks at Nautilus Institute the DEF CON 32 CTF quals are in the books - you can read all about it at
https://quals.2024.nautilus.institute/
. There's also a veritable feast of JSON dumps for the curious. Congrats to the winners, thank you to everyone who suited up and we'll see you in Las Vegas!
CTF Quals are Coming!
Posted 4.29.24

Attention packet wizards - the DEF CON 32 CTF Quals Begin May 3!
Our friends at the Nautilus Institute have created a fiendish test of skills that lasts a whole weekend, and the winner gets to compete for everlasting glory in the main event at DEF CON 32.
Will your team rise to the challenge?
You can get your hat in the ring by registering at
https://quals.2024.nautilus.institute/
Godspeed to every mad genius who answers the call.
Another new room block - The RIO!
Posted 4.22.24

We’ve secured a
block of deeply discounted rooms at the fabulous Rio
, with FREE shuttle service to and from the West Hall of the Las Vegas Convention Center! In addition to the door-to-door shuttle service, they’re giving us a big break on the room rate AND the Resort Fee. Rio also offers
additional discounts for government employees
We love the Rio - it was home base for DEF CONs 19-22 - and you should see it now. It’s had a massive multi-year renovation and it’s new all over. New all-suites accomodations, new restaurants, new food hall, even a redesigned 5-acre pool complex. It’s a whole new experience at a steal of a price.
We expect these to fill quickly, so you should act accordingly and book now!
New Room Block! Resorts World!
Posted 4.6.24

Spring has sprung. That means laughter in the air, flowers everywhere, and DEF CON right around the corner. In the spirit of new growth we’ve got another discounted room block for DEF CON 32 attendees - this time it’s at Resorts World. You can check the selection and
book at this link
.
Resorts World is the very large, very new hotel-casino complex that sits on the lot once occupied by The Stardust. It sports a location convenient to the LVCC, the very latest in accommodations and (so far as we can tell) no relation to Michael Crichton’s WestWorld and FutureWorld.
It’s all happening, people. Just a few more months till the big event. Prepare accordingly.
Fontainebleau Room Block added!
Posted 3.20.24

We’ve secured a discounted
block of rooms at the Fontainebleau Hotel
, just across the street from our new location in the LVCC West Hall. To get the discount, follow this link and be sure to reserve by July 4. You can also reserve by phone at (833) 702-7272 - tell ‘em the DEF CON Communications Group sent ya.
The DEF CON season approaches. Feel free to get amped.
DEF CON 32 Call for Papers and More!
Posted 2.22.24
DEF CON 32 preparations are well and truly underway. You can tell because the air is thick with call announcements.
The Calls opening today are:
CFP
Workshops
Demo Labs
Policy
As always, don’t procrastinate. The chances of your idea getting over the finish line are better when the reviewer has time to communicate with you.
The information about all the
open calls is here
. We can’t wait to see what you’re working on.
DEF CON 32 Online Registration is Open!
Posted 2.19.24

DEF CON is primarily a cash-at-the-door kind of conference. LineCon is in our DNA, and we will always honor it. Long may the beach balls fly.
Still, the option to register online has been a benefit to many attendees. We’re keeping that method open for all those who need it.
If that’s you, good news! From right now until July 5, 2024, you can register for DC32 at
shop.defcon.org
.
DEF CON 32 Theme!
Posted 2.5.24

Now that we’ve got the venue stuff sorted out, we’re ready to announce the DEF CON 32 theme!
This year’s theme is “Engage”. The internet may be trending toward a dystopia of dark patterns and walled gardens, but we can do better. We know how. The antidote to apathy and doomscrolling is engagement. You can read The Dark Tangent’s full post about it here:
https://forum.defcon.org/node/248361
.
The visual vibes are Y2K inspired and you can get your color palette, fonts and whatnot in the
DEF CON 32 style guide
.
As always, we are excited to see where you’ll take this. Let’s GO.
We Have Some News About DEF CON 32
Posted 2.4.24

DEF CON was canceled.
After a great 25 year relationship Caesars abruptly terminated their contract with DEF CON, leaving us with no venue for DC 32, and just about seven months to Con!
We don’t know why Caesars canceled us, they won’t say beyond it being a strategy change and it is not related to anything that DEF CON or our community has done. This kind of no-notice cancellation of a contract is unheard of in the conference business. The parting is confusing, but amicable.
So now we have a challenge. Without a venue, will we be able to UN-Cancel DEF CON 32 before time runs out?
Hackers are flexible. We find solutions. We need a space that can handle an event our size, and configurable enough to accommodate our content. We need a location close to our announced dates, and with super short notice... No small feat.
We immediately scrambled a venue strike team to Las Vegas. Floors were walked. Meetings were held. Hands were shook and options weighed. When the smoke cleared, the field narrowed to one obvious choice and we began forging the requisite agreements.
W00T! DEF CON Is UN-CANCELED!
DEF CON 32 will still be August 8-11 2024, but now held at the Las Vegas Convention Center (LVCC) with workshops and training at the Sahara.
