DCTV is Live!

DCTV is online! Jump on
dctv.defcon.org
for links to the DEF CON 33 live streams on YouTube and Twitch.
Get that DEF CON however works best for you.

Welcome to the "One Schedule to Rule them All!". Thank you for your interest by using this. This is an attempt to make things easier for you, the DEF CON attendee, to figure out the when/what/where during the chaos of DEF CON 33.
It started out simple. I had a Kindle and wanted an ebook of the schedule so I didn't have to wear out the paper pamphlet by pulling it out after every talk to figure out where to go next. Back then there was only the main DEF CON tracks, not really any Villages, and production of the ebooks were easy. Over time the Village system developed with a resulting multiplication in complexity, both for attendees and for my production. The offerings no longer include epub and mobi formats and instead now include html, csv, PDF, ical, public Google calendar, and mysql dump format files. Hopefully you'll find something of use.
The intent is still to be a resource to answer the question at the end of an hour of "What's next?"
As a general rule I do not include:Be sure to check out the Links section at the bottom of this. Most all of the events listed here were derived from these links and a Infoboot data feed. There is much more going on at DEF CON than what is listed here.
Check out the Guides/Tips/FAQs links if you're new to Las Vegas.And finally, this is only as good as the ideas and information used to generate it. I welcome your constructive suggestions and comments. Please send them to qumqats@outel.org
Have a good time at DEF CON 33!

Adversary Village is a community initiative which primarily focuses on adversary simulation/emulation, purple teaming, and adversary tradecraft. The village covers offensive operations, threat/APT/ransomware simulation, breach and adversarial attack simulation, supply chain security, adversary tactics, research on nation-state-sponsored threat-actors, adversary intelligence, adversarial mindset, philosophy, and hacker survival skills.
The goal of the Adversary Village is to build an open security community for the researchers and organizations, who are putting together new means, methodologies towards the simulation-emulation of adversary tactics and collaboration.
Subsequent to feedback from past editions, Adversary Village shall focus on hosting hands-on deep technical workshops, live demonstrations, panel discussions and a ton of other hands-on activities on adversarial attack simulation/emulation, offensive tradecraft to engage and educate the community. Adversary Village would have the following hands-on activities for this year at DEF CON;
Adversary simulator and purple teaming hands-on booth
Adversary Simulator booth is a volunteer assisted activity, which has hands-on adversary emulation plans and exercises specific to a wide variety of threat-actors; these are meant to provide the participants with a better understanding of adversarial attack emulation. The booth will be hosting a simulated environment meant to recreate enterprise infrastructure, operational technology environment, which serves targets for various attack simulations. The hands-on simulator booth also hosts an activity, which would need the participants to generate their own adversary emulation plans to assess the efficacy of the defense systems based on publicly available cyber threat intelligence.
Choose-your-own-Adversary-Adventure Tabletop Game
Adversary adventure is a story-scenario based, interactive, cyber war-gaming, choose-your-own adventure model interactive game. This is a gamified version of table-top exercises which is presented to the participants as they can choose to play as an attacker, post exploitation OR a Defender who is defending against an attacker group-threat actor OR even play as a CISO who is dealing with an adversarial situation such as a ransomware incident.
Hands-on deep technical workshops
Adversary Village will feature a limited number of deep technical workshops focused on advanced adversary tradecraft and techniques.
Hands-on guided breach and offensive attack simulation exercises
This area will feature guided attack simulation exercises for participants to engage with. There will be a few scenario-focused activities, "Breach-the-Hospital", "Breach-the-Office", “Breach-the-Bank” etc., visually represented by modular-brick-LEGO sets. A simulated cyber range will be available for each scenario, providing an exact replica of an enterprise production environment. We will provide a detailed walkthrough of the attack scenarios, including Tools-Techniques-and-Procedures, commands and how-to guides, demonstrating how to attack and breach the target environment. This exercise will give participants a clear understanding of how threat actors infiltrate corporate environments.
Adversary Wars CTF
Adversary Village will be hosting "Adversary Wars CTF", where the participants will have to pose as adversaries and replicate adversarial actions against each element of a “target” organization. Adversary Wars would have real world challenge scenarios and challenges, where the participants can perform various attacks and learn new TTPs. To visualize the CTF environment, the contest area will feature a miniature model of the city made using interlocking-plastic-bricks. The breached components will be physically marked in the city model as the CTF progresses. There will be prizes, complimentary hoodies (yes, the iconic adversary village hoodies), free t-shirts, cool stickers, village coins, badges, and various other swags.
Links:
Join us at the AI Village for interactive demonstrations at the intersection of AI and security. We’ve got something new this year with a full purple team demonstration from the AI Cyber League.
For the third Generative Red Team we are going to “red team” the evaluations that establish a model’s performance. We are bringing several model systems built to do different tasks each with their own model card. These model cards will define uses and restrictions the model creators want and determine what we mean by “trust” when it comes to fuzzier concepts like “can write good Rust” and “doesn’t help you hack”. This model card will be built off of open source evaluations that prove and establish how effective the model is. We will be paying bounties for findings against the evaluations that the model cards used to make their claims.
Following the success of last year's real-time deepfake demonstrations, we're taking things to the next level. This year, we're showcasing five different deepfake systems across a spectrum of computational requirements – from high-end professional setups to consumer-grade hardware that's becoming increasingly accessible. You can see how detections we have will break down as compute per dollar keeps improving.
Links:
The AIxCC Finals will unfold at DEF CON 33 in August 2025. The top seven teams who qualified during Semifinals will compete for a grand prize of $4 million.
The AIxCC Final Competition will introduce new challenge repositories and vulnerabilities, encouraging teams to improve upon their current CRS implementations and push forward their systems' capabilities in terms of robustness, scale, and real-world impact.
Links:
Come immerse yourself in everything the world of application security has to offer. Whether you are a red, blue, or purple teamer, come learn from the best of the best to exploit software vulnerabilities and secure software. Software is everywhere, and Application Security vulnerabilities are lurking around every corner, making the software attack surface attractive for abuse. If you are just an AppSec n00b or launch deserialization attacks for fun and profit, you will find something to tickle your interest at the AppSec Village.
Software runs the world. Everything from IoT, medical devices, the power grid, smart cars, and voting apps - all have software behind them. Such a variety of topics will be reflected in our cadre of guest speakers representing all backgrounds and walks of life.
AppSec Village welcomes all travelers to choose from talks and workshops by expert community members, an all-AppSec-focused CTF, contests that challenge your mind and your skillz, and more. Bring your thirst for knowledge and passion for breaking things, and your visit to AppSec Village will be thrilling!
Links:
The aviation and space industries, security researchers, and the public share a common goal: safe, reliable, and trustworthy aviation and space operations. For too long, negative perceptions and fractured trust on all sides have held back collaboration between the aviation, space, and security researcher communities that has advanced safety, reliability, and security of other industries. As the traditional domains of aviation safety and cybersecurity increasingly overlap, more effective collaboration between stakeholders ensures we will be safer, sooner, together.
Through the Aerospace Village, the security research community invites industry leaders, researchers and academia interested in aviation and space security, safety, and resilience to attend, understand, collaborate together to achieve our common goals. Empathy and understanding build common ground, while acts and words likely to increase division between these two communities undermine these efforts. The Aerospace Village welcomes those who seek to improve aviation and space security, safety, and resilience through positive, productive collaboration among all ecosystem stakeholders.
Our Goal
The Aerospace Village is a volunteer team of hackers, pilots, and policy advisors who come from the public and private sectors. We believe the flying public deserves safe, reliable, and trustworthy air travel which is highly dependent on secure aviation and space operations.
Links:
The global bug bounty community has witnessed exponential growth, with thousands of members actively engaged in the field. This thriving ecosystem now represents a legitimate and sought-after profession for hackers and cybersecurity specialists. After a big success and great feedback during the first ever Bug Bounty Village during DEFCON 32, We want to be part of DEFCON 33 and keep celebrating the bug bounty community, where hunters, learners, and enthusiasts can converge, interact with top-tier hackers, attend insightful workshops, talks, and immerse themselves in hands-on activities.
With over 20 workshops, panels and talks, the Bug Bounty Village at DEFCON 32 was a huge success. The room was completely full of hackers at all times, Some of the best bug bounty hunters in the community were part of our village to share knowledge, create content, teach others, and also, to make new friends. With waiting lines of over 100 people waiting to get in for some of our workshops, we have demonstrated that there is a huge interest in Bug Bounty to remain as a specific village at DEFCON, and have that special place in the biggest hacker conference in the world, where the Bug Bounty community can connect, grow and help others become the future of Bug Bounty.
Links:
At the Biohacking Village, attendees can expect an immersive, hands-on experience at the intersection of cybersecurity, healthcare, and medical technology, offering opportunities to learn, explore, and collaborate on some of the most pressing challenges in the industry.
What Attendees Can Learn at the Biohacking Village:
The Biohacking Village is your gateway to understanding and addressing the complex challenges of medical technology and cybersecurity. Attendees will leave equipped with knowledge, skills, and connections to drive meaningful change in the industry.
Links:
The Blacks In Cybersecurity (B.I.C.) Village seeks to bring culturally diverse perspectives to the holistic Cybersecurity community; by way of a series of talks and a capture the flag event. In providing these activities, we hope to help highlight Black experiences, innovations in the field, Black culture and educate the community about Black history.
In doing this, we believe that we can better educate and normalize the discussion of deficiency or prejudices in Cybersecurity education/development for minority communities. We also believe this effort can be translated to aid in eradication of these issues in the Cybersecurity and Hacker/Maker community and allow for more diverse hobbyists and professionals to engage and contribute.
Links:
Blue Team Village (BTV) is both a place and a community built for and by people who defend computer systems, networks, and people against cyber attacks. It's a place to gather, talk, share, and learn from each other about the latest tools, technologies, and tactics that our community can use to detect attackers and prevent them from achieving their goals.
The Blue Team Village's Project Obsidian is a defensive cybersecurity learning experience that provides attendees with the opportunity to gain knowledge of Incident Response (IR), Digital Forensics (DF), Malware Analysis, Cyber Threat Intelligence (CTI), and Cyber Threat Hunting (CTH). Deep dive into technical topics through training and exercises that provide practical hands-on experience across each discipline. Project Obsidian 101 trainings provide cybersecurity knowledge that will enable attendees to develop the skills needed to be successful in their current and future roles.
Two of the most valuable takeaways are how to strategically approach a task and the operational processes supporting each task's objectives. Knowing 'how' to do something is only part of the challenge. Knowing 'when' and 'why' to perform specific tasks adds the necessary context to develop the full story of defensive cybersecurity.
Links:
For over a decade, we’ve been leading the charge in automotive security, and this year, we’re shifting into high gear! Get ready for an electrifying DEF CON 33 experience packed with interactive challenges, exclusive badges, and mind-bending exercises designed to supercharge your skills.
Join us and make this DEF CON one for the record books!
Links:
With the industry’s rapid growth in cloud infrastructure, the presence of an open platform to discuss and showcase cloud research becomes a necessity. Cloud village is an open platform for researchers interested in the area of cloud security. We plan to organise talks, tool demos, CTF and workshops around Cloud Security and advancements.
Our CTF will be a jeopardy style 2.5 days contest where participants will have to solve challenges around Cloud infrastructure, security, recon, etc. These challenges will cover different cloud platforms including AWS, GCP, Azure, Alibaba, Digital Ocean, etc. We will also reward our top 3 teams with awards.
Links:
Launched in 2014, Crypto & Privacy Village (CPV) is a community-run village centred on privacy and cryptography that aims to educate and inform the general public, students, educators, hackers, security and privacy professionals, and policymakers. We provide a unique hybrid space that features talks; chill space for relaxing with friends, doing CTFs, and cross industry networking; the Gold Bug Challenge and desk for hints and support; privacy-related art installations; and an information desk for questions about privacy and cryptography. Come talk with us about facial recognition technology, privacy-preserving data analytics, or crypto backdoor laws!
Links:
The Data Duplication Village has all the updated bits and bytes available from infocon.org packed up into nice, neat packages. If you're looking for a copy of just about any security con talk known to hacker-kind or a copy of the VX-Underground archive (along with a few hundred gigs of cat pictures), you'll find it here. Our village provides a "free-to-you" service of direct access to terabytes of useful data to help build those hacking skills and allow open discussions with other storage enthusiasts.
We'll also be partnering with DC Next Gen to ensure that our future generations have the opportunity to explore the details of how past and current data storage works!
Links:
Embedded systems exist at the intersection of hardware and software, built to accomplish a specific task. Often these disciplines are dealt with individually, but understanding the custom relationships between hardware and software is key to performing security research on these devices.
Embedded Systems Village advances the security of embedded systems by hosting hands-on hacking workshops, showcasing new security research demos, and organizing exciting hacking contests to educate attendees and manufacturers on the approach hackers use to attack these devices. Attendees will leave the village with an understanding of how to reduce complex, exotic devices to their underlying embedded components and to extract the information required to use the tools and techniques taught at other villages where embedded systems are on display.
Links:
Gaming and cybersecurity intersect in many exciting and interactive ways. Our mission is to delve into various aspects of game security, fostering an environment of exploration, play, and learning. At the Game Hacking Community, participants can engage in activities ranging from modding games to exploring the intricacies of memory hacking and multiplayer cheats and learning about game malware. Whether you're a beginner or an experienced hacker, we will have presentations and activities to challenge your skills. Be part of the evolution of game security. Dive into our activities, engage with other game hackers, and explore opportunities to contribute to and support the Game Hacking Community. Let's play, learn, exploit, and perhaps even profit. Our community focuses on learning and does NOT endorse cheating in competitive online games.
Links:
Every day our lives become more connected to consumer hardware. Every day the approved uses of that hardware are reduced, while the real capabilities expand. Come discover hardware hacking tricks and tips regain some of that capacity, and make your own use for things! We have interactive demos to help you learn new skills. We have challenges to compete against fellow attendees. We have some tools to help with your fever dream modifications. Come share what you know and learn something new.
Links:
Ham Radio has been considered to be the original group of hackers, launching before computers, integrated circuits, and even the transistor! Hams of all generations have a hacker mindset, solving problems their own way, regardless of what the manual has to say. Continuing this pioneer spirit, the Ham Radio Community is here to support advancement of the hobby with a cybersecurity slant.
Everything we do today involves wireless communications of some sort, and a basic knowledge of how radio works is crucial. In the Ham Radio Community, you can learn hand-on with topics such as how to legally use a radio to send commands to a satellite, communicating around the globe when no other methods exist, and how to send and receive real-time location data without relying on any cellular networks. You can put your skills to the test by trying to find the hidden transmitters in the Ham Radio Fox Hunt contest, as well as transmitting memes over the airwaves to DEF CON attendees.
We provide license testing services for those looking to become licensed or upgrade their license class, as well as guidance on how to hack on the medium to achieve the best results and have the most fun!
Links:
**Mission**. ICS Village is a non-profit organization with the purpose of providing education and awareness of Industrial Control System security.
**Exhibits**. Interactive simulated ICS environments that provide safe yet realistic examples to preserve safe, secure, and reliable operations. We bring real components such as Programmable Logic Controllers (PLC), Human Machine Interfaces (HMI), Remote Telemetry Units (RTU), and actuators, to simulate a realistic environment throughout different industrial sectors. Visitors can connect their laptops to assess these ICS devices with common security scanners, network sniffers to sniff the industrial traffic, and more! We will also have space dedicated to Maritime technology as well as Escape Rooms ran by Idaho National Labs and CISA. In addition to talks, hands-on demos/hacking, and escape rooms we are collaborating with BioHacking Village to demonstrate how Industrial Control Systems are used in Health Care.
Links:
IoT Village advocates for advancing security in the Internet of Things (IoT) industry through bringing researchers and industry together. IoT Village hosts talks by expert security researchers, interactive hacking labs, live bug hunting in the latest IoT tech, and competitive IoT hacking contests, including our 4 time black badge DEF CON CTF. Over the years, IoT Village has served as a platform to showcase and uncover hundreds of new vulnerabilities, giving attendees from around the globe the opportunity to learn about the most innovative techniques to both hack and secure IoT. IoT Village is organized by security consulting and research firm, [Independent Security Evaluators (ISE)](https://www.ise.io/).
Links:
Want to tinker with locks and tools the likes of which you've only seen in movies featuring secret agents, daring heists, or covert entry teams?
Then come on by the Lockpick Village, run by The Open Organization Of Lockpickers (TOOOL), where you will have the opportunity to learn hands-on how the fundamental hardware of physical security operates and how it can be compromised.
The Lockpick Village is a physical security demonstration and participation area. Visitors can learn about the vulnerabilities of various locking devices, techniques used to exploit these vulnerabilities, and practice on locks of various levels of difficultly to try it themselves.
Experts will be on hand to demonstrate and plenty of trial locks, pick tools, and other devices will be available for you to handle. By exploring the faults and flaws in many popular lock designs, you can not only learn about the fun hobby of sport-picking, but also gain a much stronger knowledge about the best methods and practices for protecting your own property.
Links:
The Maritime Hacking Village (MHV) has set sail for LVCC to deliver the first and only immersive maritime hacking experience for you to learn what it takes to exploit and defend real-world maritime systems. Our mission is simple: we are creating a space for stakeholders to come together and navigate the changing tides in the maritime sector’s technological, geopolitical, and adversarial landscapes which demand ever-more-urgent collective action to address the systemic cybersecurity vulnerabilities in the systems which underpin global maritime defense and trade. Together we hack to facilitate the discovery and sharing of knowledge integral to the development of effective maritime cybersecurity policy, industry standards and regulations, vulnerability information sharing, cyber threat intelligence, and most importantly – a capable and trusted workforce and community-of-interest.
Why? Maritime infrastructure is the backbone of the global economy and order. Countries, companies, and militaries all use the sea for power projection and commerce, but no single stakeholder controls the implementation of policies and regulations. Stakeholders unanimously agree that from machines, to systems, to governance, the maritime domain is fundamentally insecure. Still, seemingly insurmountable access barriers are preventing the security community, and anyone else, from doing anything to help.
MHV has made it our purpose to eliminate these barriers – and to provide every human with the access and resources necessary to engage in maritime vulnerability research and cybersecurity innovation. Our village is a safe, shared space where the security community (elite hackers, trusted providers, and young talent alike) can develop and demonstrate their competence in attacking and defending real maritime systems – and where maritime industry stakeholders can engage with this community on neutral ground to grow their arsenals of knowledge, tools, trusted and capable providers, and fresh talent. We believe that this work together will create rising tides of awareness, information sharing, and innovation that will lift all ships and allow us to gradually secure the maritime sector.
Links:
Malware Village is dedicated to providing a safe and engaging environment for participants to learn and share knowledge about malware analysis. Our mission is to equip attendees with the skills, techniques, and historical context needed to understand, research, and combat malware. Participants will gain hands-on experience with real-world analysis techniques, guided by seasoned infosec professionals.
Beyond technical training, Malware Village fosters a strong community where researchers, enthusiasts, and professionals can connect. We welcome everyone—whether you're an artist creating malware-inspired art, a hardware researcher discovering unexpected connections to malware analysis, or a seasoned analyst reminiscing about early malware history. Even children can explore malware through Malmons (aka Malware Monsters by Lena Yu aka LambdaMamba), making cybersecurity education more accessible.
At its core, Malware Village is about uniting people—newcomers and experts alike—with a shared mission: understanding, analyzing, and defending against malware to protect society.
Links:
Come to the Payment Village to learn about payment technologies! Payments play a crucial role in our daily lives, yet many of us lack an understanding of how they work. Our mission is to educate and cultivate the next generation of payment security experts and to foster open discussions around payments. We want to raise the bar in payment security! We invite you to explore the history of payments and to learn how modern-day payments work.
The village is jam-packed with hands-on experiences and exciting challenges! Unsure of where to start? Register for one of our workshops to acquire new skills or attend a talk by one of our carefully chosen experts. Already a pro? Pick up a Payment Village credit card to take part in our contest! Looking for unique challenges? Take home all the money from our cash-grab machine or have a go at our scavenger hunt!
As if that is not enough, this year we have created the largest badge EVER at DEF CON, our vulnerable ATM badge. We are bringing ATM hacking to the masses; our badge simulates an ATM attack surfaces in a physical form factor you can carry with two hands! not a forklift truck.
Links:
The Packet Hacking Village at DEF CON provides a community learning experience for people of all skill levels, from absolute beginners to seasoned professionals. While DEF CON is made up of dozens of small community-of-interest villages, we are one of the largest and most well known. We host practical training, network forensics and analysis games, and the renowned Capture The Packet event, which has been a Black Badge contest over 10 times and draws world-class hackers from around the world. Our mission has always been simple: to teach people good internet safety practices, and to provide an atmosphere that encourages everyone to explore and learn.
We provide a welcoming environment for hackers of all skill levels and backgrounds to network, learn new things, and be active participants in DEF CON. Our famous “Wall of Sheep” provides a fun and interactive take on internet security and privacy, while our contests Packet Inspector, Packet Detective, and Capture The Packet serve as a zero-to-hero pathway for individuals to learn network security, packet analysis, and delve into advanced security topics. Every year we strive to bring something new and innovative to DEF CON, whether it’s never-seen-before talks or creative games to teach and test skills.
Links:
The DEF CON community understands that creating a safer digital society requires collaboration between security and policy experts. Policy @ DEF CON provides a space for representatives of all areas of security to come together to educate and engage each other.
Tech policy is being written as we speak and we believe that including diverse expert voices will improve outcomes and help to bridge gaps between technical and policy practitioners. Senior government officials, nonprofit and private sector experts, security researchers, hackers, academics and technologists from around the world all come together at Policy @ DEF CON.
Links:
Physical security is an important aspect to think about when considering securing your facility. The Physical Security Village provides an important opportunity to learn about real-world threats, hands-on mitigation techniques, and best practices for protecting assets. Our village brings together experts, practitioners, and enthusiasts to share knowledge through interactive demos, talks, and discussions. Whether you're new to physical security or a seasoned professional, you'll find valuable insights and practical skills.
Links:
Quantum Village Returns with our Year of Quantum Edition @ DEF CON 33!! Our theme this year is “Sense and Security” and we are bringing some amazing talks, workshops, demos, and hands-on activities to this year’s incredible Quantum Village! Come and find out how to hack quantum computers, learn more about quantum technologies, and meet the engineers and scientists who are building the machines that manipulate the quantum world. We also introduce the world’s first hackable, fully open sourced diamond-based quantum sensing platform - and we’ll be showing some of the amazing things it can do! We have quantum computers, quantum sensors, The OG Quantum CTF, quantum art (and artists), and all you need to prepare for the quantum future!
Links:
Recon Village is an Open Space with Talks, Live Demos, Workshops, Discussions, CTFs, etc., with a common focus on Reconnaissance. The core objective of this village is to spread awareness about the importance of reconnaissance and open-source intelligence (OSINT) and demonstrate how even a small piece of information about a target can cause catastrophic damage to individuals and organizations.
As recon is a vital phase for infosec as well as investigations, folks should have this skill set in their arsenal. People should check out Recon Village, as they get to learn novel point/recon techniques, play hands-on CTF, participate in Live Recon, and, most of all, have fun. At RV, we keep things simple, and the focus is on generating quality content using talks, workshops, CTF, live hacking, hackathons, and other hands-on activities, etc.
We also run fun and hands-on live competitions where participants learn while they play.
Links:
After 17 years of evolution, from the WiFi Village, to the Wireless Village, RF Hackers Sanctuary presents: The Radio Frequency Village at DEFCON 32. The Radio Frequency Village is an environment where people come to learn about the security of radio frequency (RF) transmissions, which includes wireless technology, applications of software defined radio (SDR), Bluetooth (BT), Zigbee, WiFi, Z-wave, Radio Frequency Identification (RFID), Infrared (IR) and other protocols within the usable RF spectrum. As a security community we have grown beyond WiFi, and even beyond Bluetooth and Zigbee. The RF Village includes talks on all manner of radio frequency command and control as well as communication systems. While everyone knows about the WiFi and Bluetooth attack surfaces, most of us rely on many additional technologies every day. RF Hackers Sanctuary is supported by a group of experts in the area of information security as it relates to RF technologies. RF Hackers Sanctuary’s common purpose is to provide an environment in which participants may explore these technologies with a focus on improving their skills through offense and defense. These learning environments are provided in the form of guest speakers, panels, and Radio Frequency Capture the Flag games, to promote learning on cutting edge topics as it relates to radio communications. We promise to still provide free WiFi.
Co-located with the RF Village is the RF Capture the Flag. Come for the talks, stay for the practice and the competition.
Who runs this thing?
RF Hackers Sanctuary is a group of all volunteers with expertise in radio security and various other related fields. We are the original creators of the WiFi Capture the Flag, Wireless Capture the Flag, and RF Capture the Flag. We are the original founders of the WiFi Village, Wireless Village, and RF Village. Often imitated, never duplicated.
Links:
The Red Team Village is focused on training the art of critical thinking, collaboration, and strategy in offensive security. The RTV brings together information security professionals to share new tactics and techniques in offensive security.
Links:
The Social Engineering Community is formed by a group of individuals who have a passion to enable people of all ages and backgrounds interested in Social Engineering with a venue to learn, discuss, and practice this craft. We plan to use this opportunity at DEF CON to present a community space that offers those elements through panels, research opportunities, and contests in order to act as a catalyst to foster discussion, advance the craft and create a space for individuals to expand their network. DEF CON attendees can either participate in these events, or they can watch the events unfold and learn about Social Engineering as an audience member. We plan to accomplish the above by bringing together passionate individuals to have a shared stake in building this community.
Links:
At Telecom Village, our mission is to cultivate critical and innovative thinking in telecom security, with a strong focus on 5G networks. We offer a structured learning approach that enables participants to:
Our goal is to bridge the gap between theory and real-world application, equipping participants with the expertise to navigate and counter emerging telecom security challenges effectively. Through guided research, hands-on learning, and continuous exploration, we foster a community of skilled professionals ready to tackle the evolving telecom landscape.
Links:"Tamper-evident" refers to a physical security technology that provides evidence of tampering (access, damage, repair, or replacement) to determine authenticity or integrity of a container or object(s). In practical terms, this can be a piece of tape that closes an envelope, a plastic detainer that secures a hasp, or an ink used to identify a legitimate document. Tamper-evident technologies are often confused with "tamper resistant" or "tamper proof" technologies which attempt to prevent tampering in the first place. Referred to individually as "seals," many tamper technologies are easy to destroy, but a destroyed (or missing) seal would provide evidence of tampering! The goal of the TEV is to teach attendees how these technologies work and how many can be tampered with without leaving evidence.