DEF CON 32 will be an adventure where we can try things not possible in our old Casino Hotel spaces. What specifically you ask? Well we are still learning all the specifics but we will have more space, a proper food court, and the largest indoor venue LCD wall in the country.
There are still many questions to be answered, and we have started a live FAQ section on the Forums for DEF CON 32 where we will be updating questions and answers. The initial FAQ is located here:
https://forum.defcon.org/node/248358
I look forward to seeing everyone this summer, the start of a new DEF CON era!
-The Dark Tangent
P.S. We made shirts and stickers:
https://shop.defcon.org/products/def-con-un-canceled-mens-t-shirt
https://shop.defcon.org/products/def-con-un-canceled-sticker-set
Big Batch of Calls Open Now for DEF CON 32!
Posted 1.3.24

2024 is officially underway, and we're kicking off DEF CON season with a bunch of of open calls for DC32! Villages, Constests, Parties, Communities - the majority of the calls are open now, with the balance opening February 1. The full list of open calls is available at the
Calls Index Page
.
Remember, the sooner you get your proposals in, the more chance we can help make your ideas into reality. We can’t wait to see what you’ve got up your sleeves. Happy New Year!
DEF CON Training Las Vegas 2024 is Open for Registration!
Posted 12.15.23

Registration for the DEF CON Training 2024 in Las Vegas is open! Join us August 12-13 right after DEF CON 32 for some two-day, deep-dive technical sessions from some world class trainers. All the details are at
training.defcon.org
- reserve your spot!
DARPA AIxCC talk from DEF CON 31!
Posted 9.8.23

At DEF CON 31,
DARPA announced a huge 2-year AI Cyberchallenge
with the semis and finals hosted at good old #defcon. Over 18M in total prizes, access to cutting edge tech and a chance to help secure the open infrastructure we all rely on. If that sounds like your kind of fun, details are at
http://aicyberchallenge.com
Throwback Thursday - DEF CON 31 photos!
Posted 8.31.23

More DEF CON 31 goodies going up on the media server: the photos from DC31 are live at
media.defcon.org
.
Thanks to the DEF CON Photo Corps for all the hard work!
DEF CON 31 Breaking: AI Cyber Challenge Announced for DEF CON 32 & 33
Posted 8.9.23

DEF CON will host the Artificial Intelligence Cyber Challenge #AIxCC semis in 2024 and the final in 2025! @DARPA, @openssf ,@Google, @AnthropicAI @Microsoft & @OpenAI are working together to challenge contestants to create novel AI cybersecurity systems.
Over $18m in cumulative prizes, access to cutting edge tech and a chance to help secure the open infrastructure we all rely on.
Attend the
official announcement
at DEF CON 31, Friday at 14:30 in Track 2!
Full details at
aicyberchallenge.com
Return to Index
© 1992-2023 DEF CON Communications, Inc. All Rights Reserved | DEF CON Policies | DMCA Information
DEF CON 32 FAQ
DEF CON 32 FAQ
This guide will be updated as we learn answers to our questions. If you don’t see an answer to your question please ask and we will do our best to answer.
THE BASICS
When is DEF CON 32?
August 8-11th, 2024
How much will DEF CON 32 badges cost when purchased with cash in-person?
We are still learning about the new venue and hope to announce the price in the coming weeks.
I need to buy a badge online so work will reimburse it.
When badge sales begin they will be available at
https://shop.defcon.org/
I need a receipt for the badge, I'm buying with cash.
You will be able to find a DIY receipt on the website, and the
media server under DEF CON 32, on August 8th, 2024.
Where is DEF CON 32?
Las Vegas Convention Center (LVCC) West Hall with workshops and training at the Sahara Hotel.
https://en.wikipedia.org/wiki/Las_Ve...vention_Center
https://www.vegasmeansbusiness.com/meeting-facilities/
LVCC West Hall
3150 Paradise Road
Las Vegas, Nevada 89109
Sahara Hotel
https://www.saharalasvegas.com/
2535 Las Vegas Blvd. South
Las Vegas, Nevada 89109
How much space will we have?
A lot. We will have all villages, contests, talks and events under one roof. To give you an idea the LVCC space will be about 800k square feet, and the old Caesars Convention Center was about 550k. Unfortunately a direct sqft comparison is not really the best way to measure space in a convention our size, especially given how complex and unique we are, but you will notice the positive difference.
How will the conference be laid out?
We will know more on floor-plan after we hold a couple on-site planning meetings in February and March. We will update our public maps on the venue page in the coming months, after coordinating with our content creators.
I run a contest / event / village, what does this mean for me?
We have started a separate FAQ for the DEF CON Creators in their planning space.
What are the hours of DEF CON?
Doors open each morning at 08:00 and we go to 02:30 in the morning. On Sunday we shut down after the Closing Ceremonies, around 18:00 (Pacific Time Zone)
DEF CON cash registration and official Merch store will open by 08:00 Thursday the 8th.
What hotels should we stay in?