The [Voting Village](https://votingvillage.org) has been an annual event since 2017 that provides hands-on opportunities to understand and analyze voting system hardware and software. Before the Voting Village, ordinary technologists and citizens had no access to the systems that run our election infrastructure. As the only open environment that gives the public hands-on access to their election systems, it is a critical antidote to rampant misinformation about election security and provides an opportunity to strengthen these systems against malicious attacks. The Voting Village is brought to you by our 501(c)3 tax exempt not for profit organization, the Election Integrity Foundation, EIN: 83-4089169.
The Voting Village has been invited to testify to Congress several times about how to strengthen election infrastructure. Conversely, we have drawn fire from voting system manufacturers, prompting a bipartisan group of senators to co-sign a public letter defending the Voting Village against some of the largest voting machine companies in 2018.
Even between presidential election cycles, expanding the reach of the Voting Village and providing education about how our election systems work is critical to democracy.
Links:
DCTV is online! Jump on
dctv.defcon.org
for links to the DEF CON 33 live streams on YouTube and Twitch.
Get that DEF CON however works best for you.

As you’ve likely heard, attendees in the cash line are getting paper badges right now. This is due to a badge shipment delay. We’re sorry for the inconvenience. We will share updates as soon we have them, and we’ll do our best to make it right. Thanks for your understanding.
Stay in touch with DEF CON socials and Hacker Tracker for updates as soon as they arrive.

Greetings, luminous humans of DEF CON! Welcome to the week of DEF CON 33!
Make sure to join us Thursday from 7:30 to 10:30 at the Sahara Pool for the KEVOPS Sellout Pool Party! Refreshing pool, delicious tacos, and DEF CON DJ’s on the ones and twos. DEF CON badge required for entry.
See you there!

Registration for DEF CON workshops will open at precisely noon Pacific Daylight Time on July 15. It's a good idea to have your clicking device oiled up and sighted in - spaces get snapped up very quickly.
The full lineup is on the
Workshops Page
. Get your faves and alts all lined up for maximum efficiency.
It's happening, people. Feel free to get amped.

Who's speaking on the main stages at DEF CON
? What
DEF CON Workshops
are going to be available? Inquiring minds want to know!
Lucky day for you, curious netizens. The listings for both are live now on the #dc33 website. Familiarize yourself with the lineup, and make your plans accordingly.
Final stretch people. DEF CON positively LOOMS on the horizon!

Friendly reminder to all Workshops CFP submitters: Responses have gone out! If you don't see a response to your submission in your inbox, please check your spam folder.
Thanks to everyone who sent in a submission and congratulations to everyone that's been selected.
Less than two months until DEF CON 33! Time to start planning to make the most of your DEF CON experience.
One of the best parts of DEF CON is meeting other humans and bonding over shared interests. On the
Parties, Meetups and Events page
you'll find a shockingly comprehensive list of group hangs. Whether you're into Running or Ham Radio, Blanket Forts or Karaoke, we've got you covered.
Set aside some time for fun and connection. Your people are waiting.

We sense a disturbance in the force…
registration is open for DEF CON Training Las Vegas 2025
!
Whether you're a Rebel Red Teamer or a True Blue Defender, there is training for all, from any world in the galaxy!
Pack up your droids and join us in Vegas! Register today and take advantage of this opportunity to train with our Jedi Masters - uh, we mean instructors.

DC33 planning alert - The DEF CON room block at the Fontainebleau is sold out. The blocks at the Sahara and Venetian are filling up. To lock down your own deep DEF CON 33 discounts visit
defcon.org
for the reg links.
August will be here before you know it. Make sure you plan accordingly.
See you soon!

Attention independent authors! DEF CON 33 is offering a space for
book signings in the Vendor area
. If you've got a book that will appeal to the DEF CON Community, we encourage you to submit it for consideration.
Get your work (and yourself) in front of a vibrant, engaged community of enthusiastic readers.

Attention all scribes and tale-weavers of the DEF CON community - the DEF CON 33 Short Story Contest is open for business! It takes place entirely online - you can find the details at
https://forum.defcon.org/node/252691
.
The theme is Access Everywhere. In addition to literary glory, you can also win free human badges for DC33.
let's GO.

Friendly DEF CON reminder: the deadline for the DEF CON 33 Call for Papers , Call for Workshops and Call for Demo Labs is now less than a month away! Get your submissions in ahead of the mad rush at the May 1 deadline for maximum attention. We can't wait to see what you're working on.

DEF CON Training Las Vegas Registration is officially open! Expanded menu includes dozens of course options, new 4-day trainings and a $200 earlybird discount. Join us in August for DEF CON style hands-on technical training from our world-class trainers. Information and signup at training.defcon.org . Reserve your spot now!

Friendly reminder to #defcon people everywhere 🚨
The
open calls for DEF CON 33
Contests, Villages and Communities close March 15. If you've got a cool idea to propose, now is the time!
Fortune favors the bold. Let's GO.

"Access Everywhere."
This year we're thinking about how to make information and services available to everyone. Available wherever you are, whoever you are, and usable no matter how you need to connect.
Less walled gardens, more sunlight.
You can read the theme story and get some visual inspiration on the
DEF CON 33 Theme and Style Guide page
. You can get it in a
PDF on media.defcon.org
. Homework assignments to get you into the vibe coming soon.
We can't wait to see where you'll take it.
See you at DEF CON!

DEF CON 33 is building steam. Planning is in full swing. In fact, a glance at any nearby calendar will tell you we're already halfway there!
We know you need to plan, too. That's why we're opening up Early Bird Online Registration. For the go-getters who register early, weve got our lowest online price. And just like in years past, registering online guarantees your badge, no matter what the attendance numbers turn out to be.
Starting Wednesday you'll be able to hit up
shop.defcon.org
to get your ticket. Are you ready?
The Early Reg price is $540 ($520 +$20 processing fee.) Early Bird season ends May 23.
Regular Pricing is $560 ($540 + $20 processing) and is available until July 18.
Late Pricing is $580 ($560 +$20 processing) from July 19 to the close of Online Registration.
As always, online registration is not required. The cash-at-the-door price is just $500, and it comes with the bonus of our world-famous LineCon.
We're very excited about how DEF CON 33 is shaping up. We hope you are too.Past the halfway point, people. Let's GO.

The DEF CON 33 Call Season is now almost complete! The Call for Papers is LIVE. We're also ready to accept submissions for Demos, Workshops, and Policy. Things are well and truly underway. Time to breathe deep, gather your ideas and get busy proposing.
For the comprehensive list of open calls, visit
the DEF CON 33 Call Index
. Rules, guidance, deadlines – it's all there.
Participation is the cheat code that unlocks the secret DEF CON levels. We can't wait to see what you've got in mind.

The moment has arrived - the DEF CON 33 Call Season is officially afoot! Time to get thinking on how you want to participate. Whether you've got ideas to start a new Village, or have the tunes to rock the crowd after hours, the doors are open. There are a bunch of Calls you can peruse at leisure from Contests to Soundtrack to Vendors, and all the info you need to get started is on the
DEF CON 33 Call Index
.
Don't let your dreams be dreams! Make this the year your idea makes headlines at DEF CON.
DEF CON season is underway, people. Let's get after it.

DEF CON 33 CTF Qualifcations have a date! "Packet sorcerers, make room in your calendar for the official qualifier event for #defcon 33 CTF! Our esteemed colleagues at the Nautilus Institute are hard at work building the challenges - can you afford to do less?"
Further information available at
https://nautilus.institute
. The long season of preparation begins.

Another discounted room block for DEF CON 33 has dropped! This time it's at the ultra-swanky Fontainebleau, just a short walk from the LVCC.To book yourself into the Fontainebleau, you can call (833) 702-7272 between 6am to 10pm (PST) or use this link: https://book.passkey.com/go/DefCon2025FBLV . You can also reach the link from defcon.org.Maybe it's time to treat yourself. 2025 will be here before you know it.

Attention DEF CON educators ! The DEF CON Training 2025 Call for Trainers is live!
We're looking for unique, technical, and practical presentations from trainers with deep knowledge of their subject. If that's you, let's talk!
All the info you need to apply is at
training.defcon.org
.