We have a web page with the hotels we currently have a room block with, and we are working to add more hotels in the coming weeks. Please help us by booking at one of these hotels.
https://defcon.org/html/defcon-32/dc-32-venue.html
What happens if I made a reservation in the Caesars block?
Nothing, you are free to keep it, but you may have further to travel to get to the LVCC.
What is the last day we can cancel our reservations with Caesars Entertainment hotels without an extra fee/fine?
To avoid forfeiture of deposit, please ensure all changes and cancellations are made at least 72 hours prior to scheduled arrival date.
Will new hotels charge a "resort fee" on top of quoted price and taxes? What is being offered to people that sign up under the new DEF CON block at the now hotels?
Each hotel will have separate pricing structures, resort fees, and wifi device limits. As we learn details of our room blocks we will post on the Hotels Page.
https://defcon.org/html/defcon-32/dc-32-venue.html
What about DCTV?
We are currently working the hotel venues to see what is possible, as each hotel has different infrastructure and we are just learning how to work with them. Once we know we will announce and update the hotels page.
Where can I find a map that shows how we can enter and exit the Las Vegas Convention Center during DEF CON?
We are working to add several maps & directions to the DEF CON website under our Hotel & Venue page.
https://defcon.org/html/defcon-32/dc-32-venue.html
How do I get to the LVCC?
If you are taking a Taxi go to the West Convention Center entrance: 3150 Paradise Road, Las Vegas, Nevada
You can find the current taxi fair at:
https://www.lasvegashowto.com/taxi-fare
Currently the taxi cost from the airport to LVCC is speculated at $29.
If you are walking to the LVCC you will enter via the West Convention Center entrance. You can enter by the north lobby or the main atrium entry doors.
Are there any pedestrian bridges over streets to get to the convention center? Where?
Yes, and No. There is a sky bridge crossing paradise road from the north hall to the west hall, but it is really only useful to walk from one end of the LVCC to another.
Las Vegas Convention Center Loop.
The Las Vegas Convention Center Loop is an underground transportation system designed to quickly transport passengers throughout the 200-acre Las Vegas Convention Center campus. The system consists of two one-way, .8-mile-long tunnels built to accommodate all-electric Tesla vehicles driving at speeds of up to 35 mph. The LVCC Loop reduces a 25-minute walk to a less than two-minute ride.
Attendees can access the LVCC Loop via three stations:
• West Station – Adjacent to West Hall, this station is located above ground
• Central Station – Near the Central Hall Main Entrance, this station is located below ground and is accessible via escalator or elevator
• South Station – Adjacent to South Hall, this station is located above ground
Las Vegas Monorail
Hours of operation are Mondays, 7 a.m. to midnight; Tuesday through Thursday, 7 a.m. to 2 a.m.; Friday through Sunday, 7 a.m. to 3 a.m.
The Las Vegas Monorail provides a quick and convenient connection along the Las Vegas Strip, linking riders to world-class restaurants, shows, shops, day/nightclubs, spas, hotels and casinos. Directly connected to the Las Vegas Convention Center as well as several resort hotels, the Monorail Is the most convenient way to get around the Strip in Just minutes - without the hassles of traffic or wasted time.
Trains arrive every 4-8 minutes at each of the seven stations: MGM Grand, Bally’s/Paris Las Vegas, Flamingo/Caesars Palace, Harrah’s, The LINQ, Las Vegas Convention Center, Westgate Resort & Casino, SAHARA Las Vegas.
I'm staying far away. What's the parking situation?
There is parking available, the closest are the diamond and silver lots. When we learn more about our contracted parking arrangement we will publish it on the hotel & venue page.
Will there be any kind of shuttle service from the LVCC to strip hotels?
No
What is the smoking policy at the LVCC?
Smoking is not allowed on the LVCC property, the existing outdoor terraces, or any balconies. Marijuana & tobacco vaping is 100% prohibited, there are uniformed officers with K9 on site trained to smell vaping.
You will have to go outside completely to smoke. Smoking is allowed in the parking lots and sidewalks.
What are the LVCC rules regarding contests/parties/shenanigans?
There will definitely be differences and we expect things to be better for us. We are learning what fees will be to serve alcohol and food.
If you are looking to throw an event, please fill out the call for parties form.
https://defcon.org/html/defcon-32/dc-32-cfopp.html
Can we give away or sell drinks/food/candy at DEF CON?
Please see above. We don’t know all the rules yet.
Will DEF CON provide water stations again?
There are water fountains and modern bottle filling stations throughout all 3 floors of the con space. We will include bottle stations on our floor plan map. Remember to bring your bottles!
Since we're going to be in one big non-casino space all day, will there still be Chill-out areas with areas to relax and refuel?
We will have several chill-outs for attendees to sit, rest, hack and or socialize.
The LVCC West Hall has an exclusive food court for our use during the con.
The food hall includes options from: Dunkin' Express, Metro Pizza, Brand Burgers & Fries, Fancy Wok Asian Kitchen, Go Natural, The Roost Farm Fresh Chicken.
Will there be a pool party?
We are securing a pool. If you are interested in throwing a party or a private pool event please contact
exhibitors@defcon.org
Will the "Secure DEF CON Wifi Network" work the same way?
The DEF CON NOC will be on the job, and providing secure Wifi.
To learn more about the NOC please visit:
https://noc.defcon.org/
HEALTH & PANDEMIC QUESTIONS
What health measures/protocols is DEF CON taking to ensure a safe environment on-site?
DEF CON is working closely with the venue to provide a safe and healthy experience for all. We will comply with whatever safety measures are required of us.
How's the air turnover in the LVCC?
From the LVCC: “The LVCC air filters have a quality rating of MERV 13 and they've increased replacement rate of air filters. The LVCC is also among the first convention centers in the nation to pursue the prestigious GBAC Star Accreditation Program, an accreditation that establishes gold standard cleaning, disinfection and infectious disease prevention protocols that meet or exceed the industry’s highest standards of cleanliness for pathogens like the novel coronavirus.”
What is your mask policy?
We will have masks on hand for anyone who needs them as well as a finite number of test kits onsite as well. There will be lists of resources for testing and treatment available in the program and at the Info Booth.Wearing a mask remains the safest option, but with these changes our policy is masks strongly recommended.
What will room capacity be?
Room capacity is always set to be capped at fire code standard capacity. In case of changing health and safety recommendations, limits will be reviewed and revised at the direction of Southern Nevada Health District (SNHD).
What's the Lost and Found policy at DEF CON?
If someone comes looking for a lost item, dispatch is radio’d to inquire if it’s been reported found. If you can’t find an NFO booth, they are marked on the maps in the printed program, website, and the DEF CON Hacker Tracker App. You can call DEF CON ’s lost and found at 1-725-377-5045.
LVCC Lost and Found: Central Lobby and West Lobby Security Office. Phone: 702-943-3532 Dispatch closes at the start of DEF CON Closing Ceremonies on Sunday August 11th and all lost items that have not been collected are turned over to the LVCC.
Will you have working elevators and escalators this time?
Yes, the LVCC has several banks of elevators and escalators. The Sahara has replaced all of it's elevators as well, everything is shiny and new.
Do you have ADA or HDA Information?
The DEF CON 32 HDA Guide will be published at the link below when the team receives new information.
https://defcon.org/html/links/dc-hda.html
All hotels are ADA accessible and have staff available to assist attendees before and during the convention. Registered service animals are welcomed by all hotels, and relief areas are provided. These areas are marked on the HDA maps. If you require assistance with hotel issues you may contact any DEF CON Goon, the DEF CON information desk, or the appropriate point of contact for the hotel.
Where can I find general ADA assistance for the Las Vegas Convention Center?
Las Vegas Convention and Visitors Authority
ADA Coordinator
702-892-0711
Nevada Relay Service
Voice: 1-800-326-6888 or Dial 711
TTY/ASCII/HCO: 1-800-326-6868 or Dial 711
Follow the link for the LVCC Guide for visitors with special needs.
https://www.vegasmeansbusiness.com/p...eeds-visitors/
Where can I find interpretation services?
Should you require audio, video or personal interpretation services please contact American Language at 1-800-951-5020
Do you have a plan in case of evacuation?
Customer safety staff at the LVCC is trained to handle emergency situations, they are operational 24 hours a day and become the communications center and command post in the event of an emergency. DEF CON will be working closely with the LVCC customer safety staff for to strategize an emergency action plan. We will update the venue page with emergency exit information as it becomes available.
Will any of the "Call For Everything" deadlines be changes as a result of the new venue?
Calls for Papers, Workshops, Demo Labs, and Policy talks were postponed and expected to launch February 15 2024.
https://defcon.org/html/defcon-32/dc-32-cfi.html
Will any deadlines change for content creators?
No deadlines are set to change.
What's the theme for DEF CON 32?
Our official theme is here:
https://defcon.org/html/defcon-32/dc-32-theme.html
Return to Index
© 1992-2024 DEF CON Communications, Inc. All Rights Reserved | DEF CON Policies | DMCA Information
DEF CON FAQ
Frequently asked questions about DEF CON
What is DEF CON?
DEF CON is one of the oldest continuously running hacker conventions around, and also one of the largest.
How did DEF CON start?
Originally started in 1993, it was a meant to be a party for member of "Platinum Net", a Fido protocol based hacking network out of Canada. As the main U.S. hub I was helping the Platinum Net organizer (I forget his name) plan a closing party for all the member BBS systems and their users. He was going to shut down the network when his dad took a new job and had to move away. We talking about where we might hold it, when all of a sudden he left early and disappeared. I was just planning a party for a network that was shut down, except for my U.S. nodes. I decided what the hell, I'll invite the members of all the other networks my BBS (A Dark Tangent System) system was a part of including Cyber Crime International (CCI), Hit Net, Tired of Protection (ToP), and like 8 others I can't remember. Why not invite everyone on #hack? Good idea!
Where did the name come from?