Good news, everyone! We've already got some discounted room blocks you can use to lock down your lodgings for DEF CON 33.
DC33 doesn't kick off until August 7, 2025, but that's no reason to lollygag. If you're a high-octane go-getter you already know how good it feels to get those To-Do items checked off early. If not, this is far enough ahead to forget you booked and give yourself a nice surprise when there's one less thing to do at crunch time.
You can book at
the
Venetian
now and get the DC33 ball rolling. We'll keep you posted as additional options become available.
We're already 2 months closer to the next DEF CON. Be prepared.
What is DEF CON?
DEF CON is one of the oldest continuously running hacker conventions around, and also one of the largest.
How did DEF CON start?
Originally started in 1993, it was a meant to be a party for member of "Platinum Net", a Fido protocol based hacking network out of Canada. As the main U.S. hub I was helping the Platinum Net organizer (I forget his name) plan a closing party for all the member BBS systems and their users. He was going to shut down the network when his dad took a new job and had to move away. We talking about where we might hold it, when all of a sudden he left early and disappeared. I was just planning a party for a network that was shut down, except for my U.S. nodes. I decided what the hell, I'll invite the members of all the other networks my BBS (A Dark Tangent System) system was a part of including Cyber Crime International (CCI), Hit Net, Tired of Protection (ToP), and like 8 others I can't remember. Why not invite everyone on #hack? Good idea!
Where did the name come from?
The short answer is a combination of places. There as a SummerCon in the summer, a HoHoCon in the winter, a PumpCon during Halloween, etc. I didn't want any association with a time of year. If you are a Phreak, or just use your phone a lot you'll notes "DEF" is #3 on the phone. If you are into military lingo DEF CON is short for "Defense Condition." Now being a fan of the movie War Games I took note that the main character, David Lightman, lived in Seattle, as I do, and chose to nuke Las Vegas with W.O.P.R. when given the chance. Well I knew I was doing a con in Vegas, so it all just sort of worked out.
There are several resources that will give you an idea of what DEF CON is all about.
DEF CON Press: through the prism of the media
DEF CON Groups: Local groups that meet
DEF CON Media Server: DC 1 to the present, captured
Google: always a good research starting point
Just remember, DEF CON is what you make of it.
When and where is DEF CON?
DEF CON is generally in the last week of July or first week of August in Las Vegas. DEF CON 33 will be held August 7th through August 10th, 2025. Many people arrive a day early, and many stay a day later.
Isn't there a DEF CON FAQ already?
Yes, an unofficial one. It's quite humorous, sometimes informative, and DEF CON takes no responsibility for its content. It is archived here.
What are the rules of DEF CON?
Physical violence is prohibited. Harassment of any kind is prohibited. We don't support illegal drug use. Minors should be accompanied by their parent(s) or guardian(s). Please refrain from doing anything that might jeopardize the conference or attendees such as lighting your hair on fire or throwing lit road flares in elevators. DEF CON Goons are there to answer your questions and keep everything moving. Hotel security is there to watch over their property. Each has a different mission, and it is wise to not anger the hotel people. Please be aware that if you engage in illegal activities there is a large contingency of feds that attend DEF CON. Talking about how you are going to bomb the RNC convention in front of an FBI agent is a Career Limiting Move!
You can view the DEF CON Code of Conduct at https://defcon.org/html/links/dc-code-of-conduct.html.
Is DEF CON cancelled?
No.
What is there to do at DEF CON?
DEF CON is a unique experience for each con-goer. If you google around you'll find dozens of write-ups that will give you an idea of what people have experienced at DEF CON. Trust write-ups more than media articles about the con. Some people play capture the flag 24x7, while many people never touch a computer at DEF CON. Some people see every speech they can, while others miss all speeches. Other activities include contests, movie marathons, scavenger hunts, sleep deprivation, lock picking, warez trading, drunken parties, spot the fed contest, the official music events. Because DEF CON is what the attendees make of it, there are more events than even we are aware of. Half the fun is learning what happened at DEF CON after the fact!
I'm not a hacker, should I go to DEF CON?
Many people have different definitions of what is a ‘hacker’. I would recommend looking at previous years speeches, and write-ups from past attendees - this should give you a good idea if DEF CON is for you. This hacker FAQ might give you some insight into the matter as well. If you do not have any technical interests, DEF CON is probably not for you. Sure there is a lot of socializing you can do, but technology and hacking is the core of the con.
Do criminals go to DEF CON?
Yes. They also go to high school, college, work in your workplace, and the government. There are also lawyers, law enforcement agents, civil libertarians, cryptographers, and hackers in attendance. Ssshhh. Don't tell anyone.
What are Goons?
They are the staff at DEF CON. They have many roles including safety, speaker coordination, vendor room coordination, network operations, et cetera... Please try to be helpful to them if they make requests of you. If any goon tells you to move, please do so immediately as there may be safety issues they are attempting to address.
How can I help out or become a Goon?
The staff at DEF CON has grown organically. All positions have some degree of trust associated with them, so typically new goons are ‘inducted’ by friends of existing goons. There are many random points when goons need help and may ask people for help, generally for helping move stuff or other tasks that don't require high amounts of trust or unsupervised work. Just because you help out doesn't make you a goon. If you really want to be a goon, talk with one and see how much work they actually do (Hint: you may want to enjoy being at DEF CON, not working full-time at it). One year the network group got a new Goon when a networking engineer was needed, and he came to the rescue. The intent behind the goons is not to be elitist, but to have a network of trusted people who can help run the conference - please do not feel upset if you are not chosen to be a goon.
How can I help or participate?
DEF CON is not a spectator sport! Before the con, during, and after there are chances for you to get involved. Before the con you can read about the contests and maybe sign up for one like Capture the Flag. There are artwork contests for shirts and posters. You can practice your lock pick skills, or just get your laptop all locked down and ready to do battle. Organize your .mp3s. Check out the DEF CON Forums to see what other people are up to. If you want to create your own event, you can do that as well - you will not get official space or sanctions, but virtually every official event at DEF CON started out as an unofficial event.
I would love to see XYZ event, how do I make this happen?
Virtually all events at DEF CON were conceived by the attendees. The DEF CON forums are a great place for recruiting help for an event you want to put on, and making sure your efforts aren't being duplicated. If it doesn't require resources from DEF CON (space, namely) you generally don't have to ask anyone’s permission. Most events are unofficial until they've been going on for a couple of years. Please let us know if you have an idea for an event, we may help facilitate or promote it. Email [suggestions at DEF CON dot org] to keep us in the loop.
How can I speak at DEF CON?
You can submit a response to our CFP (opening soon). All entries are read and evaluated by a selection committee. We would love to have your submission. The call for papers usually opens in January and closes mid-May.
I'm press, how do I sign up, why can't I get in for free (I'm just doing my job)?
Please email press[at]defcon[d0t]org if you wish press credentials. Lots of people come to DEF CON and are doing their job; security professionals, federal agents, and the press. It wouldn't be fair to DEF CON attendees if we exempted one group from paying. If you are a major network and plan on doing a two minute piece showing all the people with blue hair, you probably shouldn't bother applying for a press pass - you won't get one. If you are a security writer or from a real publication please submit, and someone will respond with an answer.
I want to sell stuff, how do I do this?
If you want a space in our vendor area, you need to apply. Because of limited space and our attempt to have a diversity of vendors, you may not be able to get a booth. It is wise to think of staffing issues - if you are one person do you want to spend your entire time behind a vendors booth?
What are the different price rates?
Everyone pays the same: The government, the media, the ‘well known hackers’, the unknown script kiddies. The only discount is for Goons and speakers, who get to work without paying for the privilege.
How much is admission DEF CON, and do you take credit cards?
Online pricing at shop.defcon.org ( where you can pay with a credit card) is as follows:
The Early Reg price is $540 ($520 +$20 processing fee.) Early Bird season ends May 23.
Regular Pricing is $560 ($540 + $20 processing) and is available until July 18.
Late Pricing is $580 ($560 +$20 processing) from July 19 to the close of Online Registration.
As always, online registration is not required. The cash-at-the-door price is just $500, and it comes with the bonus of our world-famous LineCon.
Does my underage child need a badge?
Children under the age of 8 will not need to purchase a badge.
Can I get a discount on DEF CON badges?
DEF CON charges one price regardless of your social status or affiliation. Please know that we depend on attendee income to pay the costs of the conference and don't have sponsors to help defray the expenses.
We sometimes get requests for discounts [students, veterans, children], unfortunately we don't want to try and validate if you are a current student, look at your ID to determine your age, decode military discharge papers, etc.
If you really want to attend DEF CON for free then do something for the con.
You could:
Submit a CFP and be an accepted speaker or workshop instructor.
Work on a contest, event, or village.
Qualify for CTF/Contests that include entry.
Find a team to become a Goon newbie.
Contribute to content, or perform some entertainment.
I need a letter of invite for my visa application, how do I get that?
In most cases, DEF CON can send a signed letter of invite, usually within a few short business days once we have all the info. If you also require verification of housing, we can put you in touch with someone to help you get your hotel stay organized, let us know if you need that.
Along with your request, please email us the following to info(at)defcon(.)org
Name as is on passport:
Passport number:
Country of issue:
Date of issue:
Date of expiration:
Country of origin:
DEF CON is too expensive, how can I afford it?
Many people have made an art and science out of coming to DEF CON very cheaply. Here are a couple of tips.
Travel: Buy airfare in advance, go Greyhound, Carpool, hitch-hike. (Note: this may be dangerous and/or illegal.)
Lodging: Share rooms - some people have up to 10 people they share a room with, find a hotel cheaper than the one that the conference is scheduled at, stay up for three days, etc. (note: this can be hazardous to your health.)
Food: Pack food for your trip, go off site to find food, eat in your hotel rooms, and look for cheap Vegas food at Casinos. (Look for deals and specials that are trying to get you in the door to gamble.)
Booze: You don't need to drink. Brew your own and bring it. (It's been done.)
Entrance: Admission can be saved, mow some lawns. Try to go to another 4 day event for cheaper than this that offers so much. We have increased the fees slowly over the years, but also the amount and quality of events have increased.
Inevitably people will try to do some math and pretend that DT gets rich each DEF CON - they seem to lack the ability to subtract.
How many people typically attend DEF CON?
There have been roughly 25-28k attendees in the last few (pre-COVID) years of DEF CON. DEF CON 27 had a record showing with approximately 30,000.
Is there a network at DEF CON?
Why yes, DEF CON is FULLY network-enabled. Now that we've perfected the art of a stable hacker con network, we're ascending to a higher level - we're providing you a network that you feel SAFE in using! Since DEF CON 18 we're WPA2 encrypted over-the-air, with a direct trunk out to the Internet. No peer-to-peer, no sniffing, just straight to the net (and internal servers). We'll provide login credentials at Registration. We know the LTE airwaves will be saturated so we're putting our own cred on the line to give you a net that even we would put our own mobile phones on.
If you're feeling frisky, we'll still have the traditional "open" network for you - bring your laptop (we'd recommend a clean OS, fully patched--you know the procedure) because we don't police what happens on that net. Share & enjoy!
What is the age limit?
People have brought children to DEF CON - it is not recommended to do this unless you are going to constantly supervise them. It is generally an ‘adult’ atmosphere (language, booze, et cetera). If you've never been to DEF CON, you may want to refrain from bringing your children (unless they are demanding that you bring them). While there are no age limits, we have consistently cooperated with parents and/or private investigators who are looking for children that ‘ran away from home’ to go to DEF CON. You will have to be 21 to reserve a room.
What is a DEF CON "Black Badge"?
The Black Badge is the highest award DEF CON gives to contest winners of certain events. CTF winners sometimes earn these, as well as Hacker Jeopardy winners. The contests that are awarded Black Badges vary from year to year, and a Black Badge allows free entrance to DEF CON for life, potentially a value of thousands of dollars.
How can I get a hold of DT? I tried to mail him and haven't seen a response yet.
DT doesn't dislike you, isn't trying to hurt your feelings, and bears you no ill will. The fact is he gets an unmanageable load of mail continually. Mailing him again may elicit a response. Try mailing FAQ (at) DEFCON.ORG if you have a general question that isn't answered here or in the forums.
Is it hot in Vegas?
Yes. Bring sunscreen (high SPF), do not fall asleep near the pool (lest you wake up to sunburn), and do not walk far in the sun unless you are experienced in dealing with extreme heat. The sun is dangerous in Las Vegas. Sleeping in lawn chairs is a sure way to wake up to severe burns in the morning when that bright yellow thing scorches your skin. Drink plenty of water and liquids - remember that alcohol will dehydrate you.
What should I bring?
It depends on what you're going to do at DEF CON. This is discussed in quite some depth on the unofficial DC FAQ, as well as a thread in the DC Forums. You may want to bring fancy (or outrageously silly) clothes for the official Music events, on Friday and Saturday nights, where everyone shows off nifty attire.
How much do rooms cost, and how do I reserve a room?
Currently we have room blocks at Venetian, and Sahara
Check the the DEF CON 33 venue page periodically for more as we add them
How much is internet access?
We are looking into this. Free (and possibly more dangerous) internet access is available in the convention area.
Will the hotels broadcast the speeches on their cable system?
DEF CON TV has succcessfully streamed all tracks to all the hotels in the past, and a couple of tracks out to the internet, for several years now. We are navigating a new venue and new hotels, so stay tuned. If we can, we probably will!
Will we have DEF CON branded poker chips?
You will have to attend DEF CON to find out.
Will conference attendees have entire floors of hotel rooms to themselves?
Probably not. Hotels have been very cooperative in attempting to centralize the DEF CON attendees, for their convenience and ours, but there will be non-DEF CON attendees in hotel rooms next to us.
This FAQ didn't answer my questions, or was unclear, how can I get further information?
Check out the DEF CON Forums to ask follow up questions.
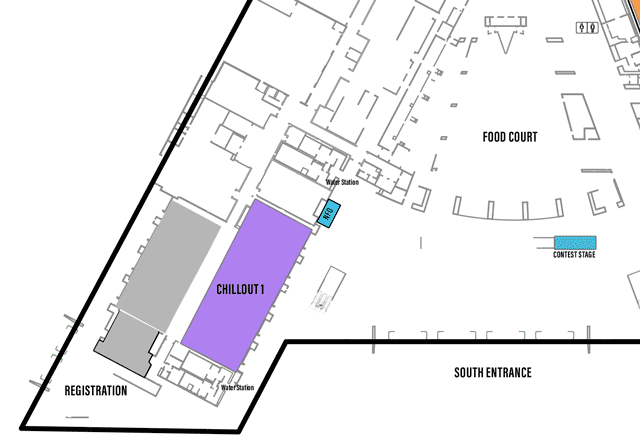
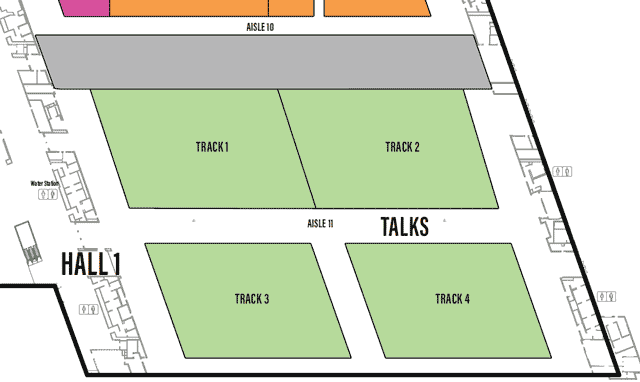
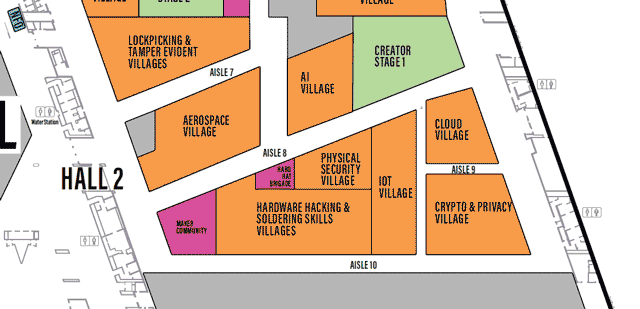
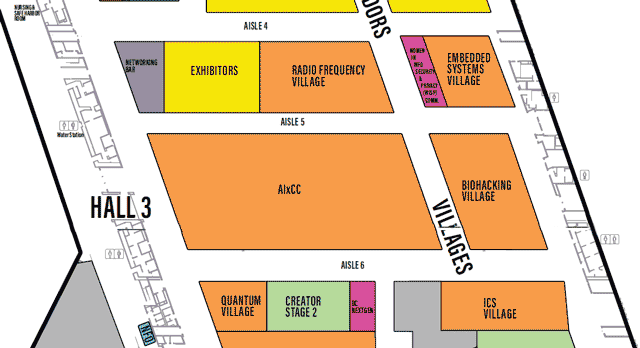
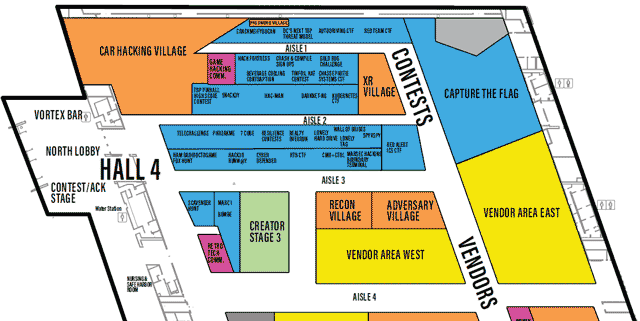
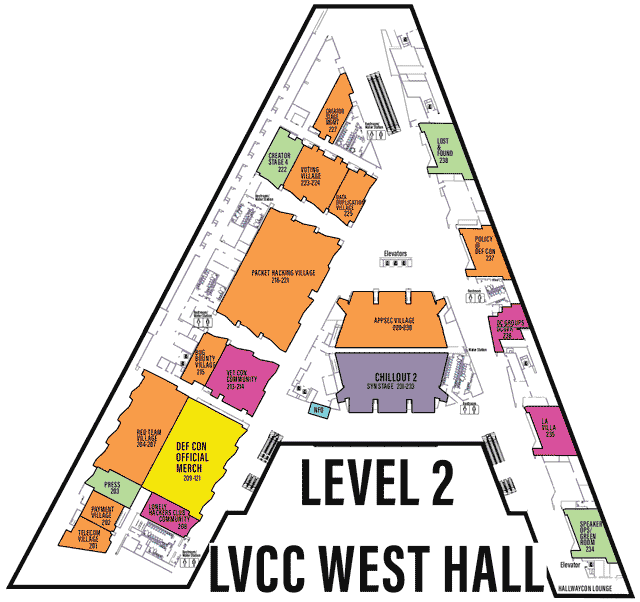
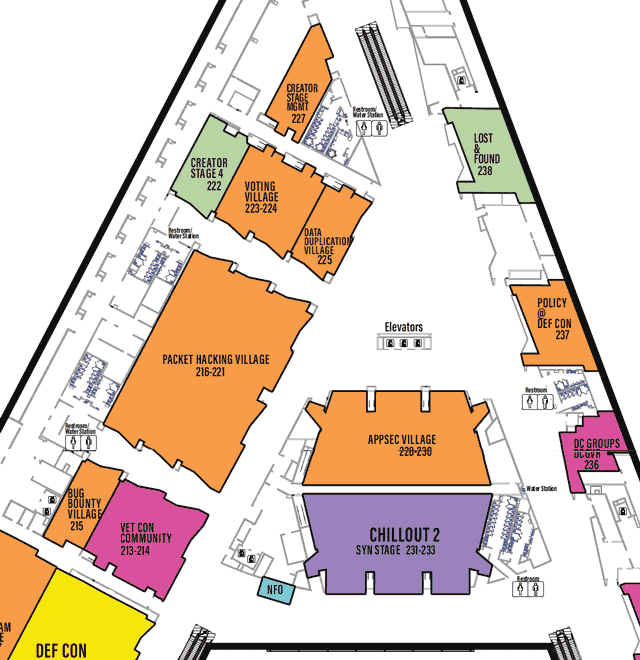
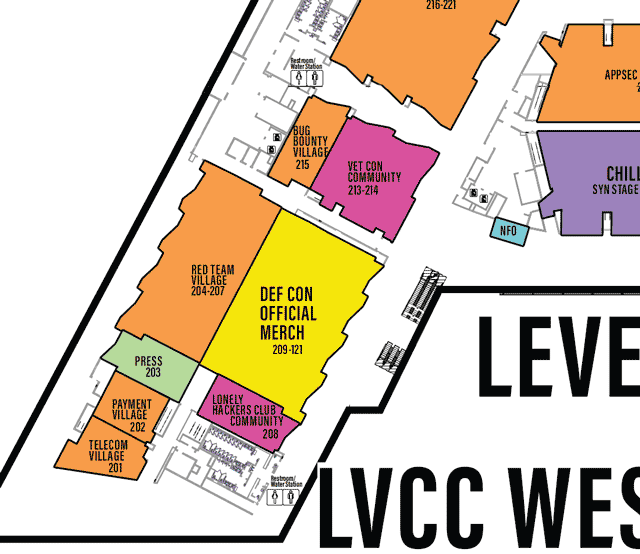
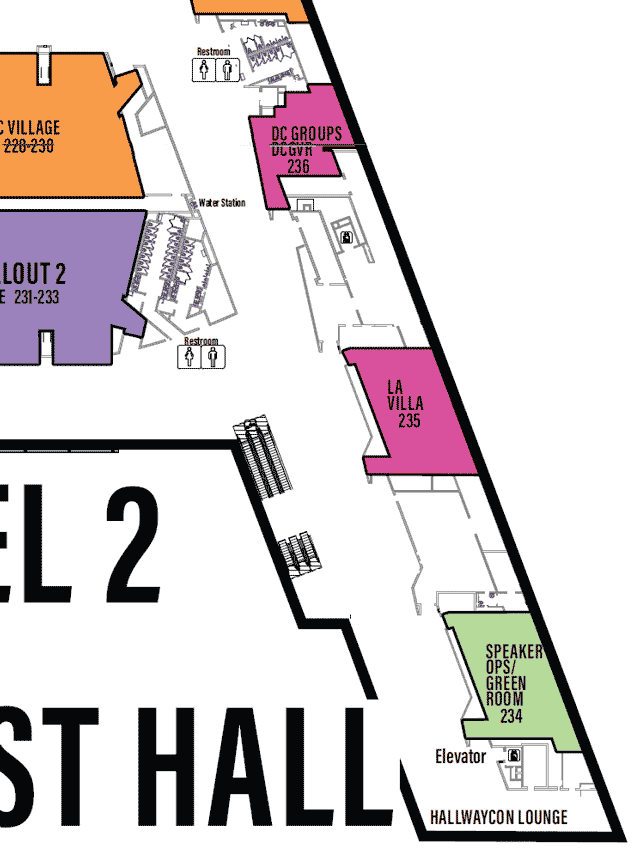
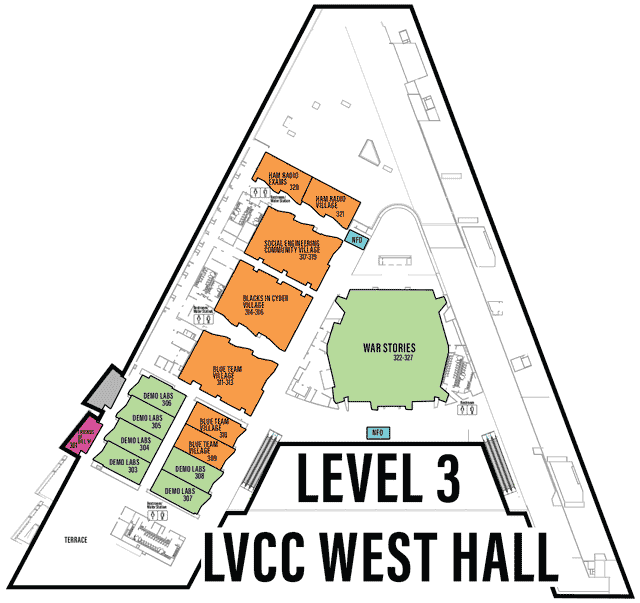
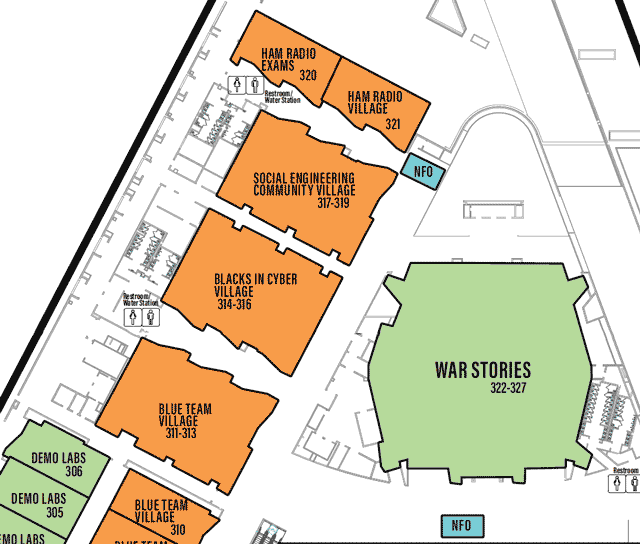
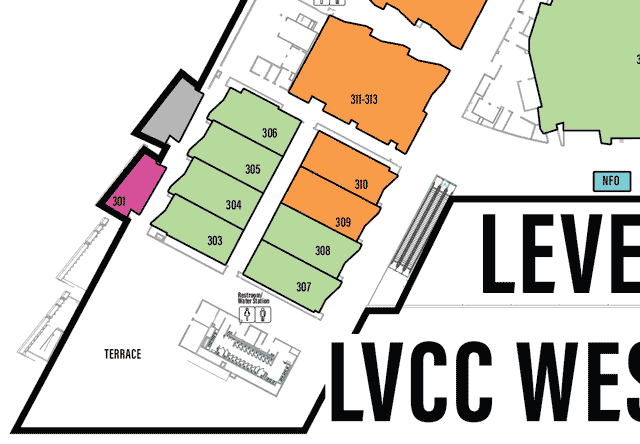
Each Village, as it’s name may imply, specializes in a topic or aspect of security or computers.
One Page All Villages list with descriptions
defcon.org Villages page
You may need to scroll to the right to see all info
Various contests, some lasting all 4 days of DEF CON, some short time on stage
One Page All Contests list with descriptions
defcon.org Contests page
You may need to scroll to the right to see all info
|
? Cube Contest Info |
.ssh/ Social Scavenger Hunt Contest Info |
|
[CANCELED] Hacking Boundary Ship Terminal Contest Info |
$$$$$_<CAPTURE_THE_COIN>_$$$$$ Contest Info |
|
$unL1ght Sh4d0w5 Contest Info |
5N4CK3Y Contest Info |
|
Adversary Wars CTF Contest Info |
AI Art Battle Contest Info |
|
Aw, man…pages! Contest Info |
Band Camp: Hacker My Music Contest Info |
|
Battle of the Bots: Vishing Edition Contest Info |
Betting on Your Digital Rights: 4th Annual EFF Benefit Poker Tournament at DEF CON 33 Contest Info |
|
Beverage Cooling Contraption Contest Contest Info |
Blacks In Cybersecurity Village Capture The Flag Competition Contest Info |
|
Blue Team Village CTF Contest Info |
Bug Bounty Village CTF Contest Info |
|
Call Center Village Contest Contest Info |
Can it Ham? Contest Info |
|
Capture The Packet Contest Info |
Car Hacking Village Capture the Flag (CTF) Contest Info |
|
Cloud Village CTF Contest Info |
CMD+CTRL Cloud Cyber Range Contest Info |
|
Code Breaker Challenge Contest Info |
Code CRIMSON: Healthcare in Trauma Contest Info |