The short answer is a combination of places. There as a SummerCon in the summer, a HoHoCon in the winter, a PumpCon during Halloween, etc. I didn't want any association with a time of year. If you are a Phreak, or just use your phone a lot you'll notes "DEF" is #3 on the phone. If you are into military lingo DEF CON is short for "Defense Condition." Now being a fan of the movie War Games I took note that the main character, David Lightman, lived in Seattle, as I do, and chose to nuke Las Vegas with W.O.P.R. when given the chance. Well I knew I was doing a con in Vegas, so it all just sort of worked out.
There are several resources that will give you an idea of what DEF CON is all about.
DEF CON Press: through the prism of the media
DEF CON Groups: Local groups that meet
DEF CON Media Server: DC 1 to the present, captured
Google: always a good research starting point
Just remember, DEF CON is what you make of it.
When and where is DEF CON?
DEF CON is generally in the last week of July or first week of August in Las Vegas. DEF CON 32 will be held August 8th through August 11th, 2024. Many people arrive a day early, and many stay a day later.
Isn't there a DEF CON FAQ already?
Yes, an unofficial one. It's quite humorous, sometimes informative, and DEF CON takes no responsibility for its content. It is archived here.
What are the rules of DEF CON?
Physical violence is prohibited. Harassment of any kind is prohibited. We don't support illegal drug use. Minors should be accompanied by their parent(s) or guardian(s). Please refrain from doing anything that might jeopardize the conference or attendees such as lighting your hair on fire or throwing lit road flares in elevators. DEF CON Goons are there to answer your questions and keep everything moving. Hotel security is there to watch over their property. Each has a different mission, and it is wise to not anger the hotel people. Please be aware that if you engage in illegal activities there is a large contingency of feds that attend DEF CON. Talking about how you are going to bomb the RNC convention in front of an FBI agent is a Career Limiting Move!
You can view the DEF CON Code of Conduct at https://defcon.org/html/links/dc-code-of-conduct.html.
Is DEF CON cancelled?
No.
What is there to do at DEF CON?
DEF CON is a unique experience for each con-goer. If you google around you'll find dozens of write-ups that will give you an idea of what people have experienced at DEF CON. Trust write-ups more than media articles about the con. Some people play capture the flag 24x7, while many people never touch a computer at DEF CON. Some people see every speech they can, while others miss all speeches. Other activities include contests, movie marathons, scavenger hunts, sleep deprivation, lock picking, warez trading, drunken parties, spot the fed contest, the official music events. Because DEF CON is what the attendees make of it, there are more events than even we are aware of. Half the fun is learning what happened at DEF CON after the fact!
I'm not a hacker, should I go to DEF CON?
Many people have different definitions of what is a ‘hacker’. I would recommend looking at previous years speeches, and write-ups from past attendees - this should give you a good idea if DEF CON is for you. This hacker FAQ might give you some insight into the matter as well. If you do not have any technical interests, DEF CON is probably not for you. Sure there is a lot of socializing you can do, but technology and hacking is the core of the con.
Do criminals go to DEF CON?
Yes. They also go to high school, college, work in your workplace, and the government. There are also lawyers, law enforcement agents, civil libertarians, cryptographers, and hackers in attendance. Ssshhh. Don't tell anyone.
What are Goons?
They are the staff at DEF CON. They have many roles including safety, speaker coordination, vendor room coordination, network operations, et cetera... Please try to be helpful to them if they make requests of you. If any goon tells you to move, please do so immediately as there may be safety issues they are attempting to address.
How can I help out or become a Goon?
The staff at DEF CON has grown organically. All positions have some degree of trust associated with them, so typically new goons are ‘inducted’ by friends of existing goons. There are many random points when goons need help and may ask people for help, generally for helping move stuff or other tasks that don't require high amounts of trust or unsupervised work. Just because you help out doesn't make you a goon. If you really want to be a goon, talk with one and see how much work they actually do (Hint: you may want to enjoy being at DEF CON, not working full-time at it). One year the network group got a new Goon when a networking engineer was needed, and he came to the rescue. The intent behind the goons is not to be elitist, but to have a network of trusted people who can help run the conference - please do not feel upset if you are not chosen to be a goon.
How can I help or participate?
DEF CON is not a spectator sport! Before the con, during, and after there are chances for you to get involved. Before the con you can read about the contests and maybe sign up for one like Capture the Flag. There are artwork contests for shirts and posters. You can practice your lock pick skills, or just get your laptop all locked down and ready to do battle. Organize your .mp3s. Check out the DEF CON Forums to see what other people are up to. If you want to create your own event, you can do that as well - you will not get official space or sanctions, but virtually every official event at DEF CON started out as an unofficial event.
I would love to see XYZ event, how do I make this happen?
Virtually all events at DEF CON were conceived by the attendees. The DEF CON forums are a great place for recruiting help for an event you want to put on, and making sure your efforts aren't being duplicated. If it doesn't require resources from DEF CON (space, namely) you generally don't have to ask anyone’s permission. Most events are unofficial until they've been going on for a couple of years. Please let us know if you have an idea for an event, we may help facilitate or promote it. Email [suggestions at DEF CON dot org] to keep us in the loop.