|
Creative Writing Short Story Contest Contest Info |
Cryptocurrency Challenge Contest Info |
|
Cyber Defender – The Game Contest Info |
Cyber Wargames Contest Info |
|
Cycle Override Contest Info |
Darknet-NG Contest Info |
|
DARPA’s Artificial Intelligence Cyber Challenge (AIxCC) Contest Info |
DC Sticker Design Contest Contest Info |
|
DC’s Next Top Threat Model Contest Info |
DEF CON Beard and Mustache Contest Contest Info |
|
DEF CON CTF Contest Info |
DEF CON MUD Contest Info |
|
DEF CON Scavenger Hunt Contest Info |
Dozier Drill Lockpicking Challenge Contest Info |
|
Dungeons@Defcon Contest Info |
EFF Tech Trivia Contest Info |
|
Embedded CTF Contest Info |
Feet Feud (Hacker Family Feud) Contest Info |
|
GenSec CTF Contest Info |
Hac-Man Contest Info |
|
Hack3r Runw@y Contest Contest Info |
Hacker Jeopardy Contest Info |
|
Hardware Hacking Village CTF Contest Info |
HardWired Contest Info |
|
HTB CTF: Data Dystopia Contest Info |
ICS Village CTF Contest Info |
|
Kubernetes CTF Contest Info |
Octopus Game 4: The Order of the White Tentacle Contest Info |
|
Password Village Contest Contest Info |
Phish Stories Contest Info |
|
PhreakMe Contest Info |
Pinball High Score Contest Contest Info |
|
PROJECT ACCESS: A Fox Hunt in the Shadows Contest Info |
Pub Quiz at DEF CON Contest Info |
|
Radio Frequency Capture the Flag Contest Info |
Raitlin’s Challenge presented by the Illuminati Party® Contest Info |
|
REALI7Y OVERRUN Contest Info |
Red Alert ICS CTF Contest Info |
|
Red Team Village CTF Contest Info |
Scambait Village Contest Contest Info |
|
Silk’s Roadhouse Contest Info |
Social Engineering Community Vishing Competition (SECVC) Contest Info |
|
spyVspy Contest Info |
Taskmooster Contest Info |
|
TeleChallenge Contest Info |
The Gold Bug Contest Info |
|
The Pwnie Awards Contest Info |
Tin Foil Hat Contest Contest Info |
|
venator aurum Contest Info |
warl0ck gam3z CTF Contest Info |
|
Whose Slide Is It Anyway? Contest Info |
Brief demonstrations for people to show off their project.
One Page All Demolabs list with descriptions
defcon.org DemoLabs page
You may need to scroll to the right to see all info
|
AIMaL – Artificially Intelligent Malware Launcher Demolabs Info |
|
AirBleed – Covert Bluetooth Plist Payload Injection Demolabs Info |
|
Angry Magpie – DLP Bypass Simulator Demolabs Info |
|
Attack Flow and Root Cause Discovery – No LLMs, No Queries, Just Explainable ML Demolabs Info |
|
Audience Picked By Popular Demand Demo Lab – TheTimeMachine Demolabs Info |
|
Audience Picked By Popular Demand Demo Lab Demolabs Info |
|
Beaconator C2 Framework Demolabs Info |
|
Blackdagger – Cyber Workflow Automation Framework Demolabs Info |
|
BOAZ – A Multilayered Approach to AV/EDR Evasion Engineering Demolabs Info |
|
C4 – Cross Compatible Command and Control Demolabs Info |
|
Caldera for OT – Oops! All Software Demolabs Info |
|
Copycat – Identity Stealer Extension Demolabs Info |
|
Cryptosploit Demolabs Info |
|
DVBE – Damn Vulnerable Browser Extension Demolabs Info |
|
Dyna – Automating the OWASP MASTG with Offensive Android Tactics Demolabs Info |
|
Empire 6.0 Demolabs Info |
|
EntraGoat – A Deliberately Vulnerable Entra ID Environment Demolabs Info |
|
FLARE-VM Demolabs Info |
|
Garuda Threat Hunting Framework Demolabs Info |
|
GlytchC2 – Command Execution and Data Exfiltration of Any Kind Through Live Streaming Platforms Demolabs Info |
|
Have I Been Ransomed? Demolabs Info |
|
Lex Sleuther Demolabs Info |
|
Messenger – Proxies Here There and Everywhere Demolabs Info |
|
Metasploit’s Latest Attack Capability and Workflow Improvements Demolabs Info |
|
MPIT – Matrix Prompt Injection Tool and ShinoLLMApps Demolabs Info |
|
nRootTag – Exploiting Find My and Transforming Computers Into Unauthorized Trackers Demolabs Info |
|
OAuthSeeker Demolabs Info |
|
PAPRa Demolabs Info |
|
PatchLeaks Demolabs Info |
|
promptmap2 Demolabs Info |
|
RETCON – Reticulum Embedded Turnkey Connection Operating Node Demolabs Info |
|
RETINA – Realtime Electronic Threat and Intrusion Neutralization Apparatus Demolabs Info |
|
rev.ng Decompiler Demolabs Info |
|
Robin – The Archaeologist of the Dark Web Demolabs Info |
|
SAMLSmith Demolabs Info |
|
Spotter – Universal Kubernetes Security Scanner and Policy Enforcer Demolabs Info |
|
Tengu Marauder v2 Demolabs Info |
|
TheTimeMachine Demolabs Info |
|
Unmanned Wireless Penetration Testing Device Demolabs Info |
|
WarHead Demolabs Info |
Longer, more detailed, hands on, lasting half a day.
These have limited seating. These will fill up VERY quickly!
One Page All Workshops list with descriptions
defcon.org Workshops page
You may need to scroll to the right to see all info
|
Sold Out – 64-bit Intel Assembly Language Programming for Hackers Workshop Info |
|
Sold Out – Accelerating Malware Analysis with WinDbg Time Travel Debugging Workshop Info |
|
Sold Out – Advanced Ghidra Scripting & Automation Workshop Info |
|
Sold Out – Analyzing and Creating Windows Shellcode for Hackers Workshop Info |
|
Sold Out – Cloud Forensics Workshop: Smart Grid Edition Workshop Info |
|
Sold Out – Contextualizing alerts with relevant logs and events without queries or LLMs Workshop Info |
|
Sold Out – Creating malicious functional app on Android Workshop Info |
|
Sold Out – Deep-dive into modern network fingerprinting Workshop Info |
|
Sold Out – Defeating Malware Evasion: Techniques and Countermeasures Workshop Info |
|
Sold Out – Disrupting Digital Dataflows: A 101 on how 2 detect, analyze, & disrupt digital systems by reverse engineering real-world Electronic Warfare techniques from Ukraine at the hardware level Workshop Info |
|
Sold Out – Dive into Windows Library Loading Workshop Info |
|
Sold Out – DIY Malware Emulation: Build It, Break It, Detect It Workshop Info |
|
Sold Out – Effectively Detecting Modern Malware with Volatility 3 Workshop Info |
|
Sold Out – Eliminating Bug Classes at Scale: Leveraging Browser Features for Proactive Defense Workshop Info |
|
Sold Out – EMMC BGA Secrets, hack bga memory, no reballing necessary: Learn how to safely remove EMMC memory modules, hack them and then reinstall, without the difficult process of trying to reball the BGA. Workshop Info |
|
Sold Out – Fine Tune your personal LLM assistant to Secure coding Workshop Info |
|
Sold Out – Fortifying AI: Hands-On Training in Adversarial Attacks and Defense of AI Systems Workshop Info |
|
Sold Out – From Prompt to Protection: A Practical Guide to Building and Securing Generative AI Applications Workshop Info |
|
Sold Out – Hacker VPN Workshop Info |
|
Sold Out – Hacking the connected plant: AI edition! Workshop Info |
|
Sold Out – Hacking The Metal: Into the GPU Workshop Info |
|
Sold Out – Hands-on IoT firmware extraction and flash forensics Workshop Info |
|
Sold Out – Hands-on Kubernetes Attack & Defense Masterclass Workshop Info |
|
Sold Out – Hands-On Threat Hunting with Wireshark Workshop Info |
|
Sold Out – Inside the Threat: Designing and Deploying Malicious Browser Extensions to Understand Their Risk Workshop Info |
|
Sold Out – Introduction to Cryptographic Attacks Workshop Info |
|
Sold Out – K8sploitation: Hacking Kubernetes the Fun Way Workshop Info |
|
Sold Out – Learning to Hack Bluetooth Low Energy with BLE CTF Workshop Info |
|
Sold Out – Medical Device Hacking: 201 Workshop Info |
|
Sold Out – Obfuscation Reloaded: Modern Techniques for Evading Detection Workshop Info |
|
Sold Out – Open Source Malware 101 – Everything you always wanted to know about npm malware (and more) Workshop Info |
|
Sold Out – Pen-testing Cloud REST APIs Workshop Info |
|
Sold Out – PLC Playground: Hands-On Industrial Control Systems Attacks Workshop Info |
|
Sold Out – Practical YARA: Crafting Custom Rules for Targeted Malware Defense Workshop Info |
|
Sold Out – Provably exfiltrating data by breaking TLS in the right ways Workshop Info |
|
Sold Out – Putting EDRs in Their Place: Killing and Silencing EDR Agents Workshop Info |
|
Sold Out – Reach the Nirvana Workshop Info |
|
Sold Out – SnowGoat: Exposing Hidden Security Risks and Leaking Data Like a Threat Actor Workshop Info |
|
Sold Out – Whitebox Web Exploit Dev (WWED) Workshop Info |
|
Sold Out – Wi-Fi-So-Serious Workshop Info |
2 day training sessions on the Mon and Tue after DEF CON. There will be an additional cost for these.
One Page All Paid Training list with descriptions
DEF CON 33 Training Signup Pages
You may need to scroll to the right to see all info
|
A Complete Practical Approach to Malware Analysis & Threat Hunting Using Memory Forensics
Training Info |
|
A Practical Approach to Breaking & Pwning Kubernetes Clusters
Training Info |
|
Active Directory Attacks for Red and Blue Teams – Advanced Edition
Training Info |
|
Advanced Cloud Incident Response in Azure and Microsoft 365
Training Info |
|
Adversarial Thinking: The Art of Dangerous Ideas
Training Info |
|
AI SecureOps: Attacking & Defending AI Applications and Services
Training Info |
|
Attack and Defend Software Supply Chain
Training Info |
|
Attacking & Securing CI/CD Pipeline Certification (ASCPC) by White Knight Labs
Training Info |
|
Azure Cloud Attacks for Red & Blue Teams – Beginner Edition
Training Info |
|
Beginner’s Guide to Attacks and Defenses
Training Info |
|
BRIDGING THE GAP – An Introduction to IoT Security from Serial to Bluetooth
Training Info |
|
Deep Dive into Fuzzing
Training Info |