How can I speak at DEF CON?
You can submit a response to our CFP (opening soon). All entries are read and evaluated by a selection committee. We would love to have your submission. The call for papers usually opens in January and closes mid-May.
I'm press, how do I sign up, why can't I get in for free (I'm just doing my job)?
Please email press[at]defcon[d0t]org if you wish press credentials. Lots of people come to DEF CON and are doing their job; security professionals, federal agents, and the press. It wouldn't be fair to DEF CON attendees if we exempted one group from paying. If you are a major network and plan on doing a two minute piece showing all the people with blue hair, you probably shouldn't bother applying for a press pass - you won't get one. If you are a security writer or from a real publication please submit, and someone will respond with an answer.
I want to sell stuff, how do I do this?
If you want a space in our vendor area, you need to apply. Because of limited space and our attempt to have a diversity of vendors, you may not be able to get a booth. It is wise to think of staffing issues - if you are one person do you want to spend your entire time behind a vendors booth?
What are the different price rates?
Everyone pays the same: The government, the media, the ‘well known hackers’, the unknown script kiddies. The only discount is for Goons and speakers, who get to work without paying for the privilege.
How much is admission DEF CON, and do you take credit cards?
The price for DEF CON 32 is $460 USD cash at the door. We do this for a number of reasons. Paying in cash protects your privacy and we can’t be forced to hand over records we don’t collect. Still, offering online registration for DEF CON Safe Mode taught us we had some attendees who really benefit from the option for things like group orders and expense report requirements.
For those attendees who need a credit card option we’ll continue to offer online ticket sales for $480 USD at shop.defcon.org. We hope this makes things easier for the community members who need it.
Does my underage child need a badge?
Children under the age of 8 will not need to purchase a badge.
Can I get a discount on DEF CON badges?
DEF CON charges one price regardless of your social status or affiliation. Please know that we depend on attendee income to pay the costs of the conference and don't have sponsors to help defray the expenses.
We sometimes get requests for discounts [students, veterans, children], unfortunately we don't want to try and validate if you are a current student, look at your ID to determine your age, decode military discharge papers, etc.
If you really want to attend DEF CON for free then do something for the con.
You could:
Submit a CFP and be an accepted speaker or workshop instructor.
Work on a contest, event, or village.
Qualify for CTF/Contests that include entry.
Find a team to become a Goon newbie.
Contribute to content, or perform some entertainment.
I need a letter of invite for my visa application, how do I get that?
In most cases, DEF CON can send a signed letter of invite, usually within a few short business days once we have all the info. If you also require verification of housing, we can put you in touch with someone to help you get your hotel stay organized, let us know if you need that.
Along with your request, please email us the following to info(at)defcon(.)org
Name as is on passport:
Passport number:
Country of issue:
Date of issue:
Date of expiration:
Country of origin:
DEF CON is too expensive, how can I afford it?
Many people have made an art and science out of coming to DEF CON very cheaply. Here are a couple of tips.
Travel: Buy airfare in advance, go Greyhound, Carpool, hitch-hike. (Note: this may be dangerous and/or illegal.)
Lodging: Share rooms - some people have up to 10 people they share a room with, find a hotel cheaper than the one that the conference is scheduled at, stay up for three days, etc. (note: this can be hazardous to your health.)
Food: Pack food for your trip, go off site to find food, eat in your hotel rooms, and look for cheap Vegas food at Casinos. (Look for deals and specials that are trying to get you in the door to gamble.)
Booze: You don't need to drink. Brew your own and bring it. (It's been done.)
Entrance: Admission can be saved, mow some lawns. Try to go to another 4 day event for cheaper than this that offers so much. We have increased the fees slowly over the years, but also the amount and quality of events have increased.
Inevitably people will try to do some math and pretend that DT gets rich each DEF CON - they seem to lack the ability to subtract.
How many people typically attend DEF CON?
There have been roughly 25-28k attendees in the last few (pre-COVID) years of DEF CON. DEF CON 27 had a record showing with approximately 30,000.
Is there a network at DEF CON?
Why yes, DEF CON is FULLY network-enabled. Now that we've perfected the art of a stable hacker con network, we're ascending to a higher level - we're providing you a network that you feel SAFE in using! Since DEF CON 18 we're WPA2 encrypted over-the-air, with a direct trunk out to the Internet. No peer-to-peer, no sniffing, just straight to the net (and internal servers). We'll provide login credentials at Registration. We know the LTE airwaves will be saturated so we're putting our own cred on the line to give you a net that even we would put our own mobile phones on.
If you're feeling frisky, we'll still have the traditional "open" network for you - bring your laptop (we'd recommend a clean OS, fully patched--you know the procedure) because we don't police what happens on that net. Share & enjoy!
What is the age limit?
People have brought children to DEF CON - it is not recommended to do this unless you are going to constantly supervise them. It is generally an ‘adult’ atmosphere (language, booze, et cetera). If you've never been to DEF CON, you may want to refrain from bringing your children (unless they are demanding that you bring them). While there are no age limits, we have consistently cooperated with parents and/or private investigators who are looking for children that ‘ran away from home’ to go to DEF CON. You will have to be 21 to reserve a room.
What is a DEF CON "Black Badge"?
The Black Badge is the highest award DEF CON gives to contest winners of certain events. CTF winners sometimes earn these, as well as Hacker Jeopardy winners. The contests that are awarded Black Badges vary from year to year, and a Black Badge allows free entrance to DEF CON for life, potentially a value of thousands of dollars.
How can I get a hold of DT? I tried to mail him and haven't seen a response yet.
DT doesn't dislike you, isn't trying to hurt your feelings, and bears you no ill will. The fact is he gets an unmanageable load of mail continually. Mailing him again may elicit a response. Try mailing FAQ (at) DEFCON.ORG if you have a general question that isn't answered here or in the forums.
Is it hot in Vegas?
Yes. Bring sunscreen (high SPF), do not fall asleep near the pool (lest you wake up to sunburn), and do not walk far in the sun unless you are experienced in dealing with extreme heat. The sun is dangerous in Las Vegas. Sleeping in lawn chairs is a sure way to wake up to severe burns in the morning when that bright yellow thing scorches your skin. Drink plenty of water and liquids - remember that alcohol will dehydrate you.
What should I bring?
It depends on what you're going to do at DEF CON. This is discussed in quite some depth on the unofficial DC FAQ, as well as a thread in the DC Forums. You may want to bring fancy (or outrageously silly) clothes for the official Music events, on Friday and Saturday nights, where everyone shows off nifty attire.
How much do rooms cost, and how do I reserve a room?
The DEF CON 32 group room registration is evolving! We are working on room blocks at several hotels.
Currently we have a block at Sahara: https://book.passkey.com/e/50769948
Check the the DEF CON 32 venue page periodically for more as we add them
How much is internet access?
We are looking into this. Free (and possibly more dangerous) internet access is available in the convention area.
Will the hotels broadcast the speeches on their cable system?
DEF CON TV has succcessfully streamed all tracks to all the hotels in the past, and a couple of tracks out to the internet, for several years now. We are navigating a new venue and new hotels, so stay tuned. If we can, we probably will!
Will we have DEF CON branded poker chips?
You will have to attend DEF CON to find out.
Will conference attendees have entire floors of hotel rooms to themselves?
Probably not. Hotels have been very cooperative in attempting to centralize the DEF CON attendees, for their convenience and ours, but there will be non-DEF CON attendees in hotel rooms next to us.
This FAQ didn't answer my questions, or was unclear, how can I get further information?
Check out the DEF CON Forums to ask follow up questions.
Return to Index
© 1992-2023 DEF CON Communications, Inc. All Rights Reserved | DEF CON Policies | DMCA Information
Villages Table
Each Village, as it’s name may imply, specializes in a topic or aspect of security or computers.
One Page All Villages list with descriptions
DEF CON 32 All Villages Forum page
You may need to scroll to the right to see all info
Contests Table
Various contests, some lasting all 4 days of DEF CON, some short time on stage
The Contests will be in LVCC West, Hall 4
One Page All Contests list with descriptions
DEF CON 32 All Contests Forum page
You may need to scroll to the right to see all info
DemoLabs Table
Brief demonstrations for people to show off their project.
The DemoLabs are in rooms at LVCC West, Level 3
One Page All Demolabs list with descriptions
DEF CON 32 All Demolabs Forum page
You may need to scroll to the right to see all info
Workshops Table
Longer, more detailed, hands on, lasting half a day.
These have limited seating. These will fill up VERY quickly!
All of the workshops are SOLD OUT at this time.
One Page All Workshops list with descriptions
DEF CON 32 All Workshops Forum page
You may need to scroll to the right to see all info
SOLD OUT – Sold Out – 64-bit Intel Assembly Language Programming for Hackers – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Capture the Flag 101 – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Crash Course in Physical Access Control Systems – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Dissecting and Defeating Ransomware’s Evasion Tactics – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Dissecting Malware for Defense – Crafting Custom Yara Rules – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Dodging the EDR Bullet: A Workshop on Malware Stealth Tactics – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Email Detection Engineering and Threat Hunting – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Finding the Needle: An Introduction to Detection Engineering – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Flipping the Coin: Red and Blue Teaming in Windows Environments (++) – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – From an attacker’s lair to your home: A practical journey through the world of Malware – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Ghidra Analysis & Automation Masterclass – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Hack the connected plant! – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Hacking Apps on Salesforce – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Hacking The Metal: A Spark of Intelligence – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Hide your kids, turn off your Wi-Fi, they Rogue APing up in here; 201 – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Industrial Control Systems: how to secure them in practice! – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Learning to Hack Bluetooth Low Energy with BLE CTF – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Long Live Empire: A C2 Workshop for Modern Red Teaming – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Machine Learning for N00bs – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Master Class: Hands-On Machine Learning to Enhance Malware Analysis, Classification, and Detection – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Med Team vs Red Team: Intro into Medical Device Hacking – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Offensive SCCM: Abusing Microsoft’s C2 Framework – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Playing with RFID – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Sharp Security from All Angles: Mastering Security in .NET Core 8 and Angular 17 Applications – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Small Choices, Global Repercussions: A Tabletop Exercise about Decision-Making in Healthcare Cybersecurity – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Supercharge SAST: Semgrep Strategies for Secure Software – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Tracing The Pain Away – Practical Binary Tracing Techniques For Defeating Modern Malware Protections – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Traumatic Library Loading : If you want to use it, you have to implement it… – Sold Out
Workshop Info
|
SOLD OUT – Sold Out – Whitebox Web Exploit Development – Sold Out
Workshop Info
|
Paid Training Table
2 day training sessions on the Mon and Tue after DEF CON. There will be an additional cost for these.