|
Dodging the EDR bullet: A Training on Malware Stealth Tactics
Training Info |
|
Everyday Ghidra: Practical Windows Reverse Engineering
Training Info |
|
Full-Stack Pentesting Laboratory: 100% Hands-On + Lifetime LAB Access
Training Info |
|
Hack the Connected Plant!
Training Info |
|
Hacking Cryptography: Attacks, Tools, and Techniques
Training Info |
|
Hacking Modern Web Apps: Master the Future of Attack Vectors
Training Info |
|
Hands-on Car Hacking & Automotive Cybersecurity
Training Info |
|
Harnessing LLMs for Application Security
Training Info |
|
Hunting for Hackers by Deloitte
Training Info |
|
Influence Operations: Tactics, Defense, and Exploitation
Training Info |
|
Loudmouth Security – Offensive IoT Exploitation
Training Info |
|
Medical Device Penetration Testing
Training Info |
|
Offensive Cyber Security Operations: Mastering Breach and Adversarial Attack Simulation Engagements
Training Info |
|
Offensive Development Practitioner Certification (On-Site) by White Knight Labs
Training Info |
|
RFID and Electronic Physical Access Control System Hacking
Training Info |
|
Simulated Adversary: Tactics & Tools Training
Training Info |
|
SOC 101 – SOC 1 Analyst Bootcamp
Training Info |
|
Software Defined Radios 101
Training Info |
|
Solving Modern Cybersecurity Problems with AI
Training Info |
|
Windows Payload Development: EDR Evasion and Initial Access Tradecraft
Training Info |
Various Parties, Gatherings, and Events
One Page All Parties, Gatherings, Events list with descriptions
defcon.org Parties, Meetups, and Events page
You may need to scroll to the right to see all info
|
+61: the Australian Embassy Event Info |
Arcade Party Event Info |
|
BlanketFort Con Event Info |
Book Signing – Adversary Emulation with MITRE ATT&CK – Drinor Selmanaj Event Info |
|
Book Signing – Alex Matrosov/No Starch Press Event Info |
Book Signing – Alfie Champion/No Starch Press Event Info |
|
Book Signing – Breaking IN: A Practical Guide To Starting a Career In Information Security Cybersecurity Essentials For Startups : A Practical Guide – Ayman Elsawah Event Info |
Book Signing – Casey Erdman/No Starch Press Event Info |
|
Book Signing – Corey Ball/No Starch Press Event Info |
Book Signing – Cyber Calendar 2026 – Chris DeCarmen/Squared Away LLC Event Info |
|
Book Signing – Daniel Reilly/No Starch Press Event Info |
Book Signing – Eugene Lim/ No Starch Press Event Info |
|
Book Signing – Firewalls Don’t Stop Dragons: A Step-by-Step Guide to Computer Security and Privacy for Non-Techies (5th ed) – Carey Parker Event Info |
Book Signing – Fotis Chantizis/ No Starch Press Event Info |
|
Book Signing – Future of Hacking: The Rise of Cybercrime and the Fight to Keep Us Safe – Laura S. Scherling, EdD / Bloomsbury Event Info |
Book Signing – Ghost Hacker : How to hack human spirit – Jun Kawasaki Event Info |
|
Book Signing – Hunter Scott/No Starch Press Event Info |
Book Signing – Jason Andress/ No Starch Press Event Info |
|
Book Signing – Jon DiMaggio/ No Starch Press Event Info |
Book Signing – JP Ausmasson/No Starch Press Event Info |
|
Book Signing – Kara Nance/No Starch Press Event Info |
Book Signing – Kurtis Minder Event Info |
|
Book Signing – Kyle Cucci/No Starch Press Event Info |
Book Signing – Lindsay Kay / No Strach Press Event Info |
|
Book Signing – Micah Lee/ No Starch Press Event Info |
Book Signing – Nick Aleks/No Starch Press Event Info |
|
Book Signing – Patrick Wardle/ No Starch Press Event Info |
Book Signing – Paulino Calderon/No Starch Press Event Info |
|
Book Signing – Philip Dursey/No Starch Press Event Info |
Book Signing – Phrack / No Starch Press Event Info |
|
Book Signing – Practical Lock Picking; Keys to the Kingdom – Deviant Ollam/Red Team Tools Event Info |
Book Signing – Supply Chain Software Security-AI, IoT and Application Security – Aamiruddin Syed/Apres Media LLC Event Info |
|
Book Signing – The Browser Security Field Manual Adeline – Audrey Adeline Event Info |
Book Signing – The Hacker Mindset: A 5-Step Methodology for Cracking the System and Achieving Your Dreams – Garrett Gee/Hacker Warehouse Event Info |
|
Book Signing – Travis Goodspeed/No Starch Press Event Info |
Call Center Village Party Event Info |
|
Conference Planners Meetup Event Info |
Cyberdelia Rave Event Info |
|
Darknet Diaries x DCG Meet up Event Info |
Day of the Dead Hacker Party Event Info |
|
DC Book Club Discussion Event Info |
DC NextGen Event Info |
|
DC404/DC678/DC770/DC470 (Atlanta Metro) Meetup Event Info |
DC702 Meetup Event Info |
|
DCG312 Meetup: Windy City Hackers Take Vegas Event Info |
DEF CON Holland Group Presents:
Drinking with the Dutch Event Info |
|
Defcon.run Event Info |
Free Ham Radio Exams Event Info |
|
Friends of Bill W Event Info |
GOTHCON Event Info |
|
Hacker Karaoke Event Info |
Human Registration Open Event Info |
|
IoT Village: 10 Years. 1,000 Devices. Infinite Vulns. (IoT Village 10th Birthday Party) Event Info |
Jack Rhysider, Ray [REDACTED] and more 1337 hackers! DXNextGen Meet and Greet Event Info |
|
Lawyers Meet Event Info |
Linecon Event Info |
|
Lost & Found Event Info |
Merch (formerly swag) Area Open — README Event Info |
|
Movie Night Event Info |
Music Set / Entertainment (Chillout Stage, Friday) Event Info |
|
Music Set / Entertainment (Chillout Stage, Saturday) Event Info |
Music Set / Entertainment (Chillout Stage, Thursday) Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Packet Hacking Village Music Event Info |
Packet Hacking Village Music Event Info |
|
Policy @ DEF CON Mixer Event Info |
Queercon Mixer Event Info |
|
Spades Tournament & Game Night Social Event Info |
Sticker Swap at DEF CON 33 Event Info |
|
The DEF CON Pool Party Event Info |
The Illuminati Party Event Info |
|
The Jasmine Dragon Event Info |
The KEVOPS Sellout Pool Party Event Info |
|
The Unofficial DEF CON Shoot Event Info |
Toxic BBQ Event Info |
|
Um, ACKtually… Event Info |
VETCON 2025 Party Event Info |
|
Walking Tour Groups Event Info |
WISP + Blue Team Village Movie Night and Mixer Event Info |
|
Women, gender non-conforming and non-binary meetup with The Diana Initiative Event Info |
List by name of the Vendors that will be in the Vendor area at DEF CON 33
One Page All Vendors list with descriptions
defcon.org Vendors page
|
Arts and Ent. Vendor Info |
Cryptocurrency Advocate Vendor Info |
|
deepnet LLC Vendor Info |
Electronic Cats Vendor Info |
|
Electronic Frontier Foundation (EFF) Vendor Info |
EXPLIoT Vendor Info |
|
FREE WiLi – Intrepid Control Systems Inc Vendor Info |
HackerBoxes Vendor Info |
|
HackerWarehouse Vendor Info |
Hak5 LLC Vendor Info |
|
iFixit Vendor Info |
Keyport Vendor Info |
|
Killchainz Clothing Vendor Info |
M2 Powered Partners LLC Vendor Info |
|
Mar Williams Vendor Info |
Midwest Gadgets LLC Vendor Info |
|
Miscreants, LLC Vendor Info |
No Starch Press, Inc Vendor Info |
|
Nuand LLC Vendor Info |
Octopwn GmbH Vendor Info |
|
PhysSec Education Vendor Info |
Rabbit-Labs Vendor Info |
|
Red Team Tools Vendor Info |
REKCAH Publishing Vendor Info |
|
Rogue’s Roost, LLC Vendor Info |
Rokland LLC Vendor Info |
|
Salty Security Vendor Info |
Shadowvex Industries Vendor Info |
|
SOK Vendor Info |
Sparrows Manufacturing Co Vendor Info |
|
The Calyx Institute Vendor Info |
The Open Organisation of Lockpickers (TOOOL) Vendor Info |
|
The Tor Project, Inc. Vendor Info |
Women in Security and Privacy Vendor Info |
|
Xcape, Inc. Vendor Info |
List by name of the Exhibitors that will be in the Exhibitor area at DEF CON 33
One Page All Exhibitors list with descriptions
defcon.org Exhibitors page
You may need to scroll to the right to see all info
|
Altered Security Exhibitor Info |
Authentik Exhibitor Info |
|
Black Hills Exhibitor Info |
Bugcrowd Exhibitor Info |
|
Capitol Technology University Exhibitor Info |
Formal Exhibitor Info |
|
Hack The Box Exhibitor Info |
Promptfoo Exhibitor Info |
|
The SecOps Group Exhibitor Info |
Triad Secure Exhibitor Info |
|
US Army xTech Exhibitor Info |
A group of people with common interests, but don’t qualify as a Village, is a Community,
One Page All Communities list with descriptions
defcon.org Communities page
You may need to scroll to the right to see all info
|
.edu Community
Community Info |
Badgelife
Community Info |
|
BBWIC Foundation
Community Info |
Code Breaker
Community Info |
|
Cryptocurrency Community
Community Info |
DC Maker’s Community
Community Info |
|
DC NextGen
Community Info |
DDoS Community
Community Info |
|
DEF CON Academy
Community Info |
DEF CON Groups (DCG)
Community Info |
|
DEF CON Groups VR (DCGVR)
Community Info |
Friends of Bill W
Community Info |
|
Hackers With Disabilities (HDA)
Community Info |
Hackers.town
Community Info |
|
Hard Hat Brigade
Community Info |
Illumicon
Community Info |
|
La Villa
Community Info |
Lonely Hackers Club
Community Info |
|
Loong Community
Community Info |
Memorial Chamber
Community Info |
|
Mobile Hacking Community
Community Info |
Nix Vegas Community
Community Info |
|
NMDP (formerly Be The Match)
Community Info |
Noob Community
Community Info |
|
Operating Systems Community
Community Info |
OWASP
Community Info |
|
Queercon Community Lounge
Community Info |
Retro Tech Community
Community Info |
|
The Diana Initiative
Community Info |
The Diana Initiative’s Quiet Room
Community Info |
|
VETCON
Community Info |
Women in Security and Privacy (WISP)
Community Info |