One Page All Paid Training list with descriptions
DEF CON 32 All Paid Training Forum page
DEF CON 32 Training Signup Pages
You may need to scroll to the right to see all info
Party,Gather,Event Table
Various Parties, Gatherings, and Events
One Page All Parties, Gatherings, Events list with descriptions
DEF CON 32 All Parties, Gatherings, Events Forum page
You may need to scroll to the right to see all info
Vendors Table
Vendors attending DEF CON
One Page All Vendors list with descriptions
The Vendors are in LVCC West, Hall 4
Exhibitors Table
Exhibitors attending DEF CON
One Page All Exhibitors list with descriptions
DEF CON 32 All Exhibitors Forum page
The Exhibitor room is in LVCC West, Level 1, Hall 3
You may need to scroll to the right to see all info
Communities Table
A group of people with common interests, but don’t qualify as a Village, is a Community,
One Page All Communities list with descriptions
DEF CON 32 All Communities Forum page
You may need to scroll to the right to see all info
Links to DEF CON 32 related pages
Links
DEF CON . org Links
DEF CON
Main page
DEF CON 32
Home Page
DEF CON
Recent News
DEF CON
FAQ
DEF CON 32
FAQ
DEF CON 32
Venue
DEF CON 32
Schedule
DEF CON 32
Policy
DEF CON 32
Training Signup
DEF CON CTF
Nautilus Institute, Twitter
@Nautilus_CTF
DEF CON
YouTube channel, prev years talks
DEF CON
Forum Calendar
DEF CON 32
Planning Forum page
DEF CON 32 Hackers with Disabilities
HDA Infopack
DEF CON 32
Speakers & Presentations Forum page
DEF CON 32
Villages Forum page
DEF CON 32
Contests Forum page
DEF CON 32
Parties & Gatherings & Events Forum page
DEF CON 32
Demolabs Forum page
DEF CON 32
Workshops Forum page - Registration opened on July 5 at Noon PDT! - All Workshops are Sold Out!
DEF CON 32
Paid Training Forum page - These occur the 2 days following DEF CON
Thanks to the InfoBooth crew for providing access to their backend database. <claps> to their hard work!
Combined Schedules of DEF CON, Villages, and everything else DC32
Hacker Tracker -
Android and
IOS - the official DEF CON schedule app
The ONE! - A consolidated DEFCON 32 schedule in multiple file formats - html, PDF, CSV, ICAL, epub, mobi, Google calendar
info.defcon.org - the official DEF CON InfoBooth site
Other Interesting Links
DEF CON 32 Planning Highlights
Hackers with Disabilities DEF CON 32
HDA Infopack
@defconparties -
calendar
defconmusic - Schedule/News from the DC Artists & Entertainment ( A&E ) Department
DEFCONorg Twitch stream
defconmusic
DEF CON Entertainment Twitch stream
defconmusic
YouTube channel
DCTV - DEF CON TV: Twitch streams and Hotel TV channels
#badgelife spreadsheet of unofficial badges for DC32
@qumqats Twitter
List of Village accounts to assist in watching Village happenings
Other cons during #SummerHackerCamp
Guides/Tips/FAQs
The Definitive Guide to DEF CON
DEF CON A&E - Resources - Rough Distances and Maps
DEF CON A&E - Resources - Packing List
Guide to Attending DEF CON 31
How to Survive Def Con 2022
OpSec For DEF CON 30
DCG 201 Hacker Double Summer 2023 Guides
Birds of a Feather-Resources for 2022 Hacker Summer Camp
Lonely Hackers Club - DEF CON n00b guide -
reddit thread
The Lost Policymaker's Guide to Hacker Summer Camp
Holon
DEF CON 30 Preparation
DEF CON: The Survival Guide
Preparing for "Hacker Summer Camp"
General / previous years
DEF CON for N00bs
JK-47 - BSidesLV & DEFCON Conference Tips
Just another DEF CON guide
HACKER SUMMER CAMP 2018 GUIDE
On Attending DefCon





































